Posts From CCME
The 20-year-old security researcher James Lee publicly disclosed details and proof-of-concept exploits for two zero-day vulnerabilities in Microsoft web browsers. The expert opted to disclose the flaw after the tech giant allegedly failed to address the zero-day issues privately he
Hackers continue to employ new techniques to evade detection from antivirus and other security products. This time they started using previously reported and widely used BOM technique. Previously Russian hacker groups used this technique to modify the hosts file on
New Android Malware Gustuff Targeting 100+ Banking, 32 Cryptocurrency and Messengers Apps such as WhatsApp
Gustuff a fully automated baking malware that abuses the accessibility Service to steal login credentials from 100+ global bank accounts and robs users of 32 cryptocurrency apps. The Accessibility Services in Android devices is to assist users with disabilities in
John the Ripper – Pentesting Tool for Offline Password Cracking to Detect Weak Passwords
John the Ripper is a fast password cracker which is intended to be both elements rich and quick. It combines a few breaking modes in one program and is completely configurable for your specific needs for Offline Password Cracking. Out
aka APT33 Hackers Attacked 50 Organizations by Launching a Variety of Malware & Free Hacking Tools
Relentless espionage Group also called as aka APT33 (Elfin) targeting various organization in Saudi Arabia and United States by deploying a variety of malware in their network. Aka APT33 group specifically targeting corporate networks and it compromised around 50 organizations
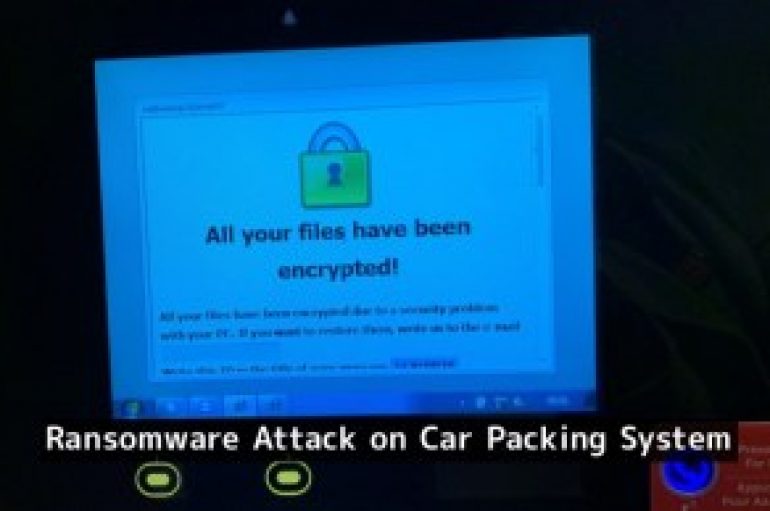
Canadian Internet Registration Authority Hit with Ransomware Attack on Car Packing System
Canadian Internet Registration Authority (CIRA) car packing system hacked and infected with ransomware that allows everyone to have a free park. CIRA is an Internet domain registration authority that manages more than 2.8 million .ca domain, the Internetcountrycodetop-level domain (ccTLD)
Most IT security professionals believe governments that mandate end-to-end encryption backdoors are exposed to a greater risk of nation state cyber-attacks, according to Venafi. The security vendor polled over 500 industry professionals at the recent RSA Conference in San Francisco
Mutli-Cloud Poses Backup Management Woes
Though backup is a known best-practice approach to IT risk management, many companies are overwhelmed by the number of sites that need to be backed up, according to a new survey released today by Barracuda Networks. The study, Closing Backup
Shodan IoT search engine announced the launch of a new service called Shodan Monitor designed to help organizations to maintain track of systems connected to the Internet. Shodan, the popular IoT search engine, announced this week the launch of a
Dangerous Function in UC Browser Lets Hackers to Hijack Millions Of Android Users via MITM Attacks
Potentially dangerous future in UC browser puts Hundreds of millions of Android users under high risk that allows hackers to hijack Android devices via Man-in-the-Middle Attacks. A hidden future that uncovered in UC browsers let attackers download and run untested
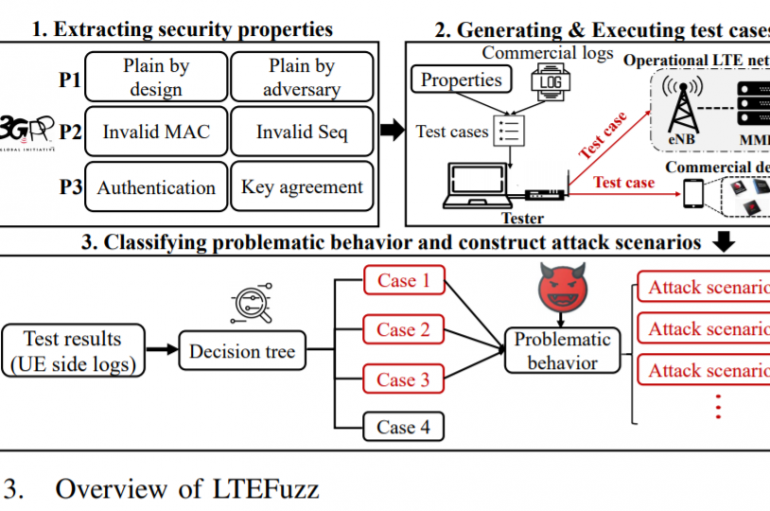
A team of researchers from the Korea Advanced Institute of Science and Technology Constitution (KAIST) discovered 36 vulnerabilities in the LTE protocol. Security experts from the Korea Advanced Institute of Science and Technology Constitution (KAIST) have discovered 36 vulnerabilities in
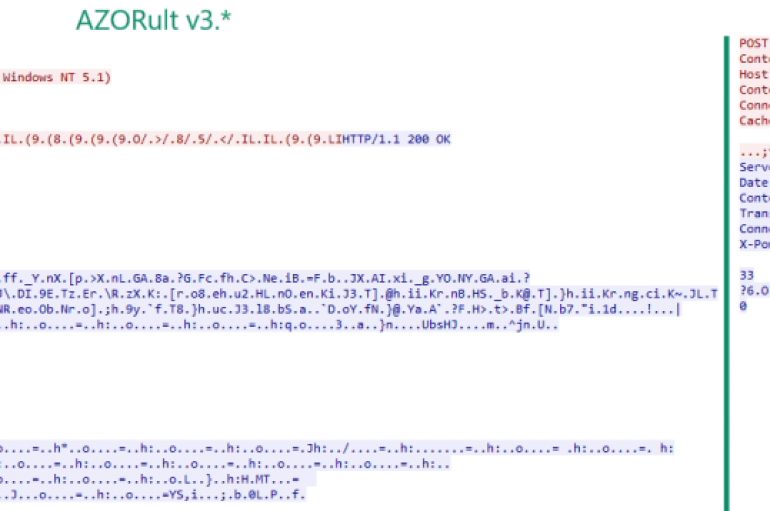
Experts from Kaspersky observed a new C++ version of the AZORult data stealer that implements the ability to establish RDP connections. The AZORult Trojan is one of the most popular data stealers in the Russian cybercrime underground. The AZORult stealer
According to MalwareBytes’s 2019 State of Malware Report, Trojans and crypto miners are the dominate malware threats of 2019. Android phones may get infected with malware less often than Windows computers, but that doesn’t mean they’re not vulnerable. With more
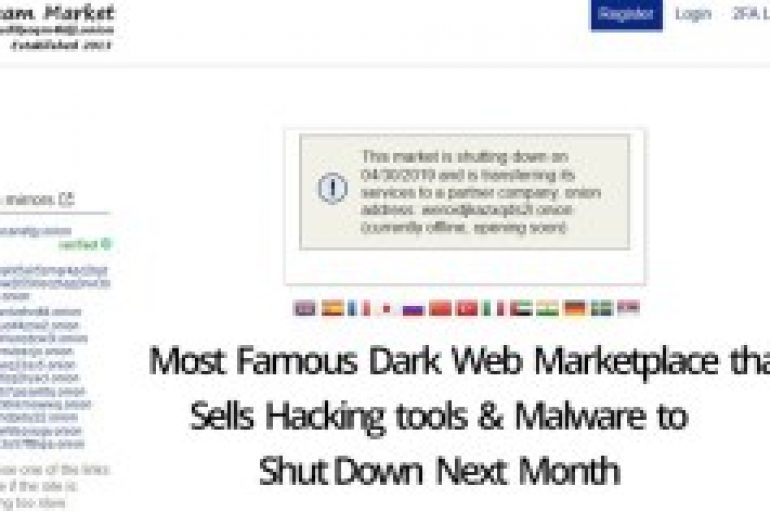
Most Famous Dark Web Marketplace that Sells Hacking tools & Malware about to Shut Down Next Month
Largest and notorious dark web marketplace Dream Market announced that it is scheduled to shut down its operation’s on April 30, 2019. Dream market has been for six years, it is was the largest market place in the dark web
Norsk Hydro is still in the process of restoring its IT systems after a devastating ransomware attack last week which has already caused the firm as much as GBP40m ($41m). The Norwegian firm, one of the world’s largest producers of
The NETSCOUT Threat Intelligence team uncovered a credential harvesting campaign tracked as LUCKY ELEPHANT targeting mostly South Asian governments. Security experts at NETSCOUT Threat Intelligence team uncovered a credential harvesting campaign, tracked as LUCKY ELEPHANT, targeting mostly South Asian governments. The