Posts From CCME
While the focus of the (ISC)2 Security Congress happening in Florida this week is cybersecurity, one of the conference’s key players has voiced concerns over what effect technology is having on human health and happiness. In an interview with Infosecurity
It’s Official, Administrative Network at Kudankulam Nuclear Power Plant was Infected with DTrack
The news is shocking, the Kudankulam Nuclear Power Plant (KNPP) that initially denied a malware infection, now admits the security breach. Yesterday a worrying news made the headlines, the Kudankulam Nuclear Power Plant (KKNPP) was hit by a cyber attack.
Internet of Things (IoT) devices can still be a serious security threat even when they are off network. Speaking on day three of the (ISC)2 Security Congress in Orlando, Florida, 802 Secure CSO Michael Raggo shared research that demonstrated the
Malicious Android Dropper App ‘Xhelper’ Reinstall Itself after Uninstall – Infected 45K Devices
Researchers observed a persistent malicious Android dropper app dubbed XHelper capable of reinstalling itself again if users uninstalled from the devices. The malicious app is persistent, once the app installed it hides and downloads other malware, displays pop-up ads. The
A Russian security researcher accidentally discovered API and firmware issues that allowed her to take over all Xiaomi FurryTail pet feeders. The Russian security researcher Anna Prosvetova, from Saint Petersburg, has accidentally discovered API and firmware issues that allowed her
The most common mistake businesses make when it comes to cybersecurity is not implementing it from the get-go, according to Lares COO Andrew Hay. In an exclusive interview with Infosecurity Magazine conducted today at the (ISC)2 Security Congress in Orlando,
DevSecOps automation is at its most effective when humans lend a hand, according to cloud and enterprise security architect and research scientist Professor Gamini Bulumulle. Speaking at the bustling (ISC)2 Security Congress in Orlando, Florida, on Tuesday, Bulumulle said that
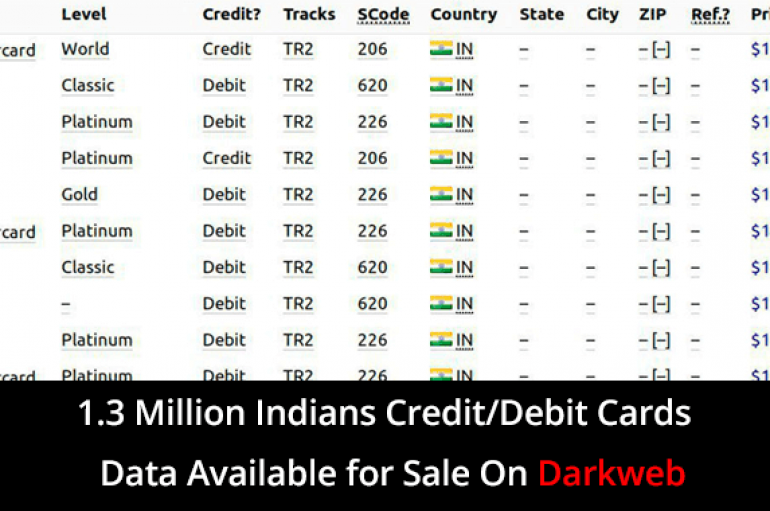
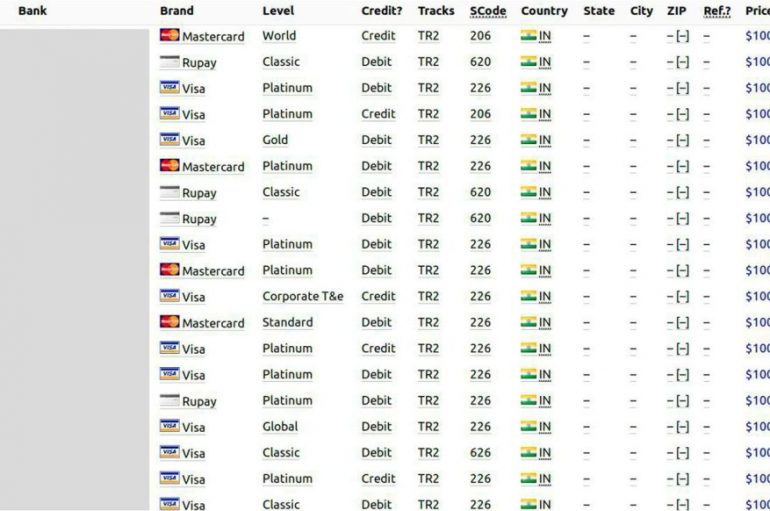
1.3 Million Indian’s Credit/Debit Card Data Available to Sale on Underground Darkweb Market
A huge database of more than 1.3 Credit and Debit Cards data put up for sale on Joker’s Stash, an infamous carding bazar that served as a distribution point for compromised payment card details. The Joker’s Stash market associated with
APT28 Hacking Group Attacking Sporting Organizations Around the World Using Custom Malware
Microsoft warns of cyberattacks targeting anti-doping authorities and sporting organizations around the world. The group active since 2004 and they target government, military, and security organizations. According to the Microsoft report, more than 16 national and international sporting and anti-doping
Microsoft has warned that Russian state-backed hackers are targeting sporting and anti-doping organizations yet again in the run up to the next Olympic Games in Tokyo. The group known as Strontium (aka APT 28, Fancy Bear), has been trying to
Attacks on integrity using AI and deepfakes, deployment of anti-surveillance technology and govermment interest in cybersecurity issues will be the main changes to the security industry next year, according to Forrester. The analyst firm’s 2020 predictions claimed that “integrity attacks”
In these hours an alleged cyber attack on the Kudankulam Nuclear Power Plant in Tamil Nadu made the headlines, but the KKNPP denies it. Worrying news made the headlines, the Kudankulam Nuclear Power Plant (KKNPP) was hit by a cyber
Thousands of websites and a national TV station have been taken out by a major cyber-attack in the eastern European nation of Georgia. The former Soviet nation has been left reeling after the apparently coordinated attack led to the defacement
Apparel site Sixth June has become the latest brand to suffer a digital skimming attack on its website, according to a security researcher. RapidSpike systems developer and researcher “Jenkins” took to Twitter yesterday to claim the firm had a live
Group-IB discovered details for 1.3 million Indian payment cards available for sale on Joker’s Stash, it is the largest card database ever Group-IB, a Singapore-based cybersecurity company that specializes in preventing cyberattacks, has detected that a huge database presumably holding
Lack of proper SaaS management in your IT department can expose your organization to a number of potential security loopholes and endpoint threats. It becomes difficult for IT departments to take action against these sorts of security gaps in their