Machete Cyber-Espionage Group Targets Latin America Military
Security experts from ESET uncovered a cyber-espionage group tracked as Machete that stole sensitive files from the Venezuelan military.
Security experts from ESET reported that a cyberespionage group tracked as Machete has stolen sensitive files from the Venezuelan military.
The group has been active since 2010 and hit military organizations and other high-profile targets worldwide. Since the beginning of 2019, the group is focusing on Venezuela, according to the experts, it is still very active at the time of the publication of the report. Experts noticed the group regularly upgrade the malware in its arsenal and its infrastructure.
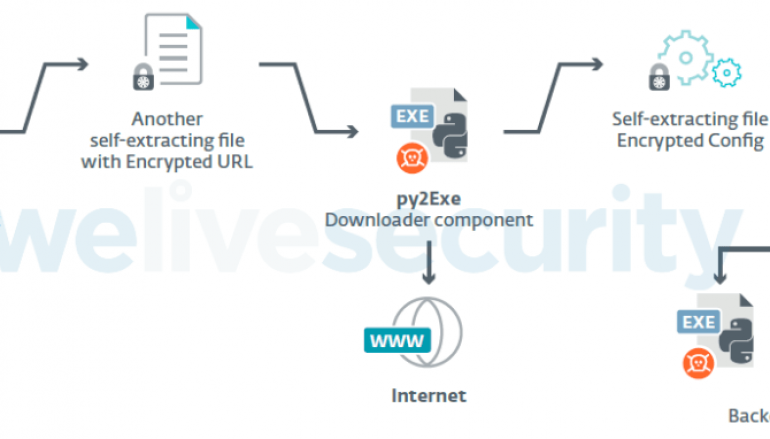
ESET has been tracking a new variant of the Python-based toolset Machete that was detected for the first time in April 2018. Previous variants were analyzed by Kaspersky in 2014 and Cylance in 2017.
The news variant implements a new set of features, between March and May 2019, ESET observed at least 50 infections.
“ESET has been tracking a new version of Machete (the group’s Python-based toolset) that was first seen in April 2018. While the main functionality of the backdoor remains the same as in previous versions, it has been extended with new features over the course of a year.” reads the analysis from ESET.
Most of the infections (75%) were located in Venezuela followed by Colombia (16%), the vast majority of the infected systems belonged to the Venezuelan military.

Machete cyberespionage group hits victims with effective spearphishing techniques, it was focused on Latin American countries and shows a deep knowledge of its targets. The group is also specialized in the exfiltration of file types used by geographic information systems (GIS) software, likely because the threat actors are interested in files that describe navigation routes and positioning using military grids.
“The Machete group sends very specific emails directly to its victims, and these change from target to target. These emails contain either a link to, or an attachment of, a compressed self-extracting archive that runs the malware and opens a document that serves as a decoy.” continues the report. “To trick unsuspecting targets, Machete operators use real documents they have previously stolen;”
The new variant of the malware has many similarities with the samples analyzed by Kaspersky, it implements stealing capabilities, but differences in the way it is delivered and also in the targets. Previous versions of Machete were not so focused on organizations in Latin America.

ESET researchers did not link the Machete group to any specific government, in 2014, Kaspersky experts speculated that the group is composed of Spanish-speaking individuals.
“Various artifacts that we have seen in Machete’s code and the underlying infrastructure lead us to think that this is a Spanish-speaking group.” concludes the report. “The presence of code to exfiltrate data to removable drives when there is physical access to a compromised computer may indicate that Machete operators could have a presence in one of the targeted countries, although we cannot be certain.”
This post Machete Cyber-Espionage Group Targets Latin America Military originally appeared on Security Affairs.





