Posts From CCME
NCSC Tackles 10 Attacks on Government Per Week
The UK’s National Cyber Security Centre (NCSC) has blocked more than 10 cyber-attacks per week in its first two years of operation, blaming nation states for the majority of incidents. The government body was spun out of GCHQ in 2016
Execs Fear Orgs Unprepared for Incident Response
Executive-level security professionals fear their organizations are not well positioned to respond to a cyber-attack, according to the results of a new poll from Deloitte. In a poll of more than 3,150 security professionals across all industries and sectors taken
Bug in New iOS Lets Attacker Access iPhone Pics
A new vulnerability discovered in Apple’s latest iOS, 12.0.1, released last week, allows an attacker with physical access to an iPhone entry into photos on a locked phone, according to Jose Rodriguez, a Spanish security researcher. While the bypass bug,
UK’s MoD Exposed in 37 Security Breaches: Report
The UK’s Ministry of Defence (MoD) appears to have exposed highly sensitive data and systems to the risk of compromise after reports revealed 37 breaches of security protocol last year. The heavily redacted reports don’t indicate whether the security breaches
UK Launches “World First” IoT Code of Practice
The UK government claims to be leading the way with a newly released Code of Practice (CoP) designed to drive security-by-design in the manufacture of IoT products. Developed in partnership with the National Cyber Security Centre (NCSC), the ICO and
Endpoint Attacks Increase as Patching Slows
While it’s no surprise that organizations are being compromised, a new study released by Ponemon Institute found that the rate at which organizations are compromised is quite alarming. The study, 2018 State of Endpoint Security Risk, found a 20% increase
Free Wi-Fi is convenient, but it is also unsafe and puts users at great risk. Here’s how the cybercriminals attack user on these open networks. The free Wi-Fi is one of the catchiest things for the users in today’s world.
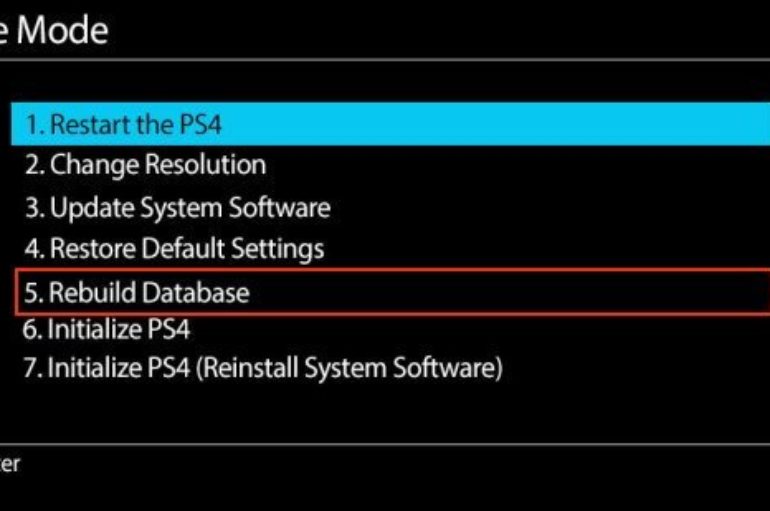
PlayStation 4 gaming consoles could crash when they receive messages containing certain symbols from fellow gamers. The consoles could freeze on while the owners are playing their preferred games, the DoS condition is triggered while the devices are parsing symbols
iPhone a Growing Target of Crypto-Mining Attacks
Apple has increasingly been the target of crypto-mining attacks, and according to Check Point, iPhone attacks increased by nearly 400% over the last two weeks in September. In its most recently published Global Threat Index, Check Point researchers said they
Attack Vectors Long Quiet Make Loud Q3 Comeback
Cyber-criminals eased into the year with a somewhat quiet first and second quarter, but according to a new report from Malwarebytes, attackers made some noise in Q3 2018. In the Cybercrime, Tactics and Techniques Q3 2018, researchers found that business
WannaCry Cost NHS GBP92 Million
The infamous WannaCry ransomware campaign of 2017 caused losses in the region of GBP92m for the NHS, the government has revealed. In a progress update titled Securing cyber resilience in health and care, the Department of Health and Social Care
Hackers Win Big by Gambling on Identity Spoofing
In analyzing global cybercrime patterns ThreatMetrix found that identity spoofing, fueled by stolen identity data, is the most prevalent attack vector for the gaming and gambling industry. Additionally, the Q2 2018 Gaming & Gambling Report discovered that location (IP) spoofing
Organizations globally are suffering a crippling cybersecurity workforce “gap” of 2.9 million employees today, putting the majority at greater risk of attack, according to the latest estimates from (ISC)2. The global certifications body has introduced a new gap analysis methodology,
One in 10 Reported Emails Verified as Malicious
New findings from Cofense have revealed that one in ten reported emails in 2018 were malicious, with more than 50% of those linked to fraudulent attempts to gather login and system information from users – known as credential phishing. As
Best Antivirus Software: 13 Top Tools
The AV-TEST Institute recently tested the most popular Windows 10 client antivirus products on three primary criteria: protection, performance, and usability. Only five of the 18 products tested earned a perfect rating of 6 for each of those criteria: Bitdefender
The number of compromised credentials detected in North American botnets has soared 141%, according to the latest quarterly analysis from Blueliv. The cyber-threat intelligence vendor scans the open, deep and dark web for signs of stolen log-ins for its clients,