U.S. Taxpayers Hit by a Phishing Campaign Delivering the Amadey Bot
Cofense researchers spotted a phishing campaign that is targeting taxpayers in the United States to infect them with the Amadey malware.
Security experts at Cofense uncovered a phishing campaign that is targeting taxpayers in the United States attempting to infect them with a new piece of malware named Amadey.
The Amadey bot is a quite simple piece of malware that is available for hire for cybercriminals. Experts revealed that the botnet was used by the TA505 cybercrime gang to distribute the FlawedAmmy RAT and some email stealers.
“The Cofense Phishing Defense CenterTM has detected a new wave of attacks targeting the US taxpayer by delivering Amadey botnet via phishing emails.” reads the analysis published by Cofense. “Amadey is a relatively new botnet, first noted late in Q1 of 2019. Known for its simplicity, it is available to hire for a very steep price compared to other commercially available botnets with similar functionality.”
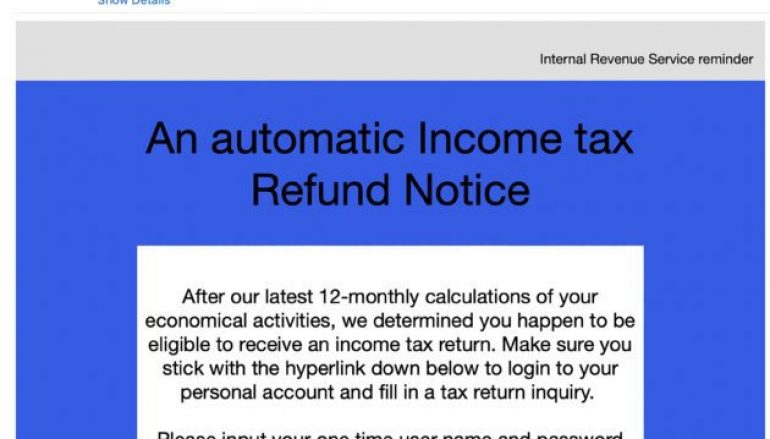
The phishing messages used in this campaign purport to be from the Internal Revenue Service (IRS), they claim that the recipient is eligible for a tax refund.

In classic social engineering attack, the phishing message presents a “one time username and password” to the victims and urges the user to click the “Login Right Here” button.
The login button is an embedded Hyperlink that points to hxxp://yosemitemanagement[.]com/fonts/page5/, a page designed to display a fake IRS login page.
Once provided the login credentials, the user will be informed of a pending refund and will be asked to download a document, print and sign it. The signed document has to be sent or uploaded to the portal. Experts discovered that when the user attempts to download the document, he will download a ZIP file that contains a highly obfuscated script dropper written in Visual Basic.
The VBScript drops an executable that downloads and executes another executable. To Amadey malware achieves persistence by setting up a registry entry using the Reg.exe command-line tool.
Once the installation process is concluded, the Amedey bot connects to one of the command and control (C&C) servers via HTTP on port 80 and sends it system diagnostic information, then it waits for further instructions.
The Amedey malware sends back to the server several data, including a unique identifier of the infected system, the malware version, operating system, antivirus software, system name, and username.
The analysis published by Cofense includes the Indicators of Compromise (IoCs).
This post U.S. Taxpayers Hit by a Phishing Campaign Delivering the Amadey Bot originally appeared on Security Affairs.





