Talos Discovered Spelevo EK, An Exploit Kit Spreading via B2B Website
Researchers at Cisco Talos group have discovered a new exploit kit dubbed Spelevo that spreads via a compromised business-to-business website.
Malware researchers at Cisco Talos have discovered a new exploit kit dubbed Spelevo that spreads via a compromised business-to-business website.
The popularity of EK rapidly decreased with the demise of the Angler Exploit Kit, but the discovery of the Spelevo exploit kit demonstrates that crooks continue to leverage on EKs to deliver malware.
Threat actors compromised a website to spread the Spelevo EK, they added only four lines of code that allowed to hack visitors with poor security hygiene.
“Today, Cisco Talos is unveiling the details of a new exploit kit campaign that proves exploit kits are still a threat and should be taken seriously by defenders: Spelevo.” reads the analysis published by Cisco Talos. “This recent campaign leveraged a compromised business-to-business site to deliver Spelevo, one of the first new kits we’ve seen in months.”
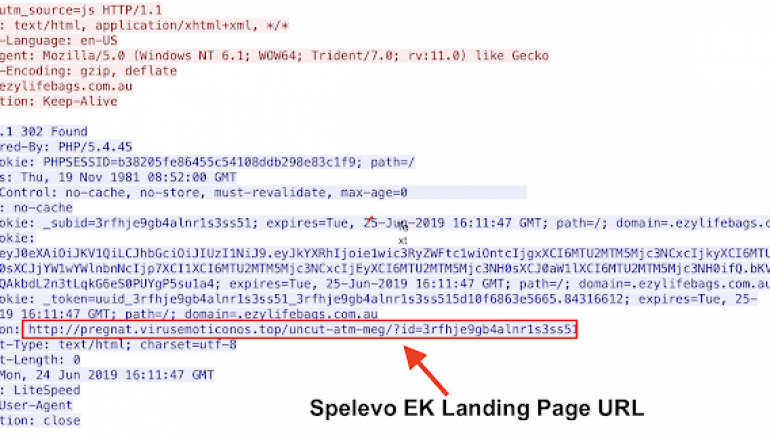
Attackers infected multiple pages on theB2B site were, and all of them were redirecting to the infection gate used for the campaign.
The gate is being hosted at ezylifebags[.]com[.]au, but experts also noticed a request for another JavaScript file being hosted at your-prizes-box[.]life.
“However, this request doesn’t result in anything but additional requests for the same file via 301 redirect and could be used as an additional tracker to ensure the victim is getting to the gate via the proper channels, a compromised website, and are not direct connects from researchers.” continues the experts.
The Spelevo’s attack chain begins with a request for the landing page, where an initial reconnaissance activity is performed. The malicious code collects information on the infected systems, including operating system, web browser, and applicable plugins.

The malware first attempts to exploit the CVE-2018-15982 is a vulnerable version of Adobe Flash was found, otherwise, the EK attempts to exploit a use-after-free in the VBScript engine of Internet Explorer tracked as CVE-2018-8174.
Once compromised the system, the Spelevo EK redirects the victim to Google. The user would notice a browser tab opening to load the infection gate, followed by the landing page, an exploit page, and then Google.
“Once the system has been compromised and the payload is delivered, Spelevo does something a bit novel for exploit kits: It redirects to Google, post compromise. The practical effect of which is that a user would see a tab open which loads the gate, followed by the landing page, an exploit page, and then finally to Google.” continues the analysis.
The campaign observed by Talos that involved the Spelevo EK was observed delivering the IcedID and Dridex Trojans.
Since its discovery, operators behind Spelevo have already implemented some minor changes, including modification of URL structure and some obfuscation changes in the landing and exploit pages themselves.
Unlike the Rig exploit kit, Spelevo is being hosted using domains instead of hard coded IP addresses, the operators behind the recently discovered EK leverage domain shadowing for that.
“In much the same way that we see old threats like MyDoom and Stuxnet circulating on the internet today, exploit kits will be a permanent part of the threat landscape.” Talos concludes. “They are still incredibly effective at leveraging existing vulnerabilities to randomly compromise victims on the internet to deliver a malicious payload,”
This post Talos Discovered Spelevo EK, An Exploit Kit Spreading via B2B Website originally appeared on Security Affairs.





