Posts From CCME
It’s as complex to choose a hosting provider as developing an app or website. Additionally, it’s of paramount importance that you pick the perfect hosting provider. The reason being: you can’t switch from one hosting service to another without incurring
For most corporate denizens, security training is an unpleasant but necessary evil, but does it have to be? Not according to Kris Martel, CISO of Imagine IT, who uses a highly interactive approach to create an engaging, entertaining learning environment
Speaking at Infosecurity ISACA North America Expo and Conference in New York, Tony Rock, chief operating officer at Lockpath, discussed the challenges many security departments face in building a business case to communicate their risk management and security programs. “Our
Startpage.com has created a private News tab that allows users to search the internet without logging in or sharing any personal information. The Dutch company launched the News tab today as an additional feature of its existing private browsing extension.
ESET researchers discovered a new downloader, dubbed DePriMon, that used new “Port Monitor” methods in attacks in the wild. The new DePriMon downloader was used by the Lambert APT group, aka Longhorn, to deploy malware. According to a report published
The US Commonwealth of the Northern Mariana Islands (CNMI) is to welcome its first ever cybersecurity business next year. In a statement released today and published in the Marianas Variety, the CNMI Departments of Commerce and Labor announced that an
A detailed set of guidelines on what cybersecurity measures to take when handling arbitration was released today as part of New York Arbitration Week. The Cybersecurity Protocol for International Arbitration (2020) is the culmination of two years of work by
Speaking at Irisscon in Dublin, McAfee chief scientist Raj Samani said that ransomware has evolved from a one to one “relationship” between the author of the malware and the victim, to using more affiliates to distribute the malware. Citing the
Over two millions users of a gaming company and a cryptocurrency specialist have become the latest “netizens” to have their personal data compromised by attackers. The haul includes 1.4 million accounts from users of cryptocurrency wallet service GateHub, which were
Opening the 11th Irisscon conference in Dublin, Brian Honan, CEO of BH Consulting and head of the Irish Reporting and Information Security Service (IRISS), said that it is the same issues that continue to be a problem for businesses. Focusing
French Hospital Crippled by Ransomware
Patient care at a large hospital in northern France has suffered considerably after a major ransomware attack at the weekend, according to local reports. The University Hospital Center (CHU) of Rouen was hit by the malware last Friday and severely
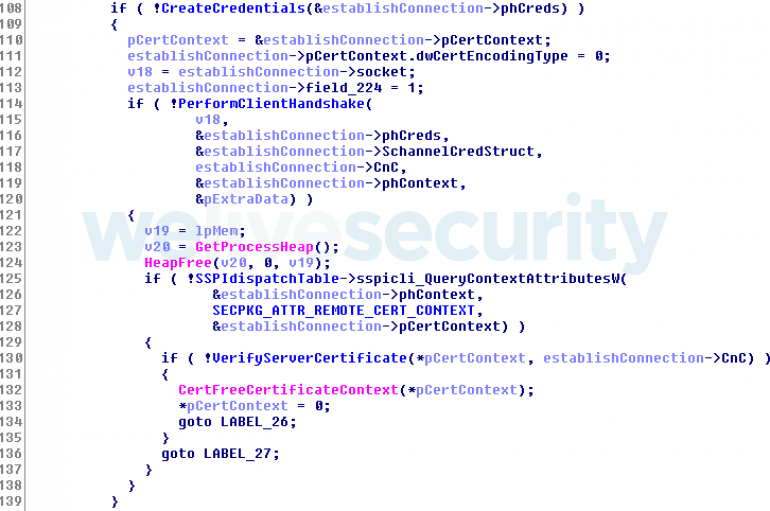
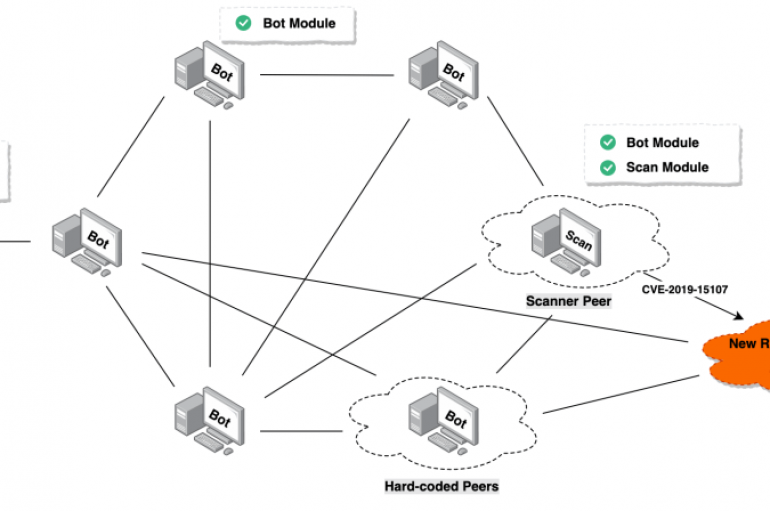
Security experts discovered a new peer-to-peer (P2P) botnet dubbed Roboto that is targeting Linux servers running unpatched Webmin installs. Researchers at 360Netlab discovered a new P2P botnet, tracked as Roboto, that is targeting Linux servers running unpatched installations of Webmin
A new wave of Roboto Botnet activities being discovered that attack the Linux Webmin servers by exploiting the RCE vulnerability using vulnerability scanning and P2P control module. Roboto Botnet initially detected via 360Netlab Unknown Threat Detection System as an ELF(
Microsoft Denies Bluekeep Ransomware Rumors
Microsoft has taken the unusual step of issuing a statement to deny what it claims to be misleading reports about a recent ransomware campaign. Stories emerged earlier this month that a number of organizations in Spain had been infected with
Cybersecurity Skills Shortage Tops Four Million
Global IT security skills shortages have now surpassed four million, according to (ISC)2. The certifications organization compiled its latest Cybersecurity Workforce Study from interviews with over 3200 security professionals around the world. The number of unfilled positions now stands at
Most Critical Docker Vulnerability Let Hackers To Take Complete Control Over Host & All Containers Within It
Researchers discovered a critical vulnerability in Docker that allows an attacker to take complete control of the host and the containers associated with it. The Docker vulnerability resides in the copy command (cp) used in containers platforms such as Docker,