Posts From CCME
Dexphot Polymorphic Malware Attacking Windows Computer to Mine Cryptocurrency and Monitor Services
A new malware strain dubbed Dexphot attacking windows computers to mine cryptocurrency, monitoring services, and scheduled tasks to rerun the infection if windows defender removed it. The malware uses filess techniques it gets malicious codes executed directly in memory and
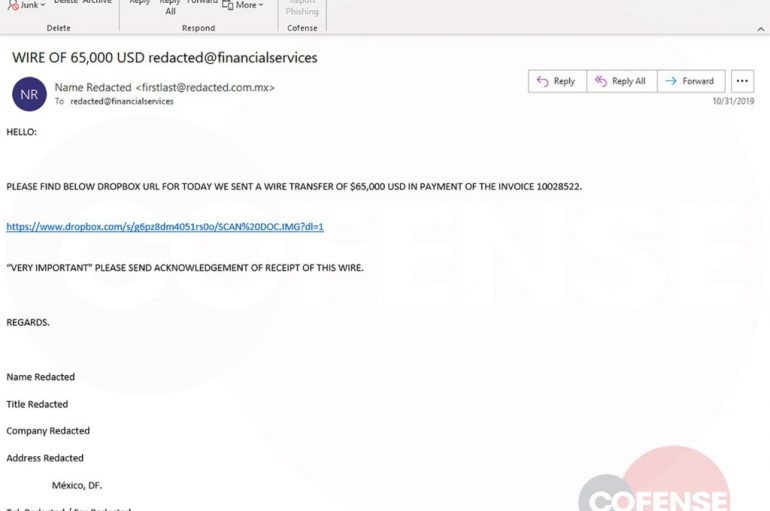
An IT services company has been hit with a $14 million ransom demand after suffering a major infection which could impact crucial patient care at many of its US nursing home clients, according to reports. Milwaukee-based Virtual Care Provider Inc.
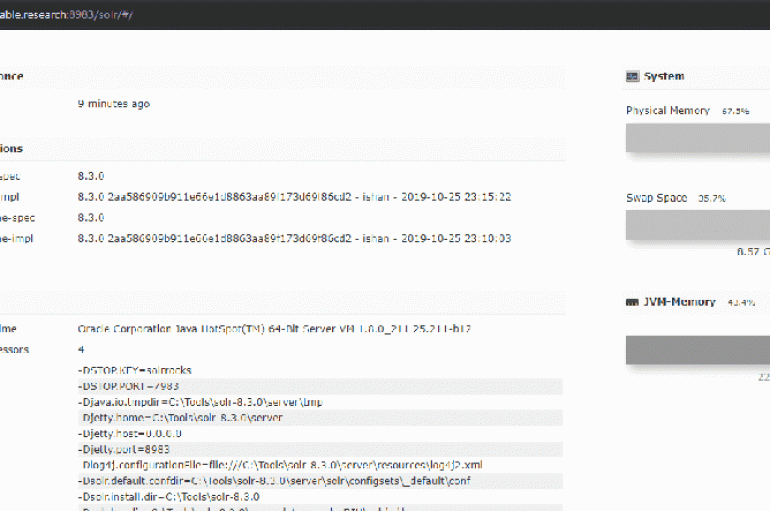
Over the summer, the Apache Solr team addressed a remote code execution flaw, not a working exploit code was published online. The bug addressed by the Apache Solr team fixed over the summer is more dangerous than initially thought. Apache
Frameworks like MITRE ATT&CK matrix are not just for large enterprises, and can be used by businesses small and large to better protect themselves and categorize attackers. Speaking at the SANS Cyber Threat conference in London, Katie Nickels, MITRE ATT&CK
Web Skimmers Use Phishing Tactics to Steal Data
Security researchers have discovered a new digital skimming attack which borrows phishing techniques to steal card data from a fake payments page. E-commerce sites often use secure payment pages hosted by third-party payment service providers (PSPs). However, attackers have used
Ransomware: Still Going Strong 30 Years On
Next month marks the 30th anniversary of the first ever ransomware attack, and according to new research this particular form of malware is still going strong. According to the “Mid-Year Threat Landscape Report” published yesterday by Bitdefender, ransomware increased 74.23%
Truecaller fixed a security flaw that may expose sensitive user data, location, and system information. The flaw was discovered by an India-based security researcher Ehraz Ahmed. Truecaller is the most popular smartphone app that includes features such as caller-identification, call-blocking,
Over One Billion Consumers Exposed in Data Leak
Personal information on over one billion individuals harvested by two data enrichment firms has been exposed online, according to security researchers. Data enrichment or aggregation providers effectively sell access to large stores of data merged from multiple third-party sources, primarily
The UK’s Ministry of Justice is inviting bids for the creation of a single, centralized cybersecurity log collection and aggregation platform. With a diverse digital estate and a wide variety of suppliers and technical systems, the MoJ is in need
A new malicious downloader dubbed “DePriMon” registers itself as fake Windows Default Print Monitor to achieve persistence and to execute commands as a SYSTEM user. The DePriMon malware found to be active at least from March 2017, it was detected
Twitter’s New 2FA Policy Tackles SIM Swap Risk
Twitter has finally remediated a two-factor authentication (2FA) security gap which could allow SIM swap attackers to unlock users’ accounts. Until now, the firm has mandated that all users wanting to use strong authentication on their accounts must first enable
Jamie Bartlett gave the closing keynote session, ‘Privacy, the Dark Web & Democracy: Uncovering the Digital Underworld,’ at the Infosecurity ISACA North America Expo and Conference in New York this week. Bartlett, a British author and journalist who specializes in
Raccoon Stealer Campaign Circumvents Microsoft and Symantec Anti-Spam Messaging Gateways
Crooks behind the Raccoon Stealer have adopted a simple and effective technique to circumvent popular anti-spam messaging gateways. Cybercriminals behind the Raccoon Stealer have adopted a simple and effective technique to circumvent Microsoft and Symantec anti-spam messaging gateways. The Raccoon
Researchers found 37 vulnerabilities in four common open-source VNC remote desktop applications that exist since 1999. These vulnerabilities allow attackers to compromise the targeted systems remotely. According to Kaspersky’s analysis, more than 600,000 VNC servers accessed remotely over the Internet,
Massive Data Leak – 1.2 Billion People Personal & Social Information That Consist of 4TB Data Exposed Online
Security researchers found an open Elasticsearch server that contains unique data sets of more than 1.2 billion users. The data found to associated with 2 different data enrichment companies. The data enrichment is a process of enhancing the data of
Half of global organizations still don’t have cyber insurance, despite the majority believing cyber-attacks will increase next year, according to FireEye. The security vendor polled 800 CISOs and senior executives across the globe to compile its new Cyber Trendscape Report.