Iranian Threat Group Targets LinkedIn Users
Iranian threat actors are believed to be behind a phishing campaign that is masquerading as a member of Cambridge University to target users of LinkedIn, according to FireEye.
“In June 2019, FireEye devices detected a large phishing campaign from APT34 targeting Middle East critical infrastructure, telecom, and oil and gas entities. This campaign is consistent with the overall Iranian targeting of the energy sector that we’ve seen dating back to at least 2012. Further, this activity is representative of Iran’s overarching efforts to collect strategic information of relevance to its national interests. With increasing geopolitical tensions between the U.S. and Iran and the introduction of new sanctions, we expect Iran to continue to increase the volume and scope of its cyber-espionage campaigns,” FireEye’s principal analyst, cyber-espionage analysis, Cristiana Brafman Kittner wrote in an email.
In addition the behavior aligns with elements of activity reported as OilRig and Greenbug by various security researchers who have attributed those attacks to APT34. “This threat group has conducted broad targeting across a variety of industries operating in the Middle East; however, we believe APT34’s strongest interest is gaining access to financial, energy, and government entities,” researchers wrote.
Victims received a message from Rebecca Watts, a specious member of the research staff at Cambridge University.
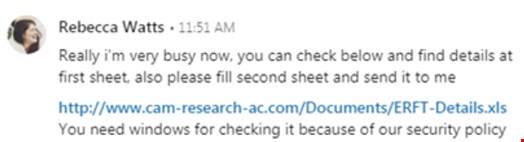
These types of attacks have been seen across social media platforms, whereby criminals attempt to gain a foothold into the network or infrastructure by inducing users to click on malicious links or to download compromised files.
“Organizations and nation-states should be prepared for what is already to all intents and purposes a war. Cybercrime, much like any other form of criminal activity, is either motivated by monetary gains or by political interests, or – more often – by both,” said DomainTools’s senior security advisor Corin Imai.
“Both private and public organizations should be investing in their employees’ cybersecurity training. As threats continue to evolve, having a solid foundational understanding of the best practices to stay safe online is the most effective way to create a first line of defense. In the current climate, organizations can no longer compromise on their security efforts, which should be holistic and account for both technical vulnerabilities and for human ones,” said Imai.
This post Iranian Threat Group Targets LinkedIn Users originally appeared on InfoSecurity Magazine.





