Posts From CCME
The Home Office breached the GDPR 100 times in its handling of EU citizens’ data in the space of just five months, an inspector’s report has revealed. Between March 30 and August 31 2019 the government department admitted a catalog
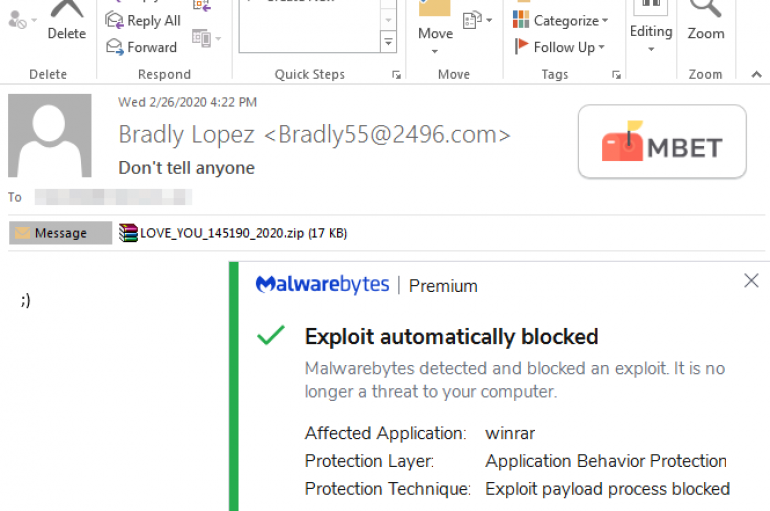
Nemty Ransomware “LOVE_YOU” Malspam Campaign
Security experts uncovered an ongoing campaign delivering Nemty Ransomware via emails disguised as messages from secret lovers. Researchers from Malwarebytes and X-Force IRIS have uncovered an ongoing spam campaign distributing the Nemty Ransomware via messages disguised as messages from secret
Researchers uncovered a new site take over the campaign that targeting WordPress websites by exploiting the multiple WordPress Plugin Zeroday vulnerabilities. 3 popular WordPress plug-ins are exploited as a part of this ongoing site take over attack campaign. Async JavaScript,
A researcher discovered a critical Account takeover vulnerability in Facebook’s Authorization feature “Login with Facebook” and, it allowed attackers to steal the Access_Token and completely take over the victim’s Facebook account. Facebook using OAuth 2.0 as an Authorization protocol that
Deep Web Search Engine is an alternative search engine when we need to search something, then Google or Bing will the first choice hit in mind suddenly. But unlike the Deep Web Search Engine, Google and Bing will not give
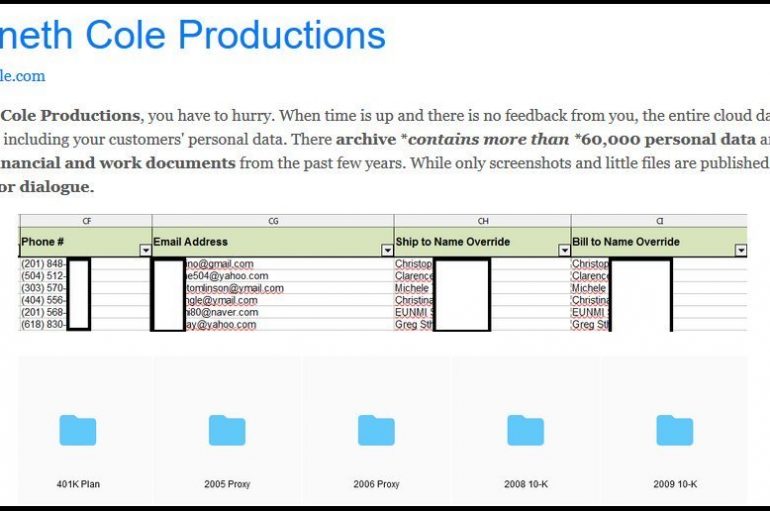
Not only Maze ransomware gang, the operators behind Sodinokibi Ransomware allegedly leaked the data of Kenneth Cole Productions. The operators behind Sodinokibi Ransomware have published the download links to archives containing data allegedly stolen from the US firm Kenneth Cole Productions. The
13-year-old Ghostcat Bug Affected Apache-Tomcat Let Hackers Remotely Inject Any Files in The Servers
Ghostcat, 13-Year old severe file inclusion vulnerability affected Apache-Tomcat server allows hackers to read or include any files in the web app directories of Tomcat remotely. Tomcat is one of the most popular Java middleware servers that used to deploy
A key highlight of any RSA Conference in San Francisco is the annual “Top 5 Most Dangerous New Attack Techniques and How to Counter Them” session led by experts from the SANS Institute. For the 2020 edition, however, many of
A data breach that exposed patients’ personal health information (PHI) for almost three months went undetected for half a year at a Michigan healthcare group. Hackers gained access to patient data placed in the safekeeping of Munson Healthcare Group by
Delivering a keynote talk at the RSA Conference in San Francisco, Mary T Barra, chairman and CEO of General Motors Company, said “all of you today are the best and strongest line of defense in this on going and even
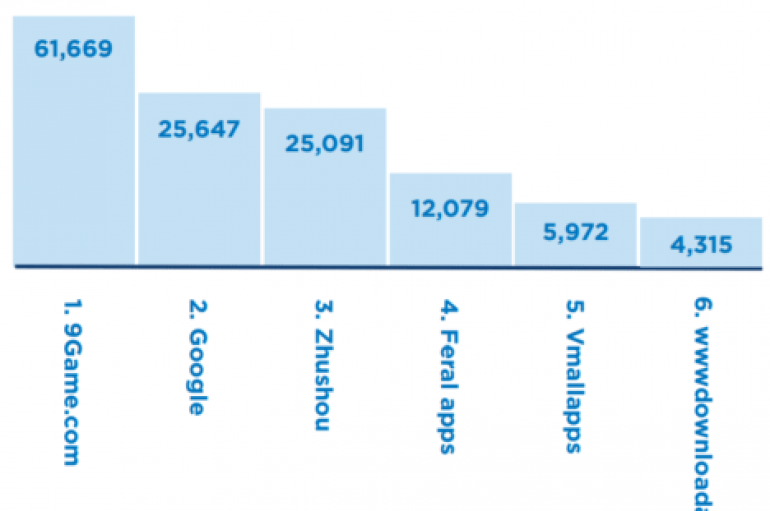
An interesting report published by RiskIQ on 2019 Mobile App Threat Landscape, lists the most dangerous mobile app store online. Mobile users downloaded over 200 billion apps in 2019 and the overall expense in app stores worldwide has been estimated
Free HTTPS tool Let’s Encrypt yesterday announced it has issued its billionth certificate, in what it claims to be a milestone for user privacy and security. Backed by the non-profit Internet Security Research Group (ISRG), the initiative has good reason
A US TV star has lost nearly $400,000 in a classic email fraud scam after a fraudster persuaded her bookkeeper to wire funds to a new bank account. Multi-millionaire Barbara Corcoran describes herself as an “NYC real estate queen” and
Iranian APT Hackers Attack Government Organizations via Weaponized Excel Files to Steal Network Credentials
Researchers observed a new malware called ForeLord from the Iranian APT hackers via weaponized MS excel document to attacker government organizations. Iranian Threat group called COBALT ULSTER aka MuddyWater, Seedworm, TEMP.Zagros is behind this attack and believed to be a
Speaking in a keynote talk at the RSA Conference in San Francisco, Mary T. Barra, chairman and CEO of General Motors Company, said that she acknowledged that “no one in this room needs convincing that there are virtually no industries
#RSAC: How to Hack Society
The method, procedures, and practices used by cybersecurity professionals have relevance beyond just the technology sphere; they can also be used to hack society. That’s the view espoused by Bruce Schneier, security technologist, researcher, and lecturer at the Harvard Kennedy