Posts From CCME
US telecommunications company Sprint revealed that hackers compromised an unknown number of customer accounts via the Samsung.com “add a line” website. The mobile network operator Sprint disclosed a security breach, the company revealed that hackers compromised an unknown number of customer accounts
Experts at Vertical Structure and WhiteHat Security discovered a serious flaw that exposed millions of files stored on thousands of exposed Lenovo NAS devices. An analysis conducted by researchers at Vertical Structure and WhiteHat Security allowed discovering a vulnerability in
The UK’s National Cyber Security Centre (NCSC) has issued a warning about DNS hijacking threats, as reports emerge of widespread attacks in Brazil affecting 180,000 users. The NCSC posted the advisory on Friday as a follow-up to one issued in
Web-based applications security relies on a number of factors among them is a Web Application Firewall (WAF). Cyberattacks are pouring in numbers and users will need an effective WAF to take care of their web-accessible data. Organizations that are in-route
On July 6, a ransomware attack brought down government computer systems at La Porte County, Indiana, finally, the county decided to pay $130,000 ransom. On July 6, a ransomware attack paralyzed the computer systems at La Porte County, Indiana, according
Japanese Exchange Bitpoint Hit By $32m Cyber-Attack Japan-based cryptocurrency exchange Bitpoint has become the latest to lose tens of millions of dollars in a cyber-attack. The firm said it was forced on Friday to stop all services — including withdrawals,
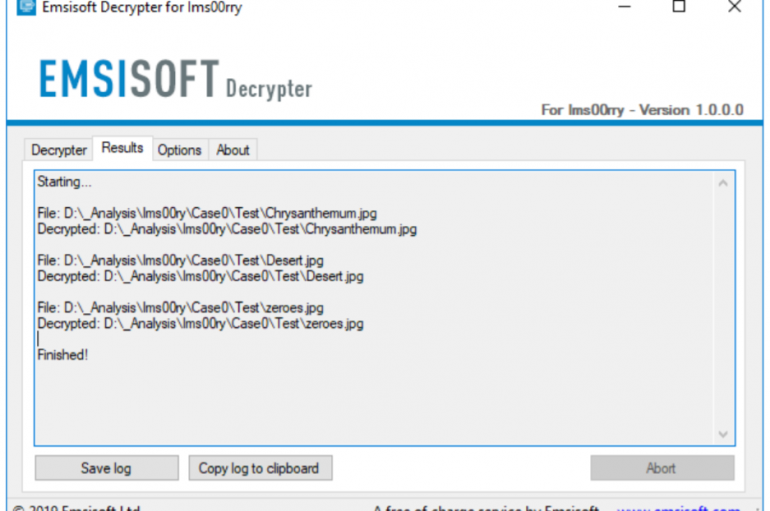
Security experts at Emsisoft released a new decryptor, it could be used for free by victims of the Ims00rry ransomware to decrypt their files. Thanks to the experts at Emsisoft the victims of the Ims00rry ransomware can decrypt their files for
A critical vulnerability affecting the Ad Inserter WordPress plugin could be exploited by authenticated attackers to remotely execute PHP code. Security researchers at Wordfence discovered a critical vulnerability in the Inserter WordPress plugin that could be exploited by authenticated attackers to remotely execute PHP code. Ad Inserter is
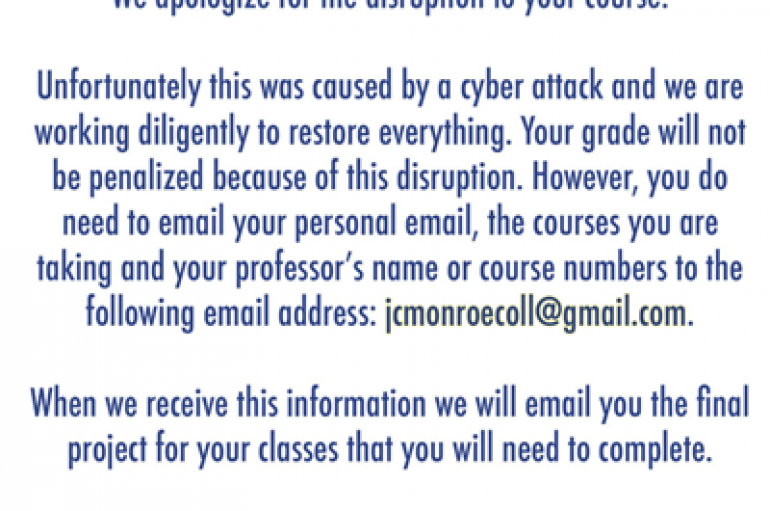
Monroe College Campuses Downed by Ransomware
Monroe College Campuses Downed by Ransomware Multiple campuses of Monroe College have had their systems downed after a ransomware attack reportedly struck the for-profit institution on July 11. The attack reportedly affected each of Monroe’s campuses in Manhattan and New Rochelle,
A serious vulnerability in Walkie-Talkie App on Apple Watch forced the tech giant to disable the applications to avoid attackers spying on its users. Apple has temporarily disabled the Walkie-Talkie app on the Apple Watch due to a vulnerability that
Security Professionals always need to learn many tools, techniques, and concepts to analyze sophisticated Threats and current cyber attacks. Here we are going to see some of the most important tools, books, Resources which is mainly using for Malware Analysis
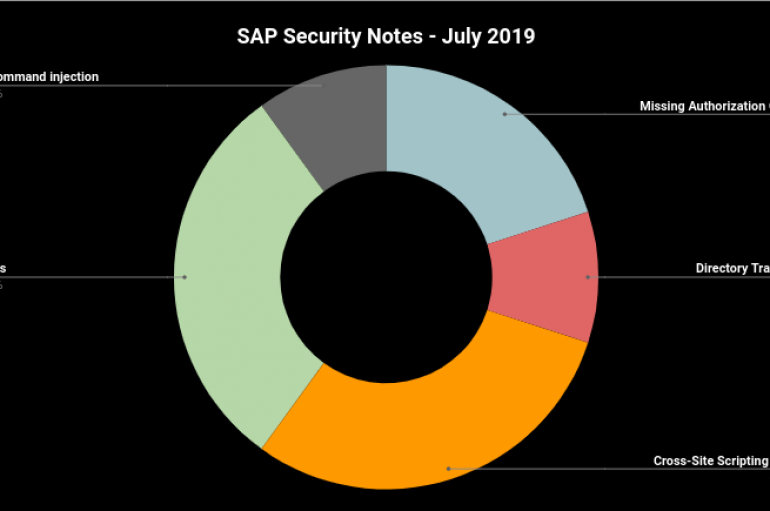
SAP released 11 Security Notes as part of the Patch Day – July 2019, one of which was a Hot News Note addressing a critical flaw in Diagnostics Agent. This month SAP released 11 Security Notes as part of the
Ongoing DNS Hijacking Attack – NCSC Issued an Alert for Organizations and Provide Mitigation Steps
National cybersecurity center issued an alert for ongoing DNS hijacking attack, a large-scale global campaign that targets various countries around the world. NCSC recently observed various targeted attacks which exploit the Domain Name System (DNS) to deface or take down
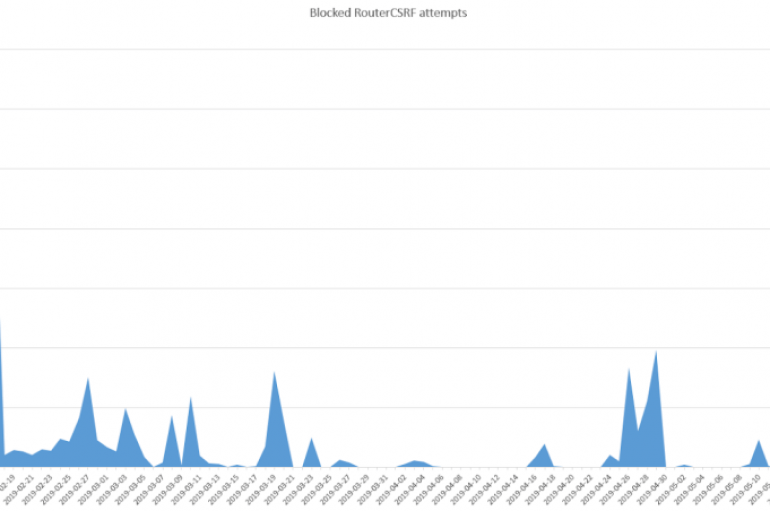
Brazilian users have been targeted bya large number of router attacks aimed at modifying the configuration of their routers for malicious purposes. This year, security experts at Avast have blocked more than 4.6 million cross-site request forgery (CSRF) attempts carried
The General Data Protection Regulation (GDPR) applied on 25 May 2018, this new law applies to all companies that collect and process data belonging to European Union (EU) citizens. This includes companies with operations in the EU and/or a website
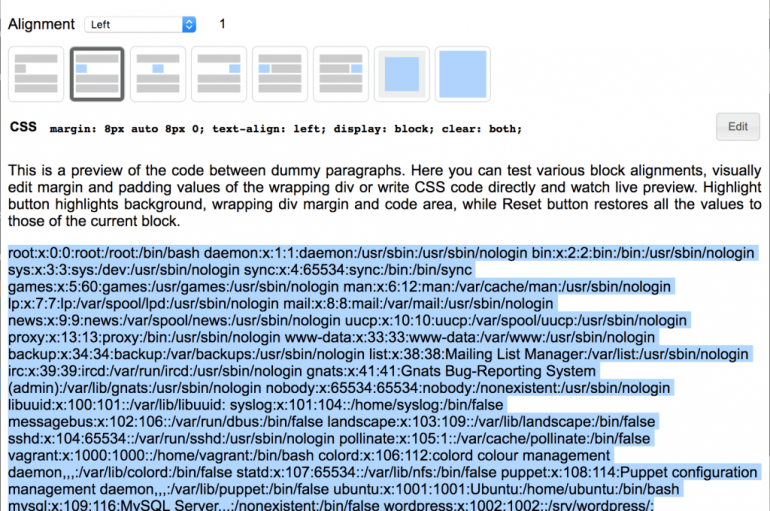
Netcat is a well build network debugging tool, which can read and write data across computers using TCP or UDP, it is also called as TCP/IP utilities. It is capable to act as master and slave to do file transfer,