Google Warns Journalists and Activists About Recent State-Sponsored Attacks
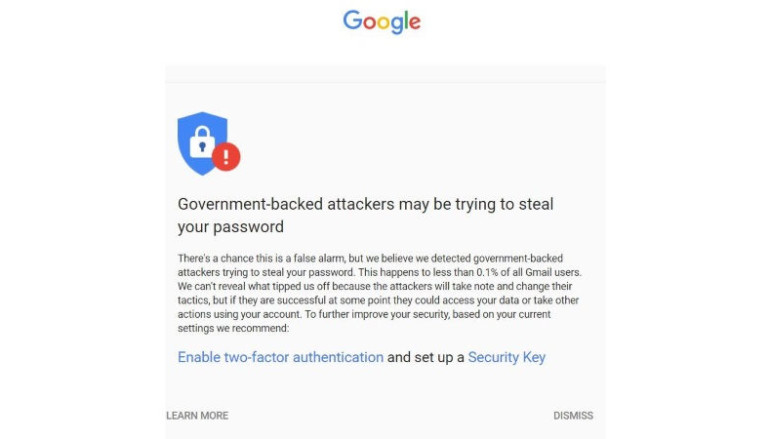
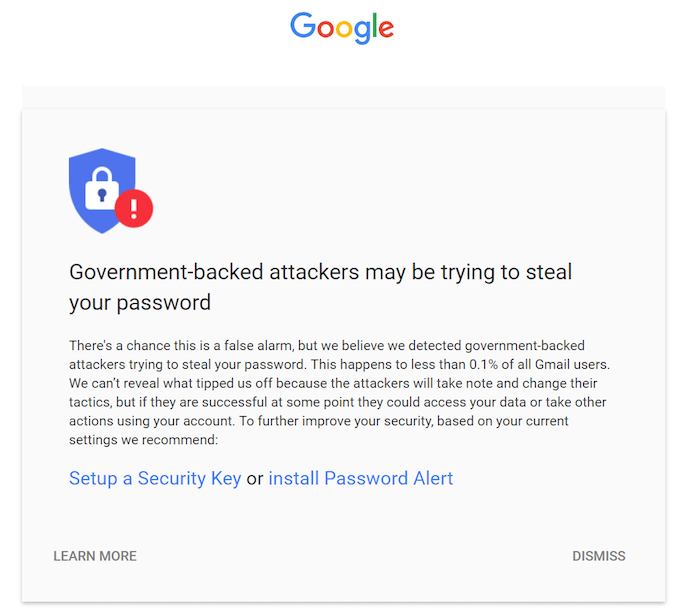
Over the last few days, Google has delivered a batch of warnings about potential government-backed attacks against numerous journalists, academics and activists. Many of the recipients have announced their personal warnings on Twitter. There are some differences in the wording of some of the warnings, but Google has confirmed that the Twitter postings appear to be authentic.
Google has been issuing such warnings since 2012. At first they were simple text alerts across the top of the recipients’ Gmail page. In March of this year it started to use the larger more noticeable banners that are now appearing. The warnings do not indicate that an account has actually been compromised; only that Google researchers have seen indications of an attempt against the account.
The warnings are also not timely. The attack indicators were likely noticed up to a month earlier. Google does not issue immediate warnings for fear that this will allow attackers to determine the method of discovery. This time lapse has led to certain assumptions that the attackers are likely to be the Russian actors, possibly APT28 or APT29, that were linked to attacks against the Democrats, supposedly to influence the election. (Last month, Russian hackers were also linked with targeting journalists investigating the MH17 crash.)
This, however, has to be conjecture. Google does not publicly provide any evidence on the identity of the attackers — and at least one target is a Hong-Kong-based Chinese activist (Joshua Wong Chi-fung).
“Google has been secretive about the algorithms and criteria it uses to determine that a potential attack is state-sponsored,” explains ESET senior research fellow David Harley; adding that such secrecy about proprietary algorithms is not unusual in the security industry. “The relationship with the APT29 targeted malware is speculative, but I can’t say there isn’t a connection. If an attack is based on code that is associated with known state-sponsored attacks, that could be another indicator, if you have that sort of information. Google isn’t exactly known for a spirit of friendly cooperation with the security industry at large, but it certainly has security resources.”
There is, however, an element of hysteria about this current batch of warnings; as if users need to take different precautions against nation attacks than they do against everyday criminal attacks. Activists are more likely to be attacked for political reasons, and in some cases the consequences could be more dire — but the defenses remain the same as those everybody should be using as a matter of course.
“Journalists and professors already know what they should do – and if they don’t, they can easily look it up. If they don’t already follow best practices it’s because they suffer from the fallacy that they aren’t important enough to target,” comments F-Secure’s Sean Sullivan. It is certainly true that users receiving Google warnings should take immediate steps to confirm the integrity of their account: Google doesn’t say the attack was successful, but nor does it say it failed.
Caleb Chen, who works with Private Internet Access, points out that state-sponsored attacks may be more prevalent than is commonly thought. Google says only that it is likely to happen to less than 0.1% of its users. If there are a billion Gmail users, he suggests, those figures mean that up to a million may have seen state-sponsored probing. “As cyber-attacks continue to proliferate, often times across borders, expect reports of this type of probing to rise in the future.”
There is also an irony about warnings being attributed to foreign governments coming at the same time as the US and particularly the UK governments are increasing their own surveillance capabilities. Luis Corrons, technical director at PandaLabs insists there is a difference. “One thing is knowing that governments are harvesting loads of information from everyone, and another thing is an attack targeted at you, so they can compromise your computer and access (steal) all your information, sources, etc.”
Nevertheless, Chen reports a 30% spike in VPN sales from the UK in the week in which the IP Bill completed its course through parliament. While standard computer defenses are required to protect accounts, VPNs are now also required to protect communications — especially those of activists of any persuasion.
Account defenses obviously include strong passwords, 2FA where possible, reputable anti-virus, and an awareness of spear-phishing techniques; but Corrons offers one other piece of advice for journalists and activists: “Ideally have all your sensitive information in a different computer to the one you use for your emails, Internet, etc. Even better if this one is not connected to the Internet.”
Source | securityweek