Posts From CCME
Computer Forensics tools are more often used by security industries to test the vulnerabilities in network and applications by collecting the evidence to find an indicator of compromise and take an appropriate mitigation Steps. Here you can find the Comprehensive
A new free cyber threat Intelligence tool that helps you in identifying malicious IP addresses and domains. It provides you a clean and easy to understand dashboard and it rates top attackers IP address, attacked ports, malicious domains, scanners, and
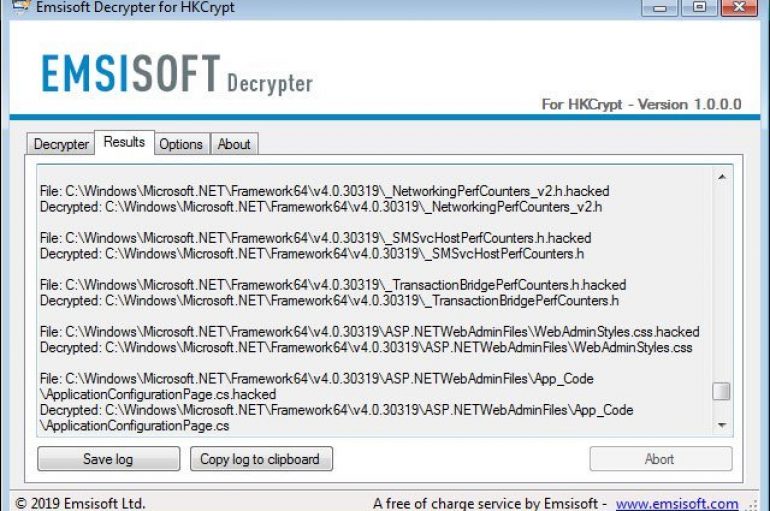
Good news for the victims of the Hacked Ransomware, the security firm Emsisoft has released a free decryptor to decrypt the data of infected computers. Security experts at Emsisoft released a free decryptor for the Hacked Ransomware. The Hacked Ransomware
The Recent Widely Spreading Lockergoga Ransomware Infection Can Be Stopped by Creating a Shortcut (LNKfile)
Lockergoga infection was first spotted in January 2019, the ransomware particularly targets on critical infrastructure. The Lockergoga ransomware encrypts all the files in the system and appends .locked extension and leaves a ransom note in the desktop folder. It was
So Long and Farewell: Dream Market Says Goodbye
Cyber-criminals have long relied on the Dark Web’s largest marketplace, Dream Market, to buy and sell illicit goods, but today threat researchers at IntSights and Flashpoint found that the notorious online store is scheduled to shutdown on April 30, 2019.
Over half (52%) of IT and security professionals believe that cybersecurity skills shortages are putting their business at an increased risk of attack, according to a new poll from Infosecurity Europe. Now in its 24th year, Europe’s leading cybersecurity show
Most Security Pros Are Impacted by Geopolitics
Two-thirds of cybersecurity professionals have been forced to change where and with whom they do business because of escalating concerns around nation state attacks, according to Tripwire. The security vendor polled 218 security professionals at the RSA Conference in San
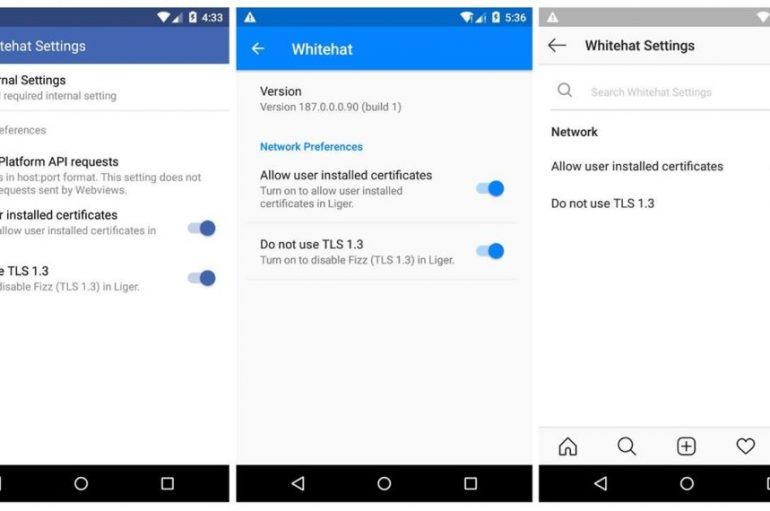
Facebook introduced new settings designed to make it easier for cyber experts to test the security of its mobile applications. Facebook has announced the implementation of new settings to make it easier for white hat hackers to test the security
Telegram Now Allows You to Delete All Your Private Messages Anytime from both Sender & Receiver
Telegram now landing into the peak of the privacy and let users delete their entire private messages from both sender and receiver side regardless of the time limit. Telegram is one of the most trusted platform and the one who
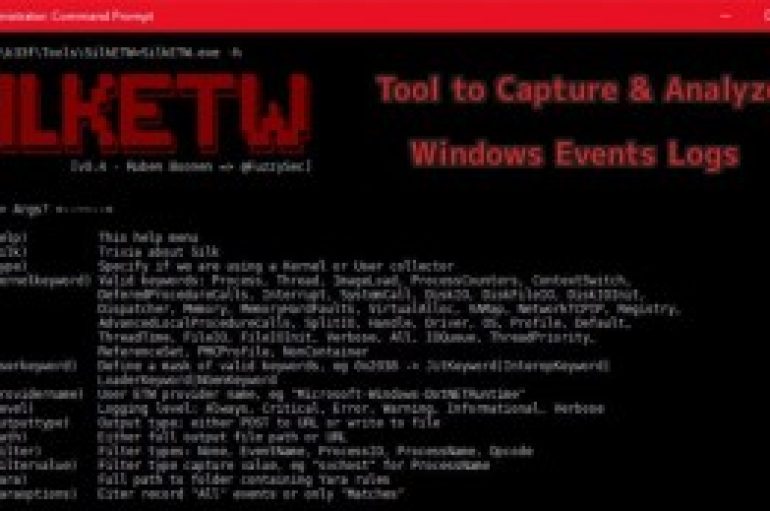
SilkETW is a flexible tool aimed to reduce the complexities of ETW(Event Tracing for Windows) and to put actionable data in the hands of researches on both the defensive and offensive side. ETW is a kernel-level tracing facility that allows
It is a battle with no holds barred between T-Series and PewDiePie, their fans are spreading the PewDiePie ransomware to force users to subscribe to PewDiePie Youtube channel. The story I’m going to tell you is another chapter of the
Anubis II – Malware and Afterlife
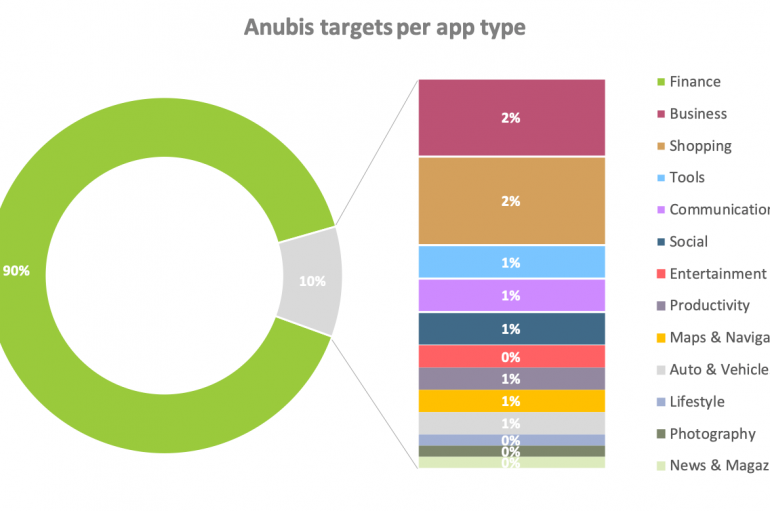
Due to the growing demand for Android banking malware, threat actors continue using Anubis even is the creator has vanished. Besides being the Egyptian God associated with mummification and afterlife, Anubis is also an Android banking malware that has caused
Despite the growing number of employees that work remotely, security professionals fear that remote workers pose risks to the enterprise, according to a new study published by OpenVPN. An overwhelming majority (90%) of survey respondents said that remote workers are
Privacy a Top Concern in ‘Biometric Exit’
Despite bipartisan concerns over privacy, most airlines reportedly support the use of facial recognition, and the US Customs and Border Patrol (CBP) has implemented facial recognition in 17 international airports, including Atlanta, New York City, Boston, San Jose, Chicago, and
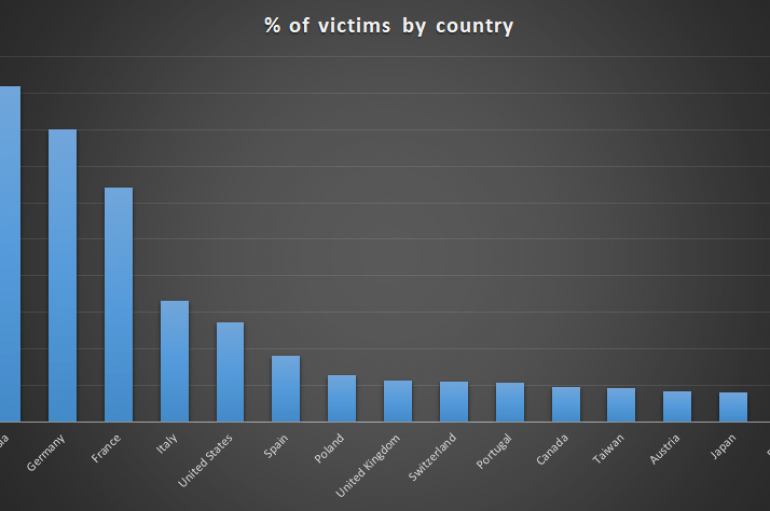
Operation ShadowHammer – ASUS is the last victim of a clamorous supply chain attack that delivered a backdoor to more than one million users, Kaspersky Lab reported. Over 1 million ASUS users may have been impacted by a supply chain
XSS is a very commonly exploited vulnerability type which is very widely spread and easily detectable and also it is one of the important vulnerability in OWASP TOP 10. What is XSS( Cross Site Scripting )? An attacker can inject