DealPly Adware Abuses Reputation Services to Remain Under the Radar
Malware researchers from enSilo have spotted a new variant of the DealPly adware that uses a new method to avoid detection.
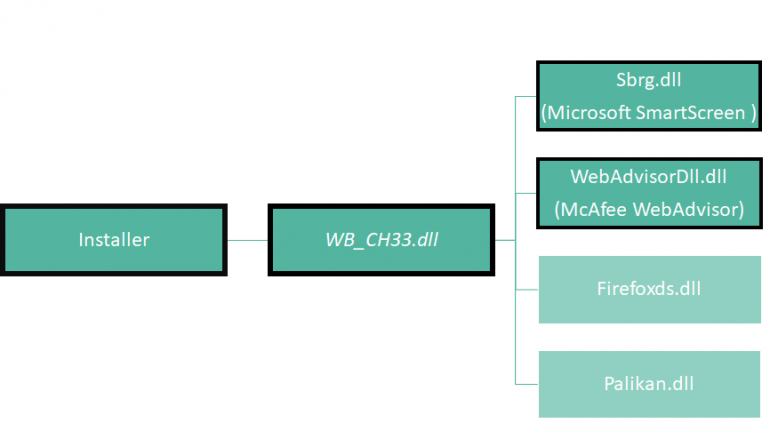
Researchers from enSilo have discovered a new variant of the modular DealPly adware that abuses the reputation services provided by Microsoft’s SmartScreen (aka Windows Defender SmartScreen) and McAfee’s WebAdvisor to avoid detection.
The main feature of the DealPly adware is to install browser extensions that display advertisements in the victim’s browser.
“Besides of modular code, machine fingerprinting, VM detection techniques and robust C&C infrastructure, the most intriguing discovery was the way DealPly abuses Microsoft and McAfee reputation services to remain under the radar. Microsoft SmartScreen and McAfee WebAdvisor provide threat intelligence verdicts on files and URLs and are free to use. ” reads the analysis published by enSilo.

This new variant abuses Microsoft and McAfee reputation services to evade the detection, it likely uses the services to check which of its variants and download sites are tracked as malicious and avoid to use them in future campaigns.
Let’s see indetail how the DealPly adware abuses the reputation services. The experts discovered that Some reputation modules are used only for certain countries. The country codes are organized into two groups and for each group, a different module is executed.
SmartScreen reputation module is used only on hosts located in the countries listed in Group A, while the McAfee WebAdvisor reputation module is used on hosts located in the countries listed in Group B. Anyway, some countries are included in both groups.
To avoid being blacklisted by Microsoft while querying the SmartScreen reputation service, DealPly will use the machines it manages to infect and will use them as a distributed network of machines for harvesting this data.
Upon initial execution, the SmartScreen module implemented by the adware will automatically deliver an empty request to the C2 server that in turn will reply with an XML formatted message containing information such as hashes/urls to be queried using the SmartScreen.
The SmartScreen reputation server appends an Authorization header that is used to prevent unwanted alterations of the requests.
The response sent by the SmartScreen includes a string describing the checked URL. The DealPly adware will focus on the following components and will send them to its C2 :
o UNKN – Unknown URL/File
o MLWR- Malware related URL/File
o PHSH – Phishing related URL/File
Experts highlighted the fact that the SmartScreen API is undocumented, this means that the author of the malware has spent a significant effort in reverse engineering the inner workings of the SmartScreen mechanismfeature.
Experts noticed that the DealPly adware supports multiple versions of the SmartScreen API to query the service on several Windows versions.
As anticipated, the adware also abuses McAfee’s WebAdvisor reputation service.
DealPly will send a request to the WebAdvisor service via the https://webadvisorc.rest.gti.mcafee.com/1 URL and will get data from the response.
enSilo researchers believe that this evasion technique will most probably be adopted by other malware in the future.
“In this blog we present an innovative technique adopted by DealPly operators to automate the evasion from AV products.By constantly querying reputation services they are able to automatically assess their AV detection rate and generate new samples when needed. This technique enable DealPly to always stay ahead of security solutions.” conclude the experts.
“This technique was initially observed when analyzing DealPly adware, yet we believe that it is only a matter of time before advanced malware operations will follow the trend.”
This post DealPly Adware Abuses Reputation Services to Remain Under the Radar originally appeared on Security Affairs.





