Iran-Linked APT33 Updates Infrastructure Following Its Public Disclosure
The Iran-linked cyberespionage group APT33 has updated its infrastructure after the publication of a report detailing its activities.
In March, Symantec published a report detailing the activities of Iran-linked cyberespionage group APT33 that was targeting organizations in Saudi Arabia and the United States.
The APT33 group has been around since at least 2013, since mid-2016, the group targeted the aviation industry and energy companies with connections to petrochemical production. Most of the targets were in the Middle East, others were in the U.S., South Korean, and Europe.
Now, according to researchers from Recorded Future, since the publishing of the report, APT33 (aka Elfin) has updated its infrastructure.
Most of the exposed domains no longer resolve to a real IPv4 address, while others moved to new providers. Four domains used in the past were updated the day after publication of the report and resolving to the same IP, which is registered to Swiss-dedicated hosting provider Solar Communications GmBH.
The actions show that threat actors quickly reacted to the publication of the report, but continued to focus on Saudi Arabian organizations.
“In response to the publication of operations in late March 2019, domains associated with suspected APT33 activity were parked or changed to new hosting providers.” reads the report.
“APT33, or a closely aligned threat actor, continues to control C2 domains in bulk.
- Over 1,200 domains have been in use since March 28, 2019 alone.
- 728 of these were identified communicating with infected hosts.
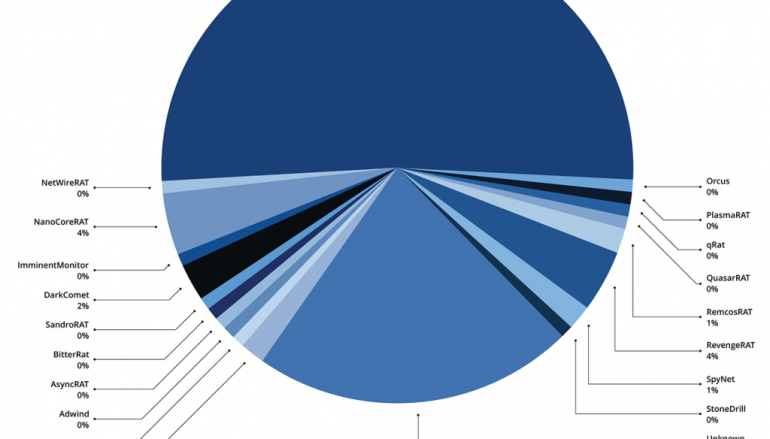
- 575 of the 728 domains were observed communicating with hosts infected by one of 19 mostly publicly available RATs.”
Since March, the operations associated with the APT33 group involved over 1,200 domains, 728 C2 domains were identified communicating with infected hosts, 575 with hosts infected by one of 19 mostly publicly available RATs.
Most of the domains (60%) were associated with malware families related to njRAT infections, a malware wasn’t previously associated with APT33. Other commodity RATs involved in the attacks and associated with the domains are AdwindRAT and RevengeRAT.

The list targeted entities includes:
- A conglomerate headquartered in Saudi Arabia, with businesses in the engineering and construction, utilities, technology, retail, aviation, and finance sectors
- Two Saudi healthcare organizations
- A Saudi company in the metals industry
- An Indian mass media company
- A delegation from a diplomatic institution
The experts at Recorded Future speculate that one APT33 actor, the Nasr Institute, is part of a tiered structure of the Iranian government cyber operations apparatus that also includes APT35 and MUDDYWATER.
“These technical and persona overlaps among Iranian threat actors are not unexpected given the tiered structure of Iranian state management of cyber operations.” concludes the report.
“Within this structure, we assessed that managers are running multiple teams, some of which are associated with government organizations (such as the Nasr Institute), and others that are contracted private companies (such as ITSec Team),” .
This post Iran-Linked APT33 Updates Infrastructure Following Its Public Disclosure originally appeared on Security Affairs.





