TrickBot Trojan Pushed as Browser Update
A fake Office 365 site created by malicious actors has been discovered distributing a password-stealing Trojan, according to MalwareHunterTeam.
Disguised as Chrome and Firefox browser updates, the site is actually sharing the TrickBot Trojan.
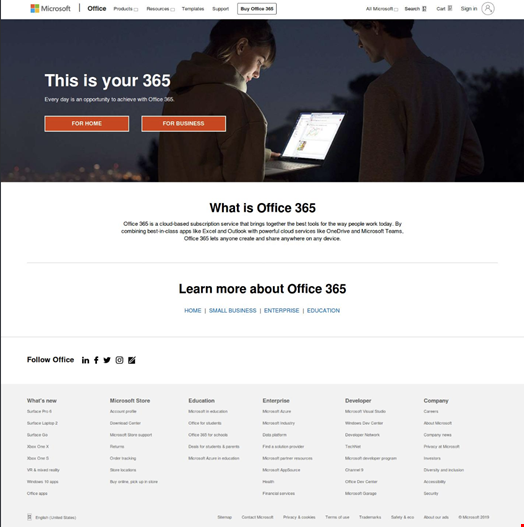
The above sample of one of the links appears to be legitimate, but the site quickly alerts the user that the browser needs to be updated, according to BleepingComputer. Clicking on the update button then launches an executable that installs the Trojan, the report said.
“Chrome is the leading browser, with 63% of web users, which translates to billions of users. With Chrome removing the XSS Auditor, web applications are now at risk of delivering a poor user experience. More users are potentially vulnerable to client-side injections due to that lack of alternatives,” said Deepak Patel, security evangelist at PerimeterX.
“Also, most users are unaware of the security implications of XSS Auditor removal,” he continued. “As a result of the change in Chrome, web application owners now have to take a hard look at client-side protection to preserve the user’s intended path on their web properties. There is also an explosion in the use of third-party code/libraries in any modern application amplifying the client-side threats. The e-commerce, travel and hospitality, and retail verticals, in particular, need to protect their brand reputation. There is a good chance, with Chrome removing XSS Auditor, that bad actors will cash in and infect more users and web visitors. It is time to bolster application security with client-side protection and advanced bot management and mitigation. It is imperative for application owners to take control of the third-party code that runs on the users’ browser. ”
Users are being warned to avoid installing browser updates prompted from pop-up alerts.
This post TrickBot Trojan Pushed as Browser Update originally appeared on InfoSecurity Magazine.