Microsoft Renewed its Attack Surface Analyzer, Version 2.0 is Online
Microsoft has renewed its Attack Surface Analyzer tool to take advantage of modern, cross-platform technologies.
The first version of the Attack Surface Analyzer 1.0 was released back in 2012, it aims at detecting and changes that occur in the Windows operating systems during the installation of third-party applications.
The Analyzer has been released on GitHub, it has been developed using .NET Core and Electron. The choice to use these two cross-platform technologies allows running on macOS and Linux, and of course Windows.
“Attack Surface Analyzer is a Microsoft-developed open source security tool that analyzes the attack surface of a target system and reports on potential security vulnerabilities introduced during the installation of software or system misconfiguration.” reads the README file published by Microsoft.
“Attack Surface Analyzer 2.0 replaces the original Attack Surface Analzyer tool, released publicly in 2012.”

Users of Attack Surface Analyzer could determine changes to the system attack surface introduced when a software is installed and evaluate risk presented when third-party software is installed.
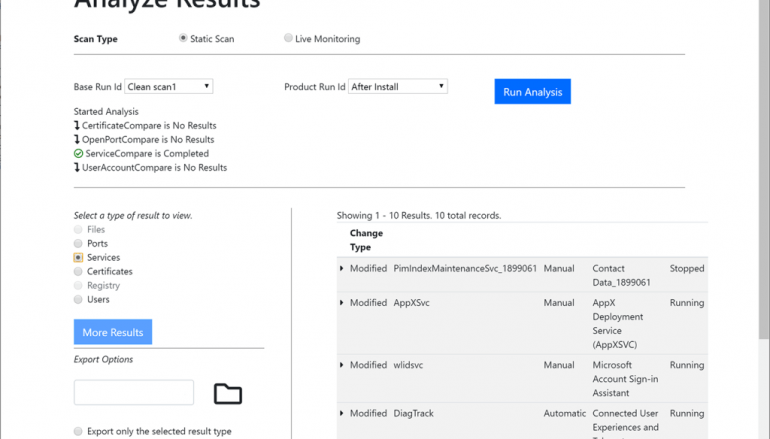
The tool is able to detect any changes to OS components, including file system (static snapshot and live monitoring available), user accounts, services, network ports, certificates, registry (Windows only).
“The core feature of Attack Surface Analyzer is the ability to “diff” an operating system’s security configuration, before and after a software component is installed.” continues Microsoft. “This is important because most installation processes require elevated privileges, and once granted, can lead to unintended system configuration changes.”
“This tool can play an important role in ensuring that the software you develop or deploy doesn’t adversely affect the operating system security configuration by allowing you to scan for specific types of changes,” reads a blog post published by Microsoft.
Microsoft pointed out that the tool includes both Electron and command line interface options. The results for the command line use option are written to a local HTML or JSON file, an implementation choice that makes it easy to include the tool in the user automated toolchain.
This post Microsoft Renewed its Attack Surface Analyzer, Version 2.0 is Online originally appeared on Security Affairs.