New ransomware uses disk-level encryption to hold your computer hostage
Encryption can be used to secure your personal communication from prying eyes, keep your banking details secure, and plenty of other great things. However, it’s also the key to an increasingly common form of malware called ransomware. When a computer is hit by a piece of ransomware, the user’s files are encrypted, and only paying a ransom in Bitcoin will get you the key to unlock. There’s a new variant of ransomware floating around, and it takes things to the extreme. Rather than just encrypting files, the Petya malware encrypts your entire hard drive.
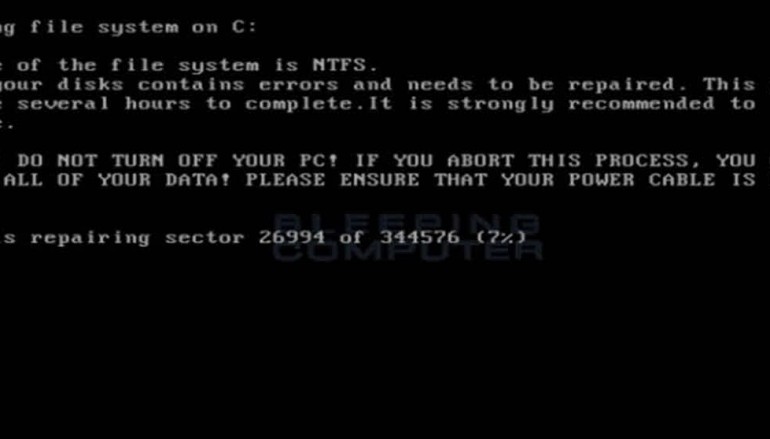
Petya is actually very clever with the way it goes about locking up a computer. After it is installed, the system will spontaneously reboot. Instead of booting normally, the computer loads what appears to be a system CHKDSK. As one would expect, this screen makes it very clear that shutting off the PC in the middle of this operation would be a very bad idea. That’s all just a smokescreen, though. In reality, Petya is using disk-level encryption to lock the system down. The PC’s master boot record has already been compromised at this point, so shutting down won’t do any good.
When the process is complete, the user gets the classic ransomware sales pitch: your files are encrypted — pay up if you ever want to see that data again. In this case, the hard drive itself (including the OS) is inaccessible until the proper decryption key is entered. A number of German businesses have been targeted by Petya already, but the amount requested is surprisingly low at just 0.9 Bitcoins (about $380). The payment must be submitted to a Tor hidden service, which then provides the necessary key.
This approach to ransomware is especially devious in a few ways. With the system disabled, there’s little to no chance for the user to retrieve additional data from the drive. The PC’s original master boot record is also encrypted, so there’s no way to restore it to normal working order without the decryption key. Many pieces of ransomware have to pick and choose what to encrypt, usually going for files in the user’s personal directory. However, it’s possible the important things are elsewhere on the hard drive. That’s not a problem for Petya as it just locks down the whole disk.
The good news is that Petya can’t install itself silently. Because it’s making changes to the boot environment, Windows will pop up a security warning. Users have to click through that in order for Petya to gain control of the system. People will still do that, but at least you have a chance to stop Petya before it’s too late.





