Z-LAB Report – Analyzing the GandCrab v5 ransomware
Experts at the Cybaze Z-Lab have analyzed the latest iteration of the infamous GandCrab ransomware, version 5.0.
Malware researchers at Cybaze ZLab analyzed the latest version of the infamous GandCrab ransomware, version 5.0. Most of the infections have been observed in central Europe, but experts found evidence that the malicious code doesn’t infect Russian users. GandCrab operates like a classic ransomware, it encrypts all user files and drops some ransom notes on the infected machine.
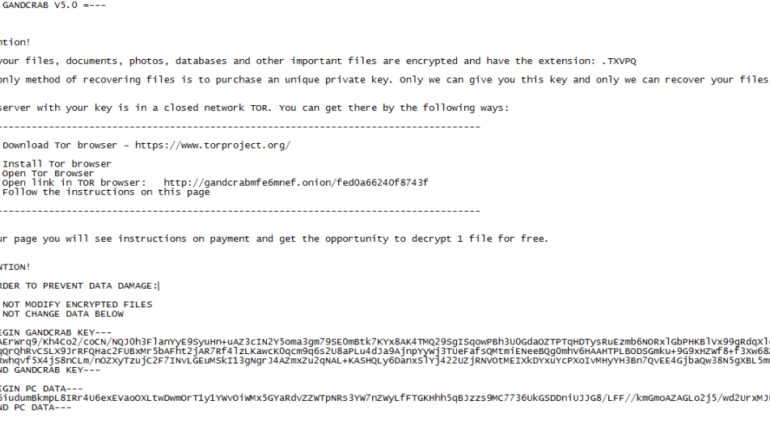
The ransomware uses a pseudo-randomic extension (5 characters long), that is different for each infection (some of these extensions are: .txvpq, .rttmc, .mcbot, etc…).
The ransom note contains some information related to the infection: an ID (“fed0a66240f8743f”, in the image below), a “GANDCRAB KEY”, required to restore the original files, and some encrypted information about the infected system such as the username, the PC name, the domain, the operative system and the language.
Unlike GandCrab v4, this version is able to kill some processes associated with some popular applications (i.e. Word, Excel, SQLServer etc.) to allow the code to encrypt the files opened by these applications.
The payment process is implemented through the hidden service associated with the Tor address:
hxxp://gandcrabmfe6mnef[.]onion, which is the same used by previous versions of the malware.
Technical details, including IoCs and Yara Rules, are reported in the analysis shared by researchers at the ZLab.
You can download the full ZLAB Malware Analysis Report at the following URL:
http://csecybsec.com/download/zlab/20181001_CSE_GandCrabv5.pdf
(Security Affairs – ransomare, cybercrime)
The post Z-LAB Report – Analyzing the GandCrab v5 ransomware appeared first on Security Affairs.