Experts Found 125 New Flaws in SOHO Routers and NAS Devices from Multiple Vendors
Researchers discovered many flaws in over a dozen small office/home office (SOHO) routers and network-attached storage (NAS) devices.
Security experts have discovered multiple vulnerabilities in over a dozen small office/home office (SOHO) routers and network-attached storage (NAS) devices. The research is part of a project dubbed SOHOpelessly Broken 2.0 conducted Independent Security Evaluators (ISE).
In this phase of the project that started in 2013 (SOHOpelessly Broken 1.0), the researchers assessed the security of 13 SOHO router and NAS devices and found a total of 125 new vulnerabilities.
“Today, we show that security controls put in place by device manufacturers are insufficient against attacks carried out by remote adversaries. This research project aimed to uncover and leverage new techniques to circumvent these new security controls in embedded devices.” reads the report published by the experts.
“Embedded devices are special-purpose computing systems. These types of systems include industrial controllers, small office/home office (SOHO) routers, network-attached storage devices (NAS), and IP cameras. Internet-connected embedded devices are often placed into a broader category referred to as IoT devices. “
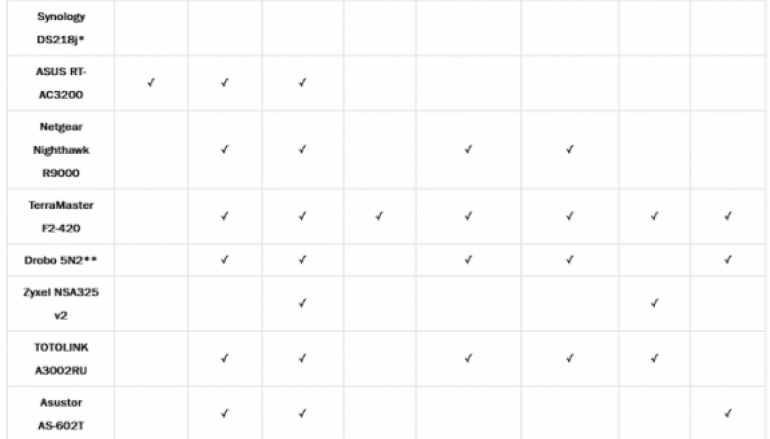
The experts tested SOHO routers and NAS devices from the following vendors:
- Buffalo
- Synology
- TerraMaster
- Zyxel
- Drobo
- ASUS and its subsidiary Asustor
- Seagate
- QNAP
- Lenovo
- Netgear
- Xiaomi
- Zioncom (TOTOLINK)
The experts discovered at least one web application issue in each device they tested vulnerability that could be exploited by a remote attacker to get remote access to the device’s shell or gain access to the device’s administrative panel.
The experts obtained root shells on 12 of the devices that allowed them to take over the vulnerable systems, 6 flaws can be remotely exploited without authentication: the Asustor AS-602T, Buffalo TeraStation TS5600D1206, TerraMaster F2-420, Drobo 5N2, Netgear Nighthawk R9000, and TOTOLINK A3002RU.
The list of flaws discovered by the researchers includes authorization bypass, authentication bypass, buffer overflow, command injection, SQL injection (SQLi), cross-site scripting (XSS), cross-site request forgery (CSRF), and file upload path traversal vulnerabilities.

According to the experts, the level of security for IoT devices is slightly improved since SOHOpelessly Broken 1.0, only a limited number of devices were found implementing defense-in-depth mechanisms such as like address-space layout randomization (ASLR), functionalities that hinder reverse engineering, and integrity verification mechanisms for HTTP requests.
“Perhaps more interesting is the amount of approaches that have not changed since SOHOpelessly Broken 1.0. Features such as anti-CSRF tokens and browser security headers, which are commonplace in mainstream web applications, are still rare among our sample of devices.” concludes the report. “These defense-in-depth mechanisms can greatly enhance the security posture of web applications and the underlying systems they interact with. In many cases, our remote exploits wouldn’t have worked if customary web application security practices had been implemented.”
The researchers responsibly disclosed all of the vulnerabilities they discovered to affected vendors, most of them quickly responded and addressed the issues.
Unfortunately, some manufacturers, including Drobo, Buffalo Americas, and Zioncom Holdings, did not respond to report.
This post Experts Found 125 New Flaws in SOHO Routers and NAS Devices from Multiple Vendors originally appeared on Security Affairs.





