Latest News
New EU Protocol Preps for X Border Cyber-Attacks
Before the next WannaCry or NotPetya cyber-attack strikes, potentially resulting in widespread damage for which few are actually prepared, law
What is DNS Attack and How Does it Work?
DNS Attack is a type of cyber attack that exploit the weakness or vulnerability in Domain name system. Today, the
Massive Attacks Bypass MFA on Office 365 and G Suite accounts via IMAP Protocol
Threat actors targeted Office 365 and G Suite cloud accounts using the IMAP protocol to bypass multi-factor authentication (MFA). Over
Zero-Day Flaws in Counter-Strike 1.6 Exploited by Malicious Servers to Hack Players Computer
Hackers exploiting zero-day vulnerabilities in Counter-Strike 1.6 game client to infect player’s devices by using a malicious gaming server and
Hackers Using Steganography to Drop the Powload Malware & Hide Their Malvertising Traffic
Cyber criminals now approaching a unique way to spread Powload malware with the help of steganography to infect the targeted
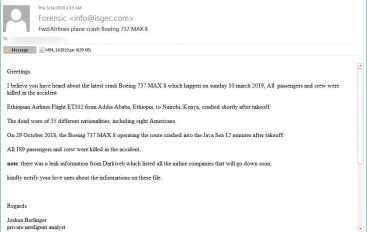
Experts Uncovered a Malspam Campaign using Boeing 737 Max Crashes
Experts at the 360 Threat Intelligence Center uncovered a new malspam campaign that leverages the tragic Boeing 737 Max crash
Gnosticplayers Offers 26 Million New Accounts for Sale on the Dark Web
The hacker gnosticplayers is offering the fourth batch of millions of records stolen from 6 new websites for sale on
Is this website Safe : How to Check Website Safety to Avoid Cyber Threats Online
Is this website safe ? In this digital world, Check website safety is most important concern since there are countless
138 Android Anti Virus Apps are Frauds in Play Store – Only 23 Apps Performed 100% Malware Detection
Recent In-depth analysis against Android Antivirus in Google play store reveals that, 138 Android antivirus products are completely fake and
Secur Solutions Group Data Leak Exposes 800,000 Singapore Blood Donors
Secur Solutions Group data leak – Another clamorous data leak made the headlines, personal information of 808,201 blood donors in
250,000 Sensitive Legal Documents Leaked Online via Unprotected Elasticsearch Cluster
Security researchers discovered 257,287 legal documents from unprotected Elasticsearch cluster that hosted on a US-based Amazon AWS server. The unprotected
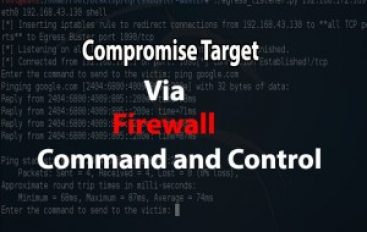
EgressBuster – A Pentesting Tool to Compromise Victim via Command & Control using Firewall
Network Firewalls acts as a fortification to keep the internal corporate network secure. Many people often think as it is
Top 10 Best Proxy Server 2019 & Important Methods to Prevent Yourself From Hackers
Best Proxy Server has been used in enormous cases where some personal data or information have been misused illegally against
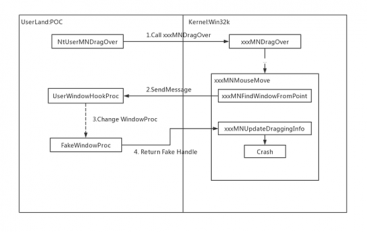
Experts Published Details of the Actively Exploited CVE-2019-0808 Windows Flaw
Experts from Qihoo 360 disclosed technical details of the actively exploited Windows zero-day flaw CVE-2019-0808 recently patched by Microsoft. Researchers
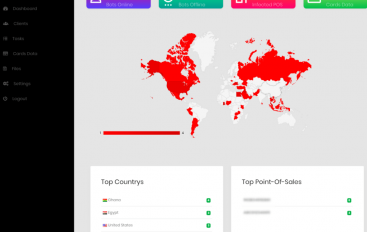
GlitchPOS PoS Malware Appears in the Cybercrime Underground
A new piece of PoS malware appeared in the threat landscape, the malicious code dubbed GlitchPOS has been found on
DMSniff POS Malware Uses DGA to Stay Active
Researchers have discovered a rare strain of POS malware which uses a domain generation algorithm (DGA) to maintain persistence. Flashpoint‘s