GozNym Trojan spreads to attack German banks
The financial Trojan’s reach continues to expand, placing our banks and accounts at risk.
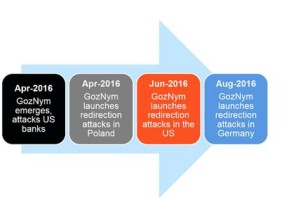
GozNym is continuing its rampage across Europe and has sourced a swathe of fresh banking targets in Germany.
Researchers from IBM X-Force said on Tuesday that the financial malware, a Trojan discovered in April this year, has recently targeted 13 German banks and their local subsidiaries.
It appears the operators behind GozNym have been busy during the summer season, with a sharp hike in attacks across Europe. According to the researchers, in August alone there has been a 3,550 percent spike in activity and a 526 percent rise in comparison to the total number of recorded attacks in April to July this year.
GozNym first hit the spotlight after starting its journey in the United States. In early April, IBM revealed the Trojan — a hybrid comprised of the powerful Nymaim Trojan and Gozi ISFB source code — has been at the heart of the theft of “millions of dollars” from US banks and credit unions.
The hybrid malware included an exploit kit dropper, web-injection capabilities, encryption, anti-VM, and control flow obfuscation, making the malware persistent, difficult to detect, and also powerful.
IBM researchers say that the malware is now also used in redirection schemes which send victims to fraudulent, carbon-copy websites of financial institutions in order to lure them into parting with their online banking details.
“It is evident that the gang operating the malware has the resources and savvy to deploy sophisticated cybercrime tactics against banks,” the researchers say. “The project is very active and evolving rapidly, making it likely to spread to additional countries over time.”
The security team ranks GozNym as the eighth most active financial Trojan in existence, standing up against other malware which has been on the scene far longer, such as Zeus variants, Zberp, and Tinba.
Banks are becoming more aware of cyberattacks and fraud, but on a personal level, you should always make sure you trust an email’s source before you click on a link or open an attachment.
Banks will not ask you to ‘update your security details’ or threaten to ‘close your account’ unless you immediately click through email to their websites, but these are common ways for cybercriminals to lure victims into handing over their credentials.
It only takes a moment to call your bank to check, but it can take months to resolve empty accounts, credit card fraud, and identity theft.
Source | zdnet