Posts From CCME
New Miori Malware Uses Text-based Protocol to Communicate with C&C Server for Launching a DDoS Attack
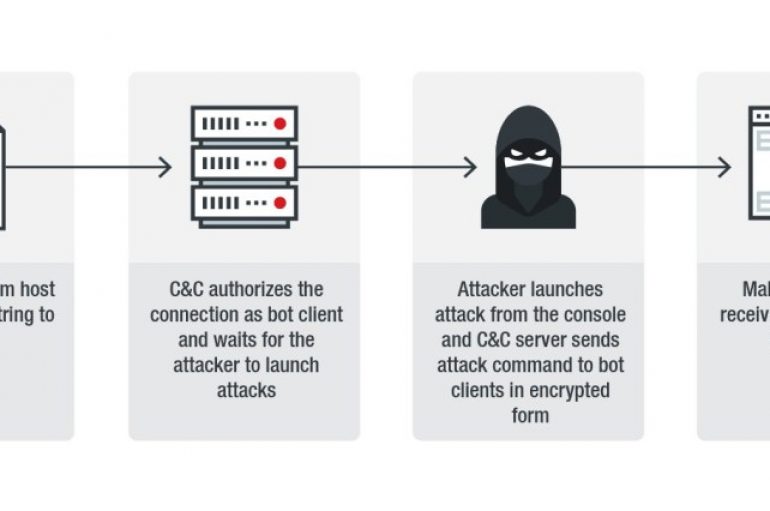
A new Mirai variant dubbed Miori uses text-based protocols to establish communication with command-and-control (C&C) servers. The Miori campaign was identified in last year December, exploiting vulnerability n the ThinkPHP programming framework. Miori targets IoT devices and exploits them by
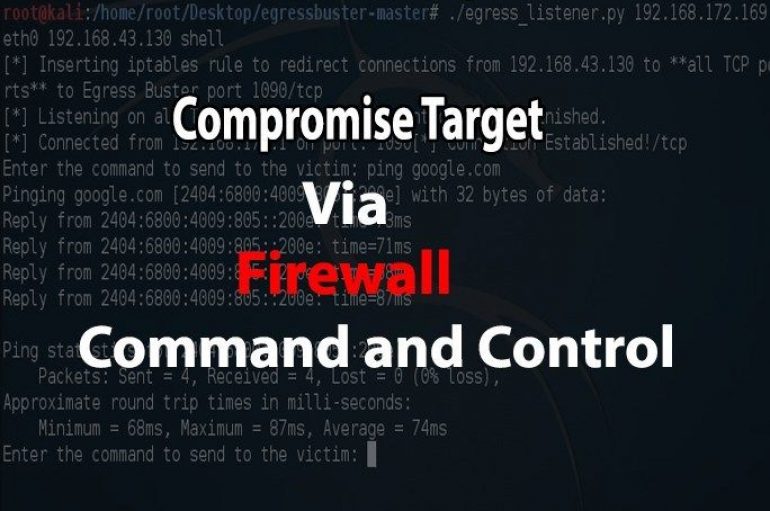
EgressBuster – A Pentesting Tool to Compromise Victim via Command & Control using Firewall
Network Firewalls acts as a fortification to keep the internal corporate network secure. Many people often think as it is protecting a device from incoming traffic. Most outbound connections are insecure without egress traffic filtering. If Egress Traffic Filtering failed
Vulnerability in Intel Processor Diagnostic Tool Let Hackers Perform Escalation of Privilege and DOS Attack
Intel released new security updates with the fixes of two vulnerabilities that affected Intel Processor Diagnostic Tool and Solid State Drives (SSD) for Data Centers (DC) S4500/S4600 Series. Vulnerability in Processor Diagnostic Tool categorized as “High” Severity and the other
A new variant of the implements a unique protocol to communicate with Command and Control infrastructure A new variant of the Mioribotnet uses a unique protocol to communicate with C&C infrastructure, it implements a protection mechanism to access the login
Hacked Hair Straightener Could Set a Fire
Security researchers have hacked hair straighteners from Glamoriser, according to Pen Test Partners. The UK firm bills itself as the maker of the “world’s first Bluetooth hair straighteners,” devices that users can link to an app so that the owner
Attacks in Turkey Used Excel Formula Injection
Having tracked the activities of threat actors suspected of being involved in a large number of malicious spam attacks targeting organizations based in Turkey, Sophos researchers determined that the attackers flew under the radar using Excel formula injections to deliver
According to a survey of 100 healthcare professionals from hospitals to physician group practices, more than half of respondents are highly confident in the cybersecurity of their patient portals. The State of Patient Identity Management report, published by LexisNexis(R) Risk
Earlier this year an experienced team of researchers at Northeastern University’s Khoury College of Computer Sciences in Boston proved that an airliner’s complex radio-navigation system can be hacked by a $600 software-defined radio. The SDR (Software-defined radio), which is available
BITPoint Japan-based cryptocurrency announced that hackers have stolen more than $32 million (3.5 billion yen) worth of cryptocurrency due to a cyber attack. BITPoint Japan-based cryptocurrency was victim of a cyber attack, the Remixpoint’s subsidiary announced that hackers have stolen
Sea Turtle DNS Hijackers Go After More Victims
A notorious state-sponsored cyber-espionage campaign has expanded its operations with new victims and DNS hijacking techniques, according to Cisco Talos. The security vendor claimed in a new blog post that the actors behind the Sea Turtle attacks – first revealed
Apple has disabled a popular comms app on its watchOS after concerns were raised over users being able to eavesdrop on each other. Available on the Apple Watch Series 1 or later with watchOS 5, the Walkie-Talkie app allows users
Buhtrap Hackers Group Using Recently Patched Windows Zero-day Exploit to Attack Government Networks
An Infamous Cyberespionage group known as “Buhtrap” uses a Windows Zero-day exploit for its new campaign to attack businesses and perform targeted attack governmental institutions. Buhtrap hackers group actively targeting various financial institutions in 2015, since then the group improvising
Kiosk Vulnerability Puts Customer Data at Risk
Researchers have discovered a vulnerability impacting a leading manufacturer of managed kiosks found in hotels, businesses, retail and other industries that could allow a malicious actor access to the cloud database, according to Trustwave. Uniguest outsources secure, fully managed customer-facing
Buhtrap Group Using Zero-Day Attack in Windows
Microsoft has issued a patch to fix a zero-day exploit in Windows that was being deployed in a highly targeted attack in Eastern Europe, according to ESET researchers. ESET reported the exploit to the Microsoft Security Response Center, which fixed
Flaw in GE Anesthesia and Respiratory Devices
Researchers have discovered a vulnerability that could allow an attacker to send remote commands that will interfere with the device’s normal working order in the protocol of in-hospital anesthesia devices, GE Aestiva and GE Aespire (models 7100 and 7900), according
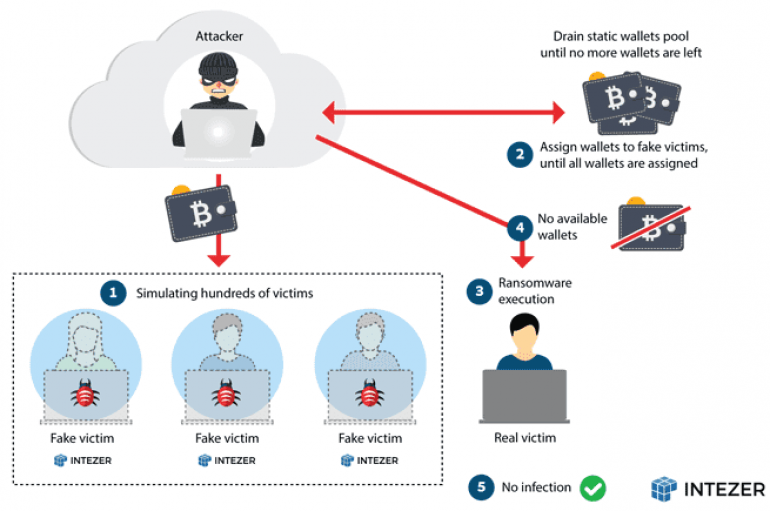
A New NAS Ransomware Targets QNAP Devices
Malware researchers at two security firms Intezer and Anomali have discovered a new piece of ransomware targeting Network Attached Storage (NAS) devices. Experts at security firms Intezer and Anomali have separately discovered a new piece of ransomware targeting Network Attached