Posts From CCME
CIA Hacking Unit APT-C-39 Hit China Since 2008
Chinese security firm Qihoo 360 revealed that the US CIA has hacked Chinese organizations in various sectors for the last 11 years. Chinese security firm Qihoo 360 is accusing that the US Central Intelligence Agency (CIA) of having hacked Chinese organizations for the last
Google Patches the Critical MediaTek rootkit Vulnerability that Affects Millions of Android Devices
Google patches a critical vulnerability with MediaTek rootkit chips that affect millions of devices with chipsets from MediaTek. MediaTek is a large Taiwanese chip design company that provides chips for wireless communications, High-definition television, and devices like smartphones and tablets.
As the value of data increases, those with top-level access are fast becoming the target of choice. Here’s how, why, and what to do about it… In the digital era, data is big business. Recent studies have shown that just
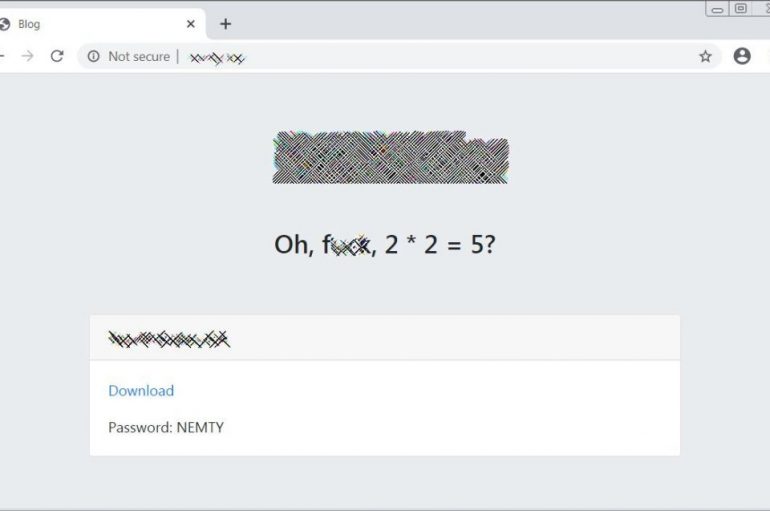
The operators behind the Nemty ransomware set up a data leak site to publish the data of the victims who refuse to pay ransoms. Nemty ransomware first appeared on the threat landscape in August 2019, the name of the malware comes after the
SpaceX Contractor Hit by Data Breach
An aerospace and industrial manufacturer has become the latest firm to have sensitive internal documents published online by ransomware attackers. Visser Precision, which makes parts for Tesla and SpaceX as well as defense contractors Boeing and Lockheed Martin, was hit
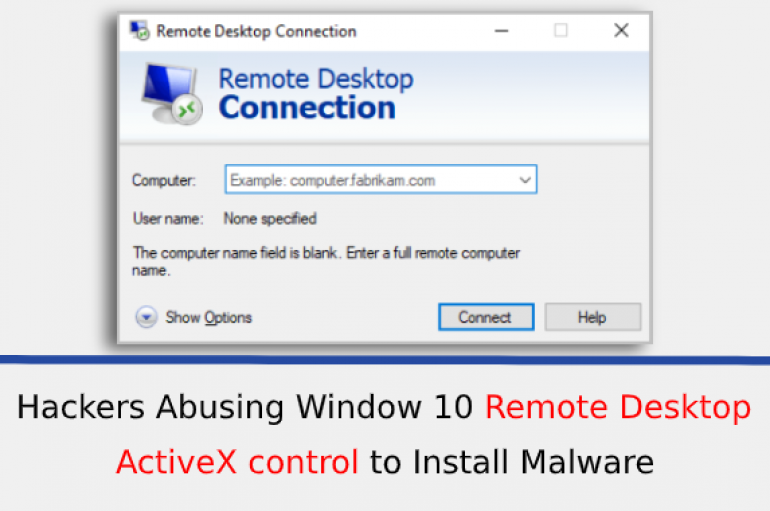
Hackers Abusing Window 10 Remote Desktop ActiveX control to Install New Version of Trickbot Malware
Researchers observed a new wave of infamous Trickbot Malware campaign via a dozen of malicious documents and infect the Windows users by abusing Remote Desktop ActiveX Control. TrickBot is one of the top modular banking malware that primarily targets financial
Pharmacy store chain Walgreens has disclosed a data breach that impacted some customers of its mobile application. Pharmacy store chain Walgreens has disclosed a data breach that impacted some customers of its mobile application. The mobile app allows users to
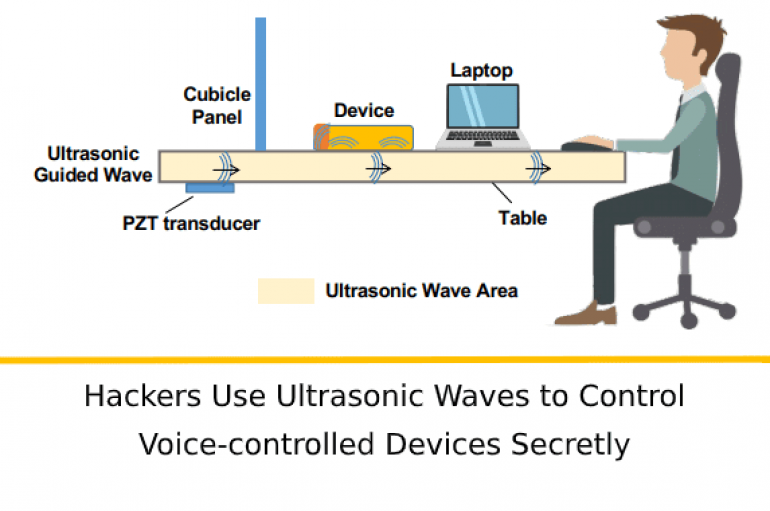
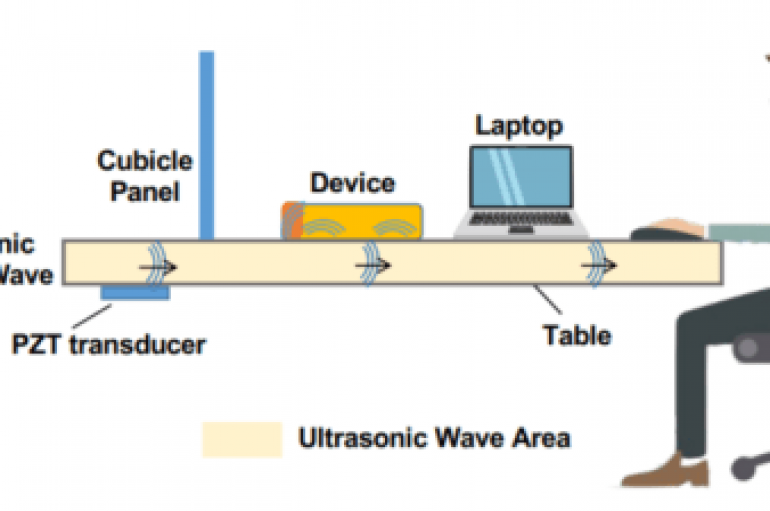
SurfingAttack – Hackers Use Ultrasonic Waves to Control Voice-controlled Devices Secretly
Researchers discovered a new attack method dubbed SurfingAttack that enables the attacker to control the voice-controlled device from over a longer distance. With this attack method attackers can hijack a mobile Short Message Service (SMS) passcode, making ghost fraud calls
A security company has accused America’s Central Intelligence Agency (CIA) of waging an 11-year campaign of cyber-espionage against critical industries in the People’s Republic of China. Qihoo 360 announced yesterday that it had “discovered and revealed cyber-attacks by the CIA
Experts from Cybaze/ Yoroi Zlab spotted a new sample of the Karkoff implant that was employed in past campaigns associated with Iran-linked APT34 group. In November 2018, researchers from Cisco Talos tracked and detailed a “DNSEspionage” campaign against targets in
America’s second-largest pharmacy store chain has disclosed an app error that let customers view the private personal messages of other customers. For nearly a week last month, users of the Walgreens mobile app were able to view the first and
Thoma Bravo Acquires Sophos for $3.9bn
British cybersecurity company Sophos announced today that its acquisition by Thoma Bravo is now complete. The private equity firm snapped up the company in a cash transaction that values Sophos at $3.9bn. Under the terms of the agreement, Sophos stockholders
Data of 10K Rail Passengers Exposed
The personal data of 10,000 UK rail passengers has been exposed after a Wi-fi provider left a database unsecured online. C3UK provides passengers with free Wi-fi at railway stations across the UK. The company admitted failing to secure a database
SurfingAttack is an attacking technique that allows to wake up mobile device and control them using voice commands encoded in ultrasonic waves. SurfingAttack is a hacking technique that sees voice commands encoded in ultrasonic waves silently activate a mobile phone’s
HMRC Scam Calls Surge 234% in a Year
The volume of HMRC phishing emails reported by the public has fallen sharply over the past two years, as those related to SMS- and phone-based scams increased, according to a new Freedom of Information (FOI) request. UK-based Griffin Law obtained
The UK parliament has invoked the spirit of Guy Fawkes in a bid to improve cybersecurity awareness among lawmakers. A reported newsletter update sent to members of the House of Lords warned that the infamous Gunpowder Plot to blow up