Latest News
Hacktivist Attacks Have Fallen 95% Since 2015
The number of publicly disclosed hacktivist attacks has dropped by 95% between 2015 and 2018 thanks to the relative decline
Stack Overflow Breached – Hackers Accessed Stack Overflow’s Production Systems
Stack Overflow, a question & answer based site for professional and programmers founded in 2008 reported a security breach. The
XSS Flaw in WordPress Live Chat Plugin Lets Attackers Compromise WP Sites
A vulnerability in the Live Chat Support plugin for WordPress could be exploited by attackers to inject malicious scripts in
WhatsApp Will Never Be Secure – Telegram Founder Attack Facebook Owned WhatsApp
“WhatsApp Will Never be Safe” !! Telegram Founder Pavel Durov Attack Facebook Owned WhatsApp after the recent incident, in which,
Hacker Group Behind GozNym Banking Malware Dismantled by International Authorities that Stolen $100 Million
International law enforcement operation brings down a globally operated and well-organized cybercrime network behind GozNym banking malware responsible for stealing
Past, Present, and Future of the Dark Web
Which is the difference between the Deep Web and Dark Web? Considerations about past, present, and future of the Dark
Google ‘0Day In the Wild’ Project Tracks Zero-Days Exploited in the Wild
White hat hackers at Google Project Zero are tracking cyber attacks exploiting zero-days before the vendor released security fixes. Experts
Critical Vulnerabilities in Cisco Products
A high-risk vulnerability in Cisco‘s secure boot process was disclosed earlier this week by Cisco and Red Balloon Security and
Supply Chain Attack Hits Best of the Web Website
The website Best of the Web, whose purpose is to assure site visitors that their user data is safe and
Microsoft Renewed its Attack Surface Analyzer, Version 2.0 is Online
Microsoft has renewed its Attack Surface Analyzer tool to take advantage of modern, cross-platform technologies. The first version of the
RCE Bug in Microsoft RDP Protocol Let Hackers Perform WannaCry Level Attack on 3 Million Vulnerable Endpoints
A critical remote execution vulnerability in Microsoft remote desktop services enables let attackers compromise the vulnerable system with WannaCry level
The Stealthy Email Stealer in the TA505 Hacker Group’s Arsenal
Experts at Yoroi-Cybaze Z-Lab observed a spike in attacks against the banking sector and spotted a new email stealer used
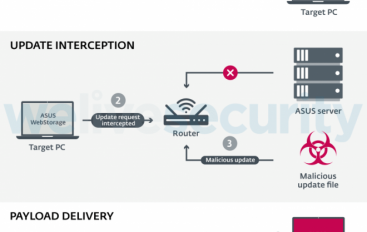
BlackTech Espionage Group Exploited ASUS Update Process to Deliver Plead Backdoor
The BlackTech cyber-espionage group exploited the ASUS update process for WebStorage application to deliver the Plead backdoor. The cyber espionage
More than 25,000 Linksys Smart Wi-Fi Routers Leaking Sensitive Information to the Public Internet
A vulnerability with Linksys Smart Wi-Fi routers allows attackers to gain unauthenticated, remote access to the vulnerable router and to
Top 10 Best Vulnerability Scanner For Penetration Testing – 2019
A vulnerability scanner is one of the essential tools in IT departments Since vulnerabilities pop up every day and thus
Companies’ Stock Value Dropped 7.5% after Data Breaches
After analyzing the top three breaches from the past three years, Bitglass found that in the aftermath of a data