Archive
Hackers Behind DNSpionage Created a New Remote Admin Tool for C2 Server Communication Over HTTP and DNS
Threat actors behind the new malware campaign DNSpionage created a new remote administrative tool that supports HTTP and DNS communication with C&C Server that operates by attackers. Based on a recent incident, the DNSpionage campaign which is developed and operates
Hackers use malicious MSI files that download and execute malicious files that could bypass traditional security solutions. The dropped malware is capable of initiating a system shutdown or targeting financial systems located in certain locations. Security researchers from TrendMicro discovered
A new report from Blancco Technology Group has warned that those looking to make some money by selling used storage drives may be putting themselves at risk of falling victim to cybercrime. As detailed in Privacy for Sale: Data Security
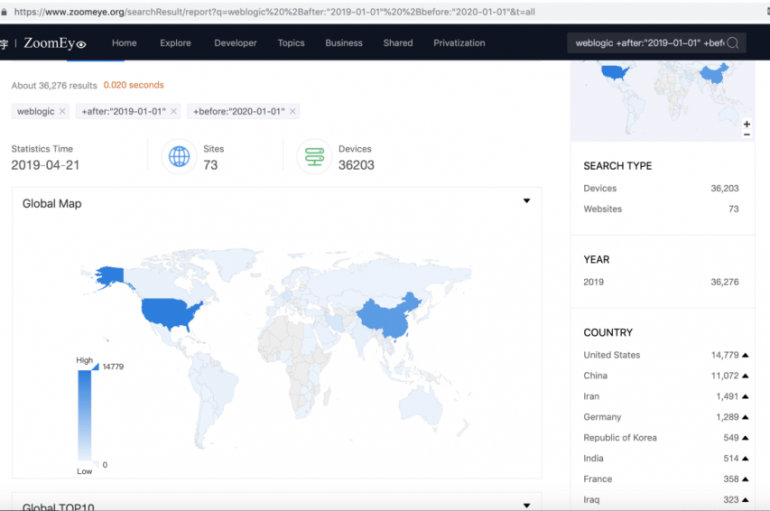
New Zero-day flaw discovered in Oracle Web logic server let attackers exploit this vulnerability to remotely execute commands without authorization. An Oracle web Logic component wls9_async and wls-wsat trigger this deserialization remote command execution vulnerability and it affects all the
Insider Threats a Top Risk to Healthcare
Across the healthcare sector, ransomware is reportedly no longer the most prevalent security threat, according to new research from Vectra that found attacks decreased during the second half of 2018. The Vectra 2019 Spotlight Report on Healthcare found that internal
Cybercriminals abusing Google sites via drive-by download attack to host dubbed “LoadPCBanker” banking malware to steal various sensitive data from compromised victims. Threat actors abusing Google sites file cabinets template and use it as a delivery medium and SQL as an
Another city fell victim of a malware attack, systems at the city of Stuart, Fla., were infected by the Ryuk ransomware on April 13, 2018. Law enforcement is investigating a ransomware attack that hit the City of Stuart on April
Online Fitness Store Gets One-Upped by Hackers
Lifting weights might build strength for the body, but for customers of Bodybuilding.com, bulking up wasn’t enough to stop hackers from stealing their personal data. According to a security notice issued by the popular online fitness store, Bodybuilding.com recently experienced
50 Malicious Android Apps Bypassed Google Play Protection and Infected 30 Million Android Users
More than 50 malicious apps with more than 30 Million installations found on Google play, that display annoying ads and in some cases, it convinces the user to install other apps. According to Avast, all the malicious apps are linked
An individual or group of hackers have managed to amass over $54m in stolen digital currency by raiding digital wallets improperly secured with private keys, according to a new report. Consultancy Independent Security Evaluators (ISE) claimed the “Blockchainbandit” had taken
Zero-Day Vulnerability in Oracle WebLogic
Security experts are warning of a dangerous zero-day remote code vulnerability that affects the Oracle WebLogic service platform. Oracle WebLogic wls9_async and wls-wsat components are affected by a deserialization remote command execution zero-day vulnerability. New Oracle #WebLogic #RCE #Deserialization 0-day
Hackers Using Weaponized TeamViewer to Attack & Gain Full Control of the Government Networks
Researchers spotted a new wave of cyber attack from Russian speaking hacker who uses the weaponized TeamViewer to compromise and gain the full control of the Government network systems. Teamviewer is the most popular tool used for remote Desktop control,
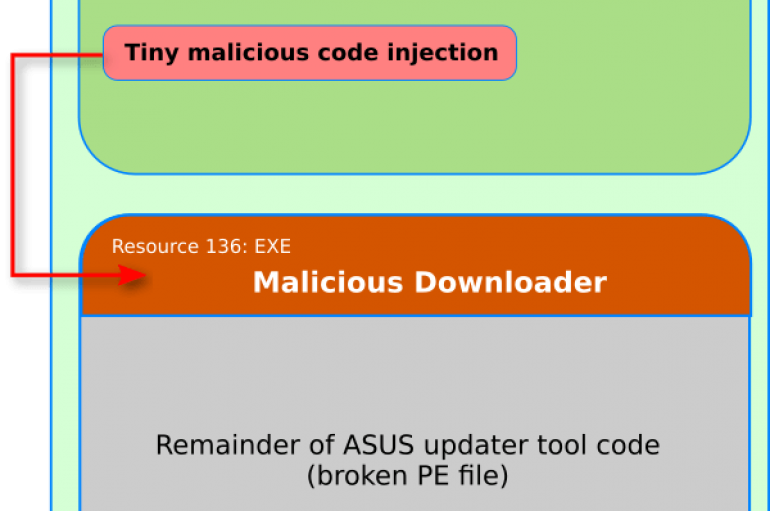
Experts at Kaspersky Lab linked the recent supply-chain attack targeted ASUS users to the “ShadowPad” threat actor and the CCleaner incident. Security researchers at Kaspersky Lab linked the recent supply-chain attack that hit ASUS users (tracked as Operation ShadowHammer) to
Magecart Swoops in to Strike Atlanta Hawks Shop
The online shop for the Atlanta Hawks currently states that it is temporarily down for maintenance, and according to Sanguine Security, the ecommerce site is the latest victim of a Magecart attack. In the wild, hawks hold their place at
New Malware attack campaign dubbed “Aggah” targeting various countries via weaponized Word documents and infect the victims by dropping the available RevengeRAT from Pastebin. Researchers from Palo Alto recently observed the largest malware campaign via telemetry and they named as
A Wi-Fi hotspot app exposed more than two million Wi-Fi network passwords from its unprotected database. The app named WiFi Finder, downloaded by thousands of users to locate and connect with Wi-Fi hotspots, the app also stores Wi-Fi password and