Posts From CCME
A new risk index has named Alaska as the state most vulnerable to cybercrime. The index was created by payments platform Cardconnect using data published by the Federal Bureau of Investigation’s Crime Complaint Center. The company analyzed state-by-state statistics on
MixCloud Hacked – 20 Million+ Users Stolen Personal Records Selling in Dark Web for $4,000
MixCloud investigating a data breach that impacts more than 20 million registered users for the service. MixCloud is a popular music streaming service. The platform allows the listening and distribution of radio shows, DJ mixes, and podcasts which are uploaded
Security experts discovered an Android banking Trojan, dubbed Ginp, that steals both login credentials and credit card data. Security experts at ThreatFabric discovered an Android banking Trojan, dubbed Ginp, that steals both login credentials and credit card data. Ginp was
Vishing Attacks to Become Commonplace in 2020
Cybersecurity experts predict that voicemail phishing attacks, otherwise known as vishing, could become a daily occurrence in 2020. Threat research conducted by Mimecast found that malicious voicemail messages were not just on the rise, but were “evolving and more nuanced
Top 5 Best Cyber Attack Prevention Methods for Small Businesses With Breach & Attack Simulation
Cyber attack prevention for Small businesses very has to get serious about their cybersecurity. Hackers are now actively Performing Targeted cyber attack due to their weak security. In fact, 43 percent of cyberattacks today are aimed at smaller firms. Unfortunately,
A study conducted by cloud-based email security company Red Sift has found that only 12.5% of America’s top 100 retailers have taken steps to prevent fraudulent emails from landing in their customers’ inboxes. The worrying finding emerged after Red Sift
Magento Marketplace Breach Exposes User Details
Users of one of the world’s most popular e-commerce marketplaces have been informed that their account information may have been stolen after a data breach at the firm. The Adobe-owned Magento Marketplace offers thousands of free and premium extensions and
Security Giant Prosegur Struck by Ransomware
Private security giant Prosegur has become the latest multi-national to suffer operational problems after being struck by ransomware. The Spanish firm — which produces building alarms, and offers physical security services including cash transit vans — has over 60,000 employees
The first step for effective web design, as stated in an article by Forbes, is keeping the users in mind. This means creating a useful, fun, and engaging site, but above all, the website must keep users’ private data safe.
Security researchers are warning of an information stealing malware campaign that has already impacted hotel guest data in 12 countries worldwide. The RevengeHotels operation has been running since 2015 but recently expanded its presence this year, according to Kaspersky. It
American cybersecurity firm Palo Alto Networks has suffered a data breach after a third-party vendor accidentally published personal data regarding the firm’s employees online. The privacy of seven current and former employees of Palo Alto Networks was compromised in the
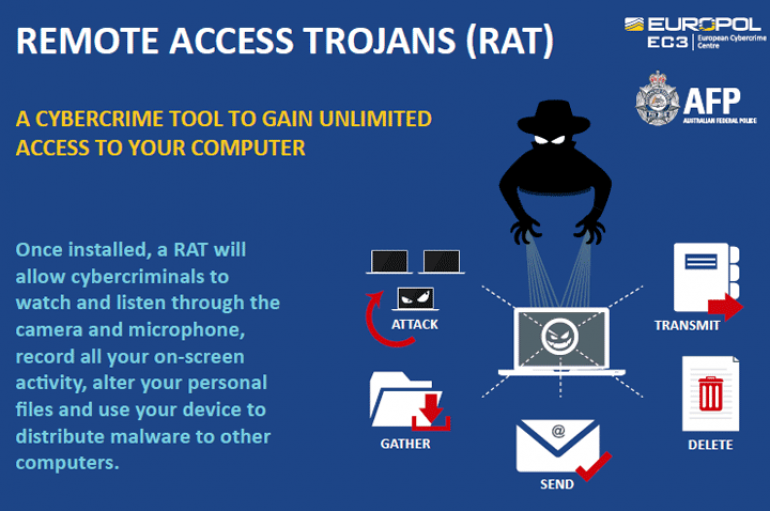
A successful new operation was announced by Europol, it announced to have dismantled the global organized cybercrime ring behind Imminent Monitor RAT. Europol announced to have dismantled the global organized cybercrime ring behind the Imminent Monitor RAT, The Imminent Monitor
RevengeHotels – Malware Attack Via Weaponized Word Documents to Steal Users Credit Card Data
A new malware campaign dubbed “RevengeHotels” targeting hotels, hostels, hospitality, and tourism companies worldwide aimed to steal credit card data of users and Travelers from hotel management systems. The campaign uses email as the main attack vector to deliver malware
Researchers discovered a new wave of spyware apps named Stalkerware emerging in wide for the past few months that spies victims’ online activities and steal sensitive data from the infected devices. Recently FTC warned that Retina-X developed and sold MobileSpy,
Global governments lose nearly $7 million on average from DNS attacks each year, the most of any sector, according to new research from EfficientIP. The DNS security vendor commissioned IDC to poll nearly 1000 IT and security leaders from North
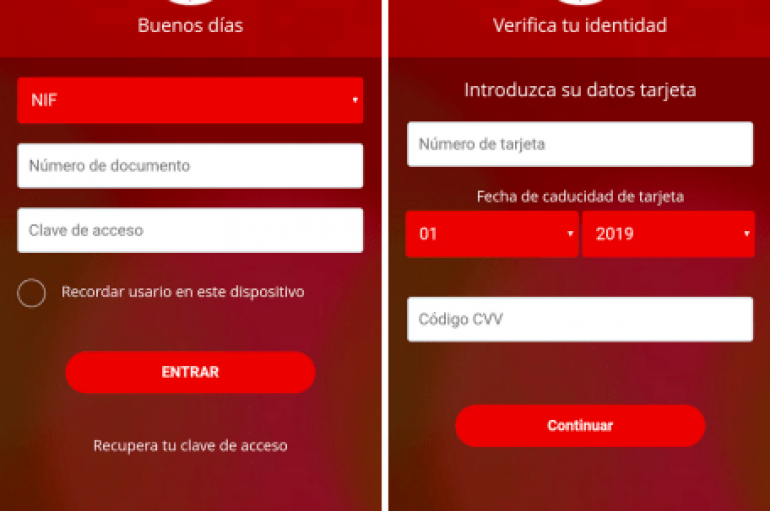
Adobe Hacked – Hackers Exploit The Bug in Magento Marketplace Gained Access To The Users Data
Adobe discloses the security breach on its Magento Marketplace portal, in results, attackers gained access to the registered customer’s sensitive account information. Adobe owned Magento is an open-source e-commerce and CMS platform written in PHP, and it was acquired for