Posts From CCME
After three months from the first detection, the Lampion origin was identified. A webserver named “portaldasfinancas” is available in Turkey and has been used to spread the threat in Portugal. Lampion malware is the most critical malware affecting Portuguese users’ last
Criminals are using a combination of server exploitation, email, and voice calls to execute voice phishing attacks, often referred to as vishing. In a session at the RSA Conference in San Francisco, John LaCour, founder and CTO at PhishLabs, and
In a talk at the RSA Conference in San Francisco, Lexis Nexis Risk Solutions director of product management Daniel Ayoub and VP of product management Dean Weinert talked about the reality of which metrics and identifiers browsers release on users.
University Fools Hackers into Sharing Tactics
Researchers at the University of Texas have found a way to bamboozle malicious hackers into giving away their secrets. The DEEP-Dig (DEcEPtion DIGging) method tricks hackers onto a decoy site set up to record whatever sneaky tactics are thrown at
Last year’s data breach at the Desjardins Group will cost the co-operative far more than initially anticipated. Original estimates by the Quebec-based financial institution set the cost of recovering from the breach at $70m. The co-operative has now said that
Traditional organized crime gangs are now making efforts to succeed in financial cybercrime in Latin America. According to research by IntSights into cybercrime activities in central and south America, persistent cyber-criminals are operating extensive schemes targeting banks, hospitality services,and retail
America’s Democratic National Committee has warned its electoral candidates to be wary after a phony Bernie Sanders campaign staffer used a fake domain to contact other political campaigns. The cyber-imposter attempted to set up conversations with at least two other
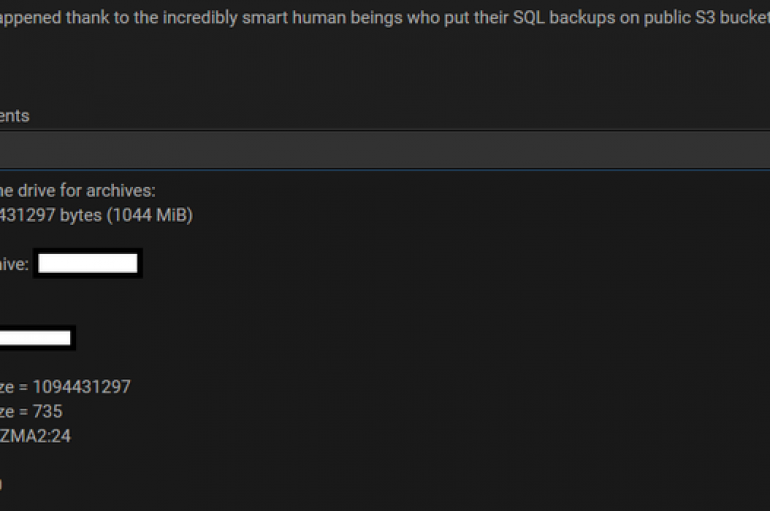
Hackers share SQL databases from unsecured AWS buckets, including the archive belonging to the BGR tech news site in India. Hackers are sharing SQL databases from unsecured Amazon S3 buckets, one of them belongs to the BGR tech news site
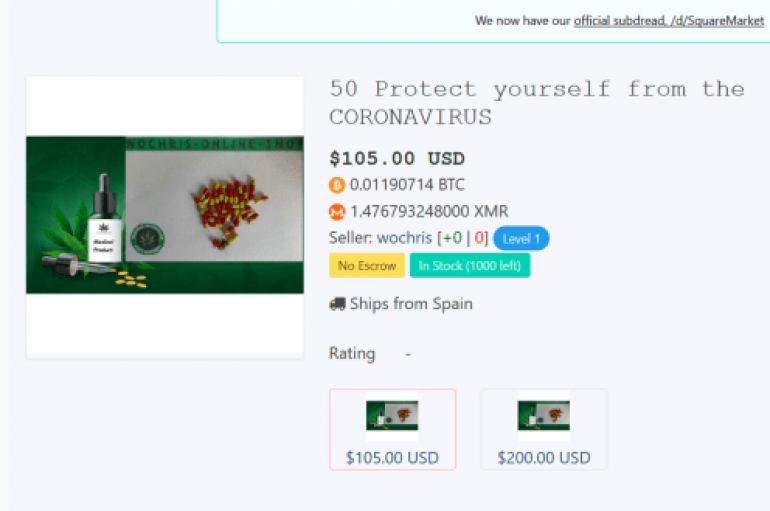
Hunting the Coronavirus in the Dark Web
Let me share with you the result of a one-night long analysis of major black marketplaces searching for anything related to the coronavirus epidemic. Recently I have received many questions from journalists and colleagues about the activity in the dark
Academic researchers discovered a new form of IMPersonation Attacks in 4G LTE networks called IMP4GT allowed attackers to exploit the missing integrity protection for user data and injecting malicious Arbitary packets by impersonating the victims. 4G Long Term Evolution (LTE)
Google revealed that the enhancements to its scanning system implemented in Gmail are boosting its detection capabilities. Google announced that the new scanning capabilities implemented in Gmail have increased the detection rate of malicious documents. The IT giant proudly announced
A controversial facial recognition company has just informed its customers of a data breach in which its entire client list was stolen. Clearview AI leapt to fame in January when a New York Times report claimed that the start-up had
A notorious group behind digital skimming attacks has upped its game recently, infecting at least 40 new websites, according to researchers. Magecart Group 12, one of many collectives using techniques designed to harvest card details from e-commerce websites, continues to
Now is the time to review your exposure to GDPR and CCPA-related lawsuits, and review contracts related to penetration testing. In a talk at RSA Conference in San Francisco exploring recent cyber-related court cases, Julia Bowen, senior vice-president, general counsel
A Guide to Building a Cyber Security Strategy On Your Organization Against The Security Breach
Everything that can be hacked will be hacked, or at least someone will try. Over the past few years, we have seen massive data breaches where hackers have stolen petabytes of confidential and often personal data from companies that customers
Kr00k – New Wi-Fi Vulnerability Let Hackers Decrypt WPA2-Encrypted Traffic – Billion of Devices Affected
Kr00k, a security flaw in Wi-Fi chips allows attackers to decrypt the WPA2-encrypted traffic. The vulnerability affects Broadcom and Cypress chips, these are the most common chips used by several client devices including top brands such as Amazon (Echo, Kindle),