
Ransomware’s next target: Your car and your home
Cybersecurity researchers have demonstrated how vulnerabilities in everyday connected devices can allow hackers to hold whole areas of your life to ransom.
It’s possible, especially as vehicles’ systems become more interconnected on the inside –something like a sound system vulnerability could be potentially be used to access other in-car systems if vehicle manufacturers don’t take security seriously enough.
Unless there is clear separation between the engine control units and other systems, hackers could block out the entire car “so you’re not even going to get out of your driveway unless you pay,” says Samani. This could be a lucrative option for cybercriminals because, while people might be OK with losing some files if they don’t pay the ransom, when it comes to a car, they’re going to give in, he added.
“Quite frankly, if you’re sitting in your driveway in 2021 in a self-driving car, if you have to pay two Bitcoins to get to work, what are you going to do? Are you going to pay? Of course you will. If you’ve got a $60,000 connected car to drive you work and you’re being charged $200 to move? You’ll pay,” he says.
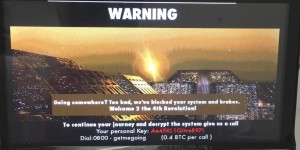
Ransomware in a connected car would render the vehicle useless until a ransom is a paid in this scenario mocked up by Intel. Image: Intel Security
Researchers have also demonstrated how it can be relatively simple for malicious hackers to infect a home router with ransomware — the one used during the research is available to buy from Amazon and over 100,000 have been sold.
The devices are shipped with some rather basic default login credentials, making it easy for cybercriminals to hack the system, simply by entering the default login and password. Anyone who wanted to try to infect this particular router could do so by searching for it on Shodan, the search engine for connected IoT devices.
Source | zdnet





