Over 23 Million Stolen Payment Card Data Traded on the Dark Web in H1 2019
According to a report published by cybersecurity firm Sixgill data for over 23 million payment card were on offer in underground forums in the first half of 2019.
A report published by cybersecurity firm Sixgill revealed that data for over 23 million payment card were offered for sale in the cybercrime underground.
The report, titled “Underground financial fraud report”, provides interesting details about the sale of stolen financial data in the Dark Web.
More than 15 million payment card were issued in the US, no other nation accounted for more than 10 percent of stolen card numbers. The second source of stolen payment card data is the U.K., while the number of stolen cards from Russia is virtually zero (only just 316 cards out of 23 million).
Despite the fight of law enforcement against the sale of stolen payment card data, certain websites continue to be important centers of this activity. The following graph shows that three trading posts accounted for 64 percent of the cards on offer during the first half of 2019.

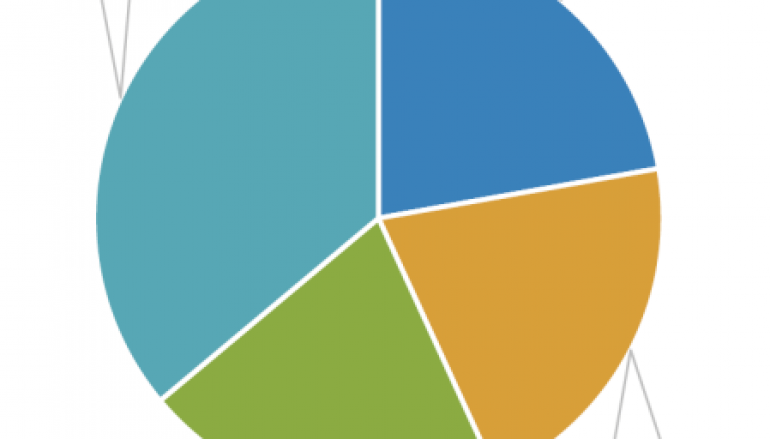
Giving a look at the details of stolen payment card data we can verify that 57 percent of stolen records are related to Visa cards, followed by Mastercard at 29 percent. AMEX accounted for 12 percent.
Crooks prefer to buy records containing CVV numbers (65%) instead of data dumps (35%) because the former could be used for online frauds, while the latter for in-store fraud using cloned cards. Compromised payment card data is sold on dark web markets for as little as $5
“Fraudsters have a number of illicit methods they use to steal card data. They place “skimmers” over the card readers on gas pumps and ATM machines. Retail workers and restaurant employees use devices to copy the swipes when they take a card for payment. They infect computers and other devices with malware to record payment information when their owners buy from ecommerce sites. Hackers infiltrate the networks of large companies and simply steal millions of records at a time.” states the blog post published by Sixgill.
“”CVV” information is sold with the three-digit number on the back of the card, which tend to be used in schemes in which criminals order things online. “Dumps,” which contain all of the information on the magnetic strip necessary to swipe, are used to replicate physical cards and make in-store purchases. Cards with CVV numbers were more popular, in part because the ability to fabricate new cards to be used in-person is far more difficult than using an ecommerce site.”
Experts pointed out that cyber criminals are moving outside traditional website-based markets, most of the illegal activities are passing through to Instant Relay Chat and encrypted Telegram channels. One IRC channel hosts a bot that is able to quickly validate stolen cards, and according to the experts, it was used more than 425,000 times in the first half of 2019.
“The centralization of fraudulent activity in a handful of markets mirrors similar economic and commercial patterns in real-world financial markets,” concludes the report. “This phenomenon may seem like a ripe opportunity for law enforcement agencies to effectively shut down a sizable portion of cybercriminal activity; however, as we’ve seen in the past with the shutting down of markets like Alphabay, Hansa, and Silk Road, threat actors quickly migrate their activities to other markets.”
This post Over 23 Million Stolen Payment Card Data Traded on the Dark Web in H1 2019 originally appeared on Security Affairs.