Latest News
#Infosec19: Threat Intel Sharing: The Future of Resilience, but Use with Caution
Speaking at Infosecurity Europe 2019 Chris Doman, security researcher at AT&T Cybersecurity, explored the sharing of threat intelligence data and
#Infosec19: DNS Security Could Be a Match for Crypto-jacking
DNS security tools can offer IT teams a useful way to detect and prevent illegal cryptocurrency mining on their networks,
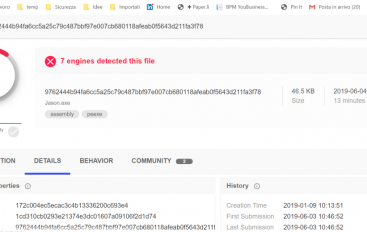
OilRig’s Jason Email Hacking Tool Leaked Online
A few hours ago, a new email hacking tool dubbed Jason and associated with the OilRig APT group was leaked
#Infosec19: Experts Urge Defense-in-Depth Approach to Security Training
IT leaders must expand cybersecurity training programs beyond phishing awareness to avoid major blind spots emerging which could lead to
#Infosec19: Shake Up Cybersecurity Training to Keep Ahead of Hackers
Cybersecurity training needs to evolve to allow organizations to keep up with today’s sophisticated threat actors, according to Max Vetter,
#Infosec19: Physical Intrusions Too Often Go Unchallenged
#Infosec19: Physical Intrusions Too Often Go Unchallenged Security awareness techniques rarely work, as too many employees rarely report or spot
macOS Zero-Day Vulnerability Allows Hackers to Bypass Security Protections With Synthetic Clicks
A new zero-day vulnerability in macOS let hackers to bypass the system security warnings and to compromise easily with Synthetic
Quest Diagnostics Says Nearly 12 Million Patients Records Exposed in Data Breach
Quest Diagnostics has confirmed a data breach that exposes 11.9 million patients records that includes financial data, Social Security numbers,
AI Is Fundamental to Future of SME Cybersecurity
Research shows that small and medium enterprises (SMEs), while confident that artificial intelligence (AI) will be vital to the future
Sophos Acquires Rook Security to Bolster MDR Services
British cybersecurity company Sophos has acquired Rook Security, a provider of managed detection and response (MDR) services. The privately owned
Over Half of UK Firms Failing on Privacy Compliance
UK firms are struggling with a complex patchwork of privacy regulations, with more than half now believing they’re failing with
Expert Shows How to Hack a Supra Smart Cloud TV
Supra Smart Cloud TV allows remote file inclusion in the openLiveURL function, which allows a local attacker to broadcast fake
Confusion Reigns as C-Suite Bemoans Lack of Security Resources
Most C-level executives believe their organization is more exposed to potential security breaches because it lacks crucial technical, financial or
Top 5 ATM Malware Families Used By Hackers to Dispense Money from Targeted ATMs
ATM-Based cyber attacks are continually evolving with much more advanced methods and functions, attackers continuously employee the number of sophisticated
Hackers Abusing Microsoft Azure to Deploy Malware and C2 Servers Using Evasion Technique
Now Microsoft Azure becomes a sweet spot for hackers to host powerful malware and also as a command and control
Leicester City Football Club Disclosed a Card Breach
Leicester City Football Club disclosed a card breach that affected its website, hackers stole payment card data, including card numbers