US Utilities Targeted with LookBack RAT in a New Phishing Campaign
Security experts at Proofpoint observed a new wave of phishing attacks aimed at US Utilities in an attempt to deliver the LookBack RAT.
Security experts at Proofpoint have discovered a new series of phishing attacks targeting entities US utilities in an attempt to deliver the LookBack RAT.
In early August, the expert reported that between July 19 and July 25, 2019, several spear-phishing emails were identified targeting three US companies in the utility sector. The phishing messages were impersonating a US-based engineering licensing board with emails originating from what appears to be an actor-controlled domain, nceess[.]com. Nceess[.]com is believed to be an impersonation of a domain owned by the US National Council of Examiners for Engineering and Surveying. Threat actors weaponized Word documents used to download and execute the LookBack RAT, a new remote access Trojan (RAT).
Now ProofPoint experts warn of a new wave of attacks carried out between August 21 and August 29, the threat actors targeted other organizations in the same sector. This time the attackers used phishing emails impersonating a licensing body related to the utilities sector.
The experts reported that at least 17 entities in the US utilities sector have been targeted by these attackers from April 5 through August 29, 2019.
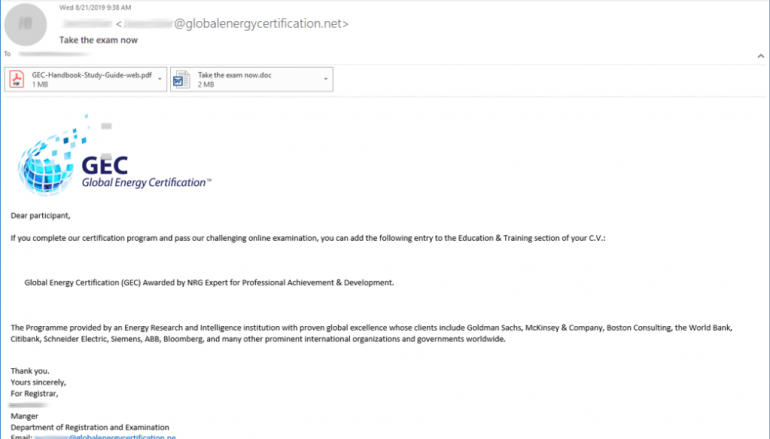
“The phishing emails originated from what appears to be an actor-controlled domain: globalenergycertification[.]net. This domain, like those used in previous campaigns, impersonated a licensing body related to the utilities sector.” reads the post published by Proofpoint. “In this case, it masqueraded as the legitimate domain for Global Energy Certification (“GEC”). The emails include a GEC examination-themed body and a malicious Microsoft Word attachment that uses macros to install and run LookBack.”
The tactics, techniques, and procedures (TTPs) observed in these attacks are consistent with phishing campaign reported in early August.
The analysis of the attacks allowed the researchers to uncover a reconnaissance activity conducted prior to the launch of the phishing campaigns. The attackers used a staging IP, the scanning targeted SMB over IP via port 445 for up to two weeks prior to the sending of the phishing emails.
“This is a newly identified TTP not disclosed in our initial publication regarding LookBack.” continues the post. “Observed scanning IPs in some instances have also hosted phishing domains prior to their use in phishing campaigns.”
The phishing messages were sent from an email address at the domain globalenergycertification[.]net in the attempt to trick victims into believing that they were sent by the official GEC website. The malicious messages invited recipients to take the GEC exam administered by the Energy Research and Intelligence Institution.

The weaponized attachments titled “take the exam now.doc” contained VBA macros to install LookBack, the macro is quite similar to the one involved in the previous campaign. The phishing emails also had a legitimate and benign PDF file attached. Designed for exam preparation, the PDF was hosted on the legitimate GEC site.
Once the victim opened the attachment, the macro installs several privacy-enhanced mail (PEM) files on the host that are both malware modules and macro variables.
The macro drops a version of certutil.exe on to the victim’s machine , and leverages it to decode the following initial files:
- Pense1.txt contains variables specific to the creation of the GUP proxy tool
- Pense2.txt pertains to the libcurl.dll downloader
- Pense3.txt appears to be run alongside pense2.txt.
Experts observed that threat actors modified the macros in the recent attacks, they added additional variables likely in the attempt obfuscating the code. The C&C server used in this campaign was 103.253.41[.]45, that is the same used by the threat actors in the previous attacks.
“The evolution of TTPs including updated macros demonstrates a further departure from tactics previously employed by known APT groups. However, at the current moment, the creators of LookBack malware are yet to depart from their persistent focus on critical infrastructure providers in the United States,” Proofpoint concludes.
This post US Utilities Targeted with LookBack RAT in a New Phishing Campaign originally appeared on Security Affairs.





