Posts From CCME
Lancaster University has confirmed that it was “subject to a sophisticated and malicious phishing attack” which resulted in breaches of student and applicant data. This has led to undergraduate student applicant data records for 2019 and 2020 being accessed, including
More than 40% of UK organizations believe cyber-attackers can infiltrate their networks at every attempt, according to new research from CyberArk. CyberArk surveyed 1000 global organizations and detailed its findings in the CyberArk Global Advanced Threat Landscape Report 2019. The
Passwords continue to be a top security challenge for organizations, with penetration testers revealing that they can easily guess passwords in the majority of their engagements, according to the 2019 Under the Hoodie report published by Rapid7. The new report,
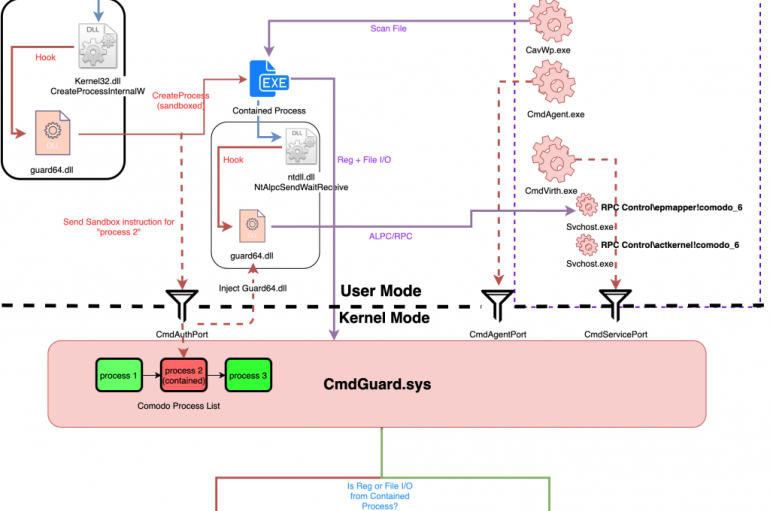
Experts discovered several flaws in Comodo Antivirus, including a vulnerability that could allow to escape the sandbox and escalate privileges. The Tenable expert David Wells discovered five flaws in the Comodo Antivirus and Comodo Antivirus Advanced. Four of the vulnerabilities
A hacker group compromised Russia’s Secret Intelligence Agency and they gained access to terabytes of data stored by the FSB contractor that includes the secret project details. BBC learned that hackers who breached Russian intelligence contractor found that they are
Breach Costs Impact Firms For Years
The average global cost of a data breach has risen again, with experts at IBM claiming the financial impact can be felt for years after an incident. The computing giant’s annual Cost of a Data Breach study has become a
VLC player is still affected by a critical heap-based memory buffer over-read condition, tracked as CVE-2019-13615, that could be exploited by a remote attacker to execute arbitrary code. The VLC player is still affected by a critical remote code execution
Iranian Threat Group Targets LinkedIn Users
Iranian threat actors are believed to be behind a phishing campaign that is masquerading as a member of Cambridge University to target users of LinkedIn, according to FireEye. “In June 2019, FireEye devices detected a large phishing campaign from APT34
Met Police Red-Faced After News Platform Hacked
London’s Metropolitan Police has admitted that its public-facing news platform was compromised last Friday evening, leading to the publication of a string of offensive messages on Twitter. Observers first noticed something was wrong after the Met’s Twitter feed, which has
File copy vulnerability in ProFTPD server allows an anonymous remote attacker to execute the code in vulnerable machine results in remote code execution and information disclosure without authentication. By exploiting the vulnerability attacker can run any program code with the
TrickBot Trojan Pushed as Browser Update
A fake Office 365 site created by malicious actors has been discovered distributing a password-stealing Trojan, according to MalwareHunterTeam. Disguised as Chrome and Firefox browser updates, the site is actually sharing the TrickBot Trojan. Fake Office 365 Site The above
Calamity occurrence in any area, arising from natural or man-made causes, or by accident or negligence which results in substantial loss of asset or business, Flood: Any unplanned event that requires immediate redeployment of limited resources is defined as cyber
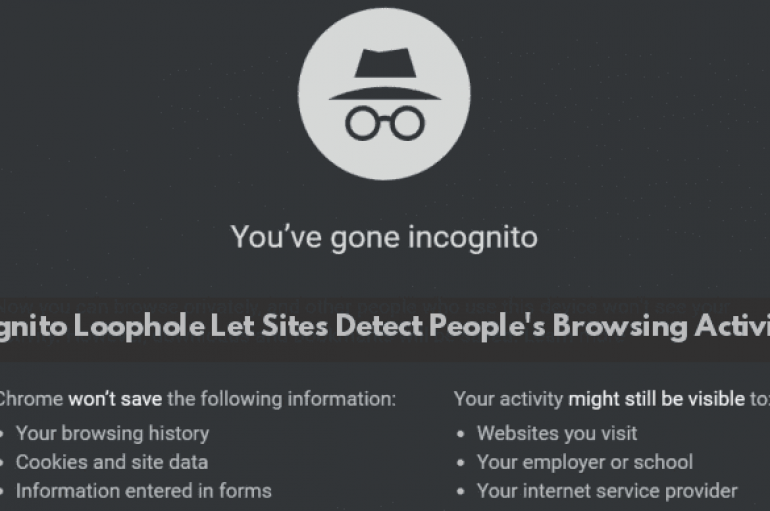
Google announced a release of Chrome 76 beta version on July 30, in which Chrome will remedy an Incognito loophole that has allowed sites to detect people’s browsing activities. Incognito Mode is an optional Chrome’s feature helps users to browse
BlackBerry Cylance has addressed a bypass vulnerability recently discovered in its AI-based antivirus engine CylancePROTECT product. Experts at cybersecurity firm Skylight announced last week that they have devised a method to bypass BlackBerry Cylance’s AI-based antivirus engine, now the company
Over 60 US Colleges Compromised by ERP Exploit
Scores of US colleges and universities have been compromised after hackers exploited a vulnerability in popular ERP software, according to the Department of Education. The government revealed the campaign in an alert last week, explaining that the flaw in question
Russia’s fearsome intelligence agency the FSB has been trying to decrypt Tor traffic since 2012, according to new reports stemming from a major breach of a Russian defense contractor. The firm in question, SyTech, was revealed to be working on