Latest News
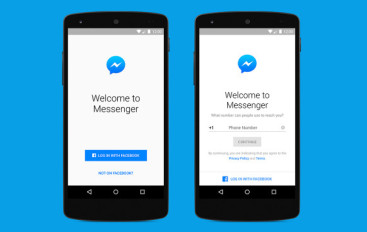
Facebook Messenger Starts Testing End-to-End Encryption
Facebook is planning to use end-to-end encryption for its Messenger app and has begun rolling out the feature. Facebook has
Edward Snowden Designs an iPhone Case to Detect & Block Wireless Snooping
We just cannot imagine our lives without smartphones, even for a short while, and NSA whistleblower Edward Snowden had not
Beware: DDOS attacks a greater threat than ever
DDoS attacks are on the increase with an average of 124,000 attacks per week over the last 18 months reported
ATM Security in the Battle Against Fraud and Physical Attacks
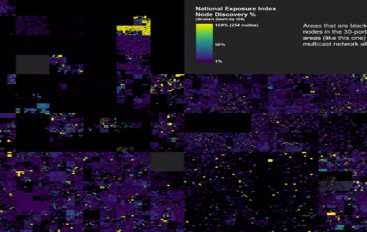
For today’s banks the monitoring and security of ATMs is a major priority. Not content with card skimming – whereBelgium Tops List of Nations Most Vulnerable to Hacking
A new “heat map of the internet” has revealed the countries most vulnerable to hacking attacks, by scanning the entire
AT&T Highlights Progress in 5G Lab Trials, New Markets and Vendors
DALLAS, Texas, June 6, 2016 /PRNewswire/ — AT&T* is now working with Nokia to expand our 5G lab trial work. In
Sabotage of telecoms masts reignite Swedish security fears
The mysterious suspected sabotage of three telecommunications masts, key parts of Sweden’s infrastructure, has reignited fears of foreign spies and
Prioritizing Patch Management Critical to Security
That lack of attention can cost. Recent stats from the Verizon Data Breach report showed that many of the most
This sneaky mobile malware just evolved into something even nastier
A piece of Android malware designed to steal banking log-ins has added UK banks to its list of targets in
Irongate ICS Malware Steals From Stuxnet Playbook
New malware that targets industrial control systems called Irongate was found by researchers who say the discovery should serve as
Knowledge of attack patterns key to protecting digital operations
Companies and organizations must be able to first identify all cyberattack patterns in an attempt to develop a reliable protection
Study Finds Widespread HIPAA Violations Occurring on Yelp
It is no secret that the Health Insurance Portability and Accountability Act (HIPAA) is a trap for the unwary. A
An in-depth guide to turning a product into an open source project
One occasionally runs into a company trying to build an open source project out of an existing product. This is
Rowhammer Attacks on Microsoft Edge Can Compromise Entire PC, New Research Shows
Four researchers from the Vrije University in the Netherlands have put together a successful attack on Windows 10 that uses
Student convicted after finding encryption flaws in government network
A student from the University of Maribor in Slovenia has ended up with a prison sentence after finding cryptographic flaws
Qualcomm Expects Chip Family to Enable Wireless Virtual Reality
TAIPEI—Qualcomm, the world’s largest supplier of chips for mobile devices, announced a suite of chips today at the Taipei Computex