Skidmap Linux Miner Leverages Kernel-Mode Rootkits to Evade Detection
Trend Micro researchers spotted a piece of Linux cryptocurrency miner, dubbed Skidmap that leverages kernel-mode rootkits to evade the detection.
Skidmap is a new piece of crypto-miner detected by Trend Micro that target Linux machines, it uses kernel-mode rootkits to evade the detection.
This malware outstands similar miners because of the way it loads malicious kernel modules to evade the detection.
The crypto-miner set up a secret master password that uses to access any user account on the system.
“These kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — attackers can also use them to gain unfettered access to the affected system. A case in point: the way Skidmap can also set up a secret master password that gives it access to any user account in the system.” states the analysis published by TrendMicro. “Conversely, given that many of Skidmap’s routines require root access, the attack vector that Skidmap uses — whether through exploits, misconfigurations, or exposure to the internet — are most likely the same ones that provide the attacker root or administrative access to the system.”
Experts noticed that several routines implemented by Skidmap require root access, suggesting that its attack vector is the same that provided the attackers with root or administrative access to the system.

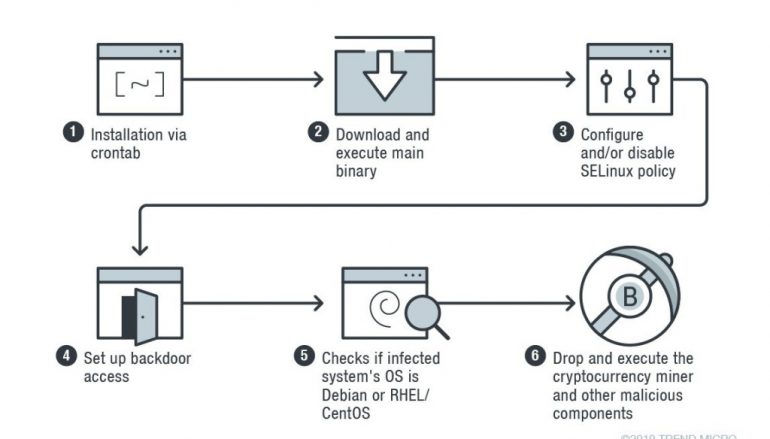
The infection chain sees the Skidmap miner installing itself via crontab, then the malicious code downloads and executes the main binary. The malware decreases the security settings of the target systems by configuring the Security-Enhanced Linux (SELinux) module to the permissive mode or by disabling the SELinux policy and setting selected processes to run in confined domains. The miner also set up backdoor access to the infected system.
Skidmap also provides attackers with backdoor access to the infected machine.
“Skidmap also sets up a way to gain backdoor access to the machine. It does this by having the binary add the public key of its handlers to the authorized_keys file, which contains keys needed for authentication.” continues the report.
“Besides the backdoor access, Skidmap also creates another way for its operators to gain access to the machine. The malware replaces the system’s pam_unix.so file (the module responsible for standard Unix authentication) with its own malicious version”
The main binary checks whether the system runs on Debian or RHEL/CentOS, then drops the miner and other for the specific Linux distro.
Trend Micro experts revealed that the Skidmap miner has notable components designed to obfuscate its activities and ensure that they continue to run. Samples of these components are:
A fake “” binary that replaces the original, once executed it will randomly set up a malicious cron job to download and execute a file.
Another component is “kaudited,” s file installed as /usr/bin/kaudited that drops and installs several loadable kernel modules (LKMs). The kaudited binary also drops a watchdog component used to monitor the mining process.
Trend Micro also described the “iproute” module that hooks the system call getdents that is normally used to read the contents of a directory, with the intent of hiding specific files.
The last component is “netlink,” a rootkit that can fake the network traffic statistics and CPU-related statistics to hide the activity of the malware.
“Skidmap uses fairly advanced methods to ensure that it and its components remain undetected. For instance, its use of LKM rootkits — given their capability to overwrite or modify parts of the kernel — makes it harder to clean compared to other malware.” Trend Micro concludes. “In addition, Skidmap has multiple ways to access affected machines, which allow it to reinfect systems that have been restored or cleaned up,”
This post Skidmap Linux Miner Leverages Kernel-Mode Rootkits to Evade Detection originally appeared on Security Affairs.