Posts From CCME
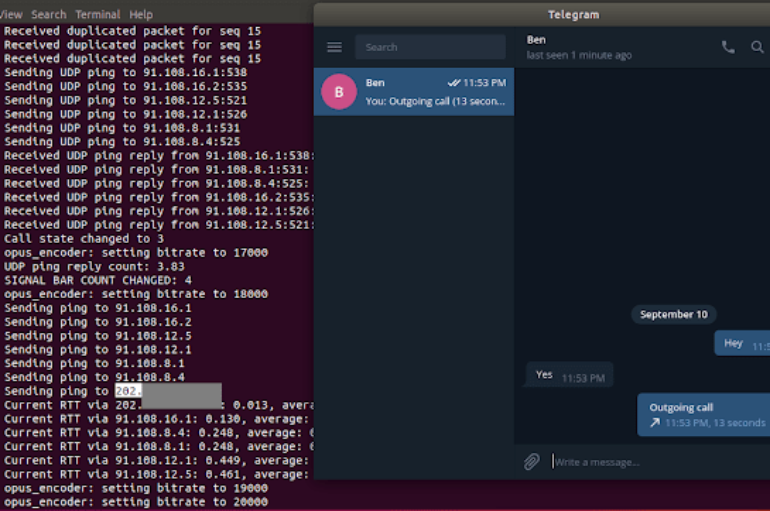
CVE-2018-17780 – Security researcher Dhiraj Mishra discovered that Telegram default configuration would expose a user’s IP address when making a call. Strangely tdesktop 1.3.14 and Telegram for windows (3.3.0.0 WP8.1) leaks end-user private and public IP address while making calls. .@telegram unsafe default behavior of
New EU Regulation Requiring Payments Of More Than €30 Will Require Multifactor Authentication
In light of the news from the EU that will mean payments of over €30 will require multifactor authentication, please see the below comments from Brett Beranek, General Manager, Security Line of Business, Nuance Enterprise Division. Brett Beranek, General Manager, Security
It is being reported that Facebook said an attack on its computer network led to the exposure of information from nearly 50 million of its users. The company discovered the breach earlier this week, finding that attackers had exploited a feature in Facebook’s code that
The worst suspect is a disconcerting reality, Facebook admitted that advertisers were able to access phone numbers of its users for enhanced security. Researchers from two American universities discovered that that phone numbers given to Facebook for two-factor authentication were also
Over Half Of SMBs Have Experienced A Data Breach
Following Cisco’s SMB Cybersecurity Report, which has revealed that 53% of midmarket companies have experienced a data breach, Todd Peterson, Product Manager at One Identity, discusses why they are such an attractive target to hackers and how they can protect
In its first enforcement of the Identity Theft Red Flags Rule, the SEC fined Voya Financial Advisors one million dollars for insufficient security policies to protect confidential personal data. Will LaSala, Director Security Solutions, Security Evangelist at OneSpan: “This is
Over ten years ago, five credit unions came together and formed a credit union service organization (CUSO). A majority interest was held by one, very large credit union, which owned all of the technology, had a full-time IT staff and
Fortinet’s new network access control (NAC) product line secures IoT environments. The security vendor also integrated IoT device visibility and control capabilities into its Security Fabric platform. The company acquired NAC vendor Bradford Networks earlier this summer, and today it’s
Recently, most of the organizations experienced severe downfall due to an undetected malware, Deeplocker, which secretly evaded even the stringent cyber security mechanisms. Deeplocker leverages the AI model to attack the target host by using indicators such as facial recognition,
NETSCOUT SYSTEMS, INC., (NASDAQ: NTCT), a leading provider of service assurance, security, and business analytics, announced that it has been named as the best ‘Anti-DDoS Solutions Vendor of the Year’ at Frost & Sullivan’s 15th annual 2018 Asia Pacific ICT
Illusive Networks Expands FirstMove Services to Drive Adoption of Deception-based Security
Illusive Networks, the award winning leader in deception-based cybersecurity, announced the availability of its FirstMove services, the industry’s first comprehensive set of professional and consulting services aimed at helping customers plan, deploy, and optimize a deception-based approach to cybersecurity. A
Acalvio™ Technologies, the global cloud deception leader, announced availability of ShadowPlex Cloud, a fundamentally new platform designed to protect cloud assets. Built on Acalvio’s patented Autonomous Deception technology, ShadowPlex Cloud detects malicious activity within public cloud environments with precision and
Network packet brokers (NPB) have played a key role in helping organizations manage their management and security tools. The tool space has exploded, and there is literally a tool for almost everything. Cybersecurity, probes, network performance management, forensics, application performance,
Every day, security researchers and hackers discover new vulnerabilities, augmenting the tens of thousands of known holes in applications, services, operating systems, and firmware. A vulnerability scanner provides automated assistance for tracking known vulnerabilities and detecting your exposure to them.
How to Hunt For Security Threats
Organizations ready to take the next step in threat detection tools and methods should explore the emerging practice of threat hunting as a way to improve their security and monitoring operations. IT security teams are constantly on the lookout for
Enterprises and their Security Operations Centers (SOCs) are under siege. Security events are being triggered from all corners of the security stack – from the firewall, endpoints, and servers, from intrusion detection systems and other security solutions. What’s more is