Posts From CCME
New Malware Samples Resemble StrongPity
Researchers have said with high confidence that the publicly reported adversary dubbed StrongPity has been engaged in an unreported and ongoing malware campaign, according to research from AT&T Alien Labs. Threat actors are using the new malware and infrastructure to
Top Call Center Security Considerations for Safe Cloud Migration and Protecting Customer Data and Privacy
With the increasing pace of digitalization, call centers are required to take numerous security considerations including Safe Cloud Migration into account, especially when handling customer and business data. Over recent years, the preferred method of customer and business data protection
The UK’s National Cyber Security Centre (NCSC) has dismantled tens of thousands of phishing campaigns and fraudulent websites over the past year as its Active Cyber Defence (ACD) program continues to lead by example globally. In an update on Tuesday,
Kali Linux announced a free Kali NetHunter App Store available for non-NetHunter devices so that anyone can avail the packages. Starting from Kali NetHunter 2019.2 it supports more than 50 Android devices running KitKat through to Pie. “The Kali NetHunter
The Federal Bureau of Investigation (FBI) released master decryption keys for all the version ( 4, 5, 5.0.4, 5.1, and 5.2 ) of Notorious GandCrab ransomware which can be used for both organization or individual. Gandcrab ransomware initially spotted in
American telecommunication company Sprint recently learned that hackers breached the customers account through Samsung website. According to the letter shared by the company on June 22, says that “unauthorized access to your Sprint account using your account credentials via the
Vulnerability in Windows Defender Application Control Let Hackers Bypass It’s Security Feature
Microsoft released a new security update for the vulnerability that affected Windows Defender Application Control (WDAC) that allows a local attacker to bypass the WDAC security feature. Windows Defender Application Control restricts which applications users are allowed to run and
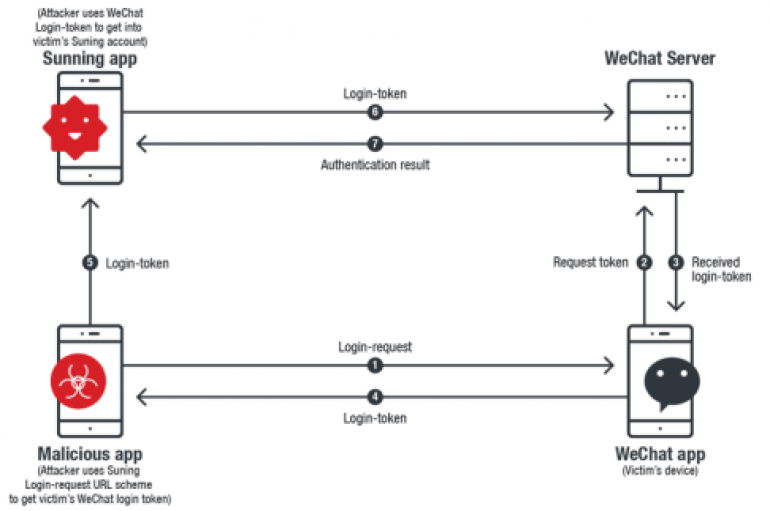
Security experts at Trend Micro have discovered that iOS URL scheme could allow an attacker to hijack users’ accounts via App-in-the-Middle attack. Security experts at Trend Micro devised a new app-in-the-middle attack that could be exploited by a malicious app
Critical Account Take over Vulnerability Allows to Hack Your Instagram Account within 10 Minutes
A security researcher reported a critical vulnerability that allows malicious hackers to hack Instagram account and take complete control of your Instagram account within 10 minutes. Facebook and Instagram are frequently fixing several vulnerabilities discovered by the internal team and
Cybersecurity incidents have cost UK mid-market firms a combined GBP30bn over the past year as automated attacks become the norm, according to Grant Thornton. The accounting and consulting giant interviewed 500 UK business leaders from firms with revenue of between
Some of the crooks behind the Dridex Trojan have split from the gang and released a forked version of the BitPaymer ransomware dubbed DoppelPaymer. Cybercrime gang tracked as TA505 has been active since 2014 and focusing on Retail and Banking
US Coast Guard Issued Cyber-Safety Alert
The US Coast Guard recommended that ships update their cybersecurity strategies after a malware attack “significantly” degraded the computer systems of a deep draft vessel in February, according to a press release. In the marine safety alert, the Coast Guard
SPARTA is GUI application developed with python and inbuilds Network Penetration Testing Kali Linux tool. It simplifies scanning and enumeration phase with faster results. The best thing of SPARTA GUI Toolkit it scans detects the service running on the target
Media File Jacking – New Flaw Let Hackers Manipulate WhatsApp and Telegram Media Files in Android
A critical security flaw dubbed “Media File Jacking” affected WhatsApp and Telegram for Android let hackers manipulate both apps media files if users enable certain features. Threat actors are able to intercept and manipulate media file without the user’s knowledge
Critical Vulnerability in WordPress Ad Inserter Plugin Let Hackers to Execute Arbitrary PHP Code
A critical remote code execution vulnerability in WordPress plugin Ad Inserter, let hackers execute arbitrary PHP code in the vulnerable installations. The vulnerability was discovered by Wordfence security team and the vulnerability can be executed only by the authenticated users
Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
In earlier years, everyone depends on SOC (includes firewalls, WAF, SIEM,etc.) and the prioritize in building the SOC provides security and the CIA was maintained. However, later the emerge of the attacks and the threat actors becomes more challenge and