Hackers hacking hackers to knacker white hat cracker trackers
The treachery is a bid to prompt Shadowserver and fellow malware investigators to take down their rival’s command and control servers and domains.
Perlotto says they are happy to oblige.
“We are seeing A-level actors hacking through B-level and C-level actors, sometimes through two or three of em,” Perlotto told the Australian Cyber Security Conference in Canberra today.
“The criminals are pointing each other to us saying ‘hey this arsehole’s over here, take him out’ and we do.”
“They will dox each other too and we benefit from that.”
Sometimes these hack-throughs are obvious. Pakistan hackers in one instance owned a Russian hacking group to confuse researchers and draw heat to their competitors. “I looked over it and asked ‘why are these Russians using really good Farsi’?”
The better malware writers are abandoning prefab kits and instead opting for higher quality custom code, the investigator says. This makes their malware stealthier and means their hacking campaigns run longer before being detected and blocked.
The trend may flow down to the shoddier VXers, Pelotto says.
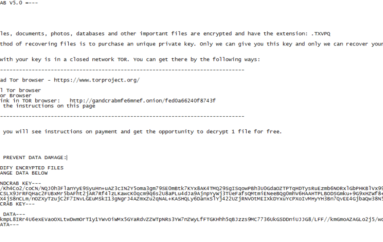
Off-the-shelf and exploit kits are still popular for their effectiveness in pwning unpatched systems with minimal effort, and plays a prominent role in malvertising and spreading ransomware.®
Source | TheRegister