Posts From CCME
Experts found tens of thousands of printers that are exposed online that are leaking device names, organization names, WiFi SSIDs, and other info. It’s not a mystery, a printer left exposed online without proper security could open the doors to
US government websites are taking another major step forward to becoming more secure after it was announced that all .gov TLDs would be changed to enforce HSTS preloading. The DotGov program made the announcement on Sunday, stating that all new
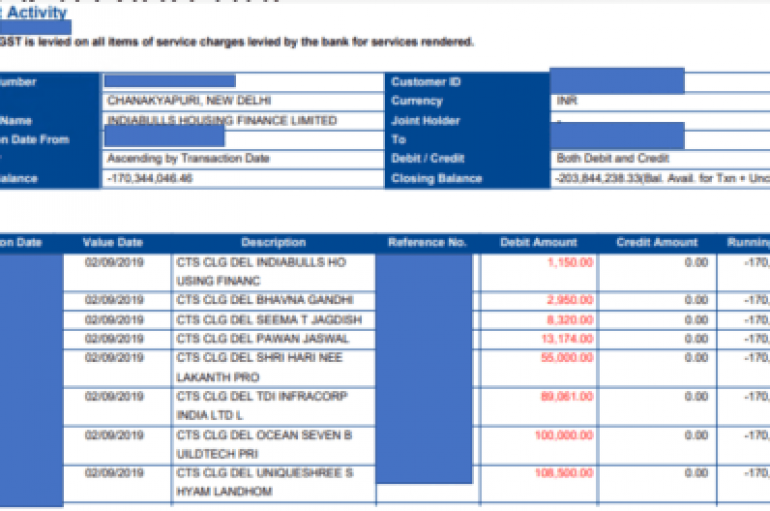
CLOP ransomware operators have allegedly hacked IndiaBulls Group, an Indian conglomerate headquartered in Gurgaon, India. CLOP ransomware operators have allegedly hacked the Indian conglomerate IndiaBulls Group, its primary businesses are housing finance, consumer finance, and wealth management. Indiabulls Group has around 19,000
Over two-fifths of businesses are considering replacing email as their primary communications channel as the country begins to open-up again after lockdown, according to a new report. Think tank Parliament Street commissioned the poll of 200 senior decision makers in
The Age Verification law is set to be revived for the UK Government’s online harms bill. Speaking at the Westminster eForum policy conference around next steps for online regulation in the UK, Sarah Connolly, director, security and online harms at
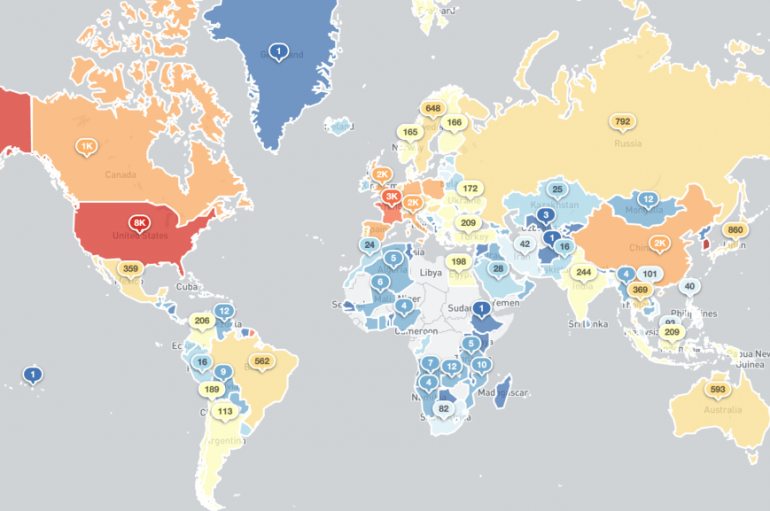
A major supply chain breach appears to have led to the exposure of hundreds of thousands of sensitive US police records dating back over two decades. WikiLeaks-like organization Distributed Denial of Secrets released the trove on Friday, claiming it contained
How to Detect Obfuscated Malware on Your Server
Traditional malware detecting methods are ineffective against the hackers’ new techniques – deploying malware which is obfuscated. That’s why an innovative new approach is required in server security to stop these new threats. History of Malware Detecting Technologies The constant
Indonesia Denies #COVID19 Test Data Breach
An alleged breach of COVID-19 test result data is being investigated by authorities in Indonesia. Concerns over a possible breach were raised after a hacker tried to sell what they claimed was the personal information of hundreds of thousands of
Nearly GBP17m has been lost to online fraud over the COVID-19 lockdown period with younger shoppers most affected, according to Action Fraud. The UK’s National Fraud and Cybercrime Reporting Center claimed that online scams had snared 16,352 victims with online
Security researchers are warning of a multi-country North Korean phishing campaign designed to capitalize on government COVID-19 bail-out measures. The operation is being undertaken by Pyongyang’s notorious Lazarus Group, and is “designed to impersonate government agencies, departments, and trade associations
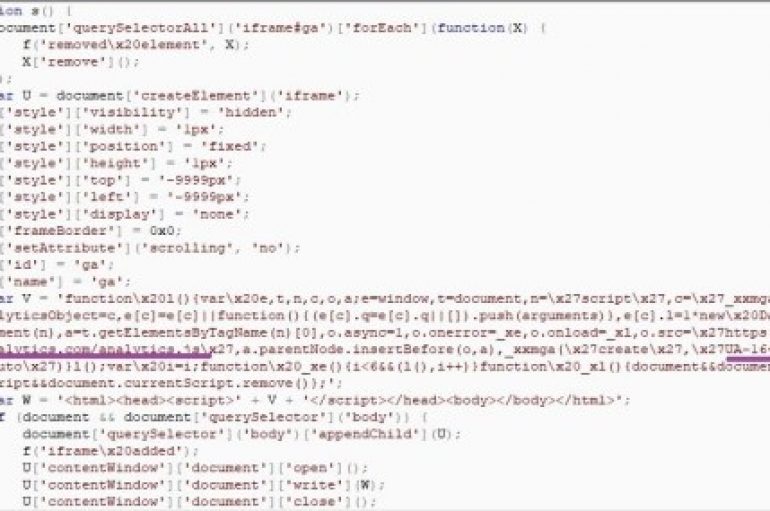
Security researchers at Kaspersky uncovered a web skimming campaign leveraging Google Analytics service to steal user data. Recently, researchers at Kaspersky identified several web skimming attacks that abused Google Analytics service to exfiltrate data stolen with an e-skimmer software. Threat
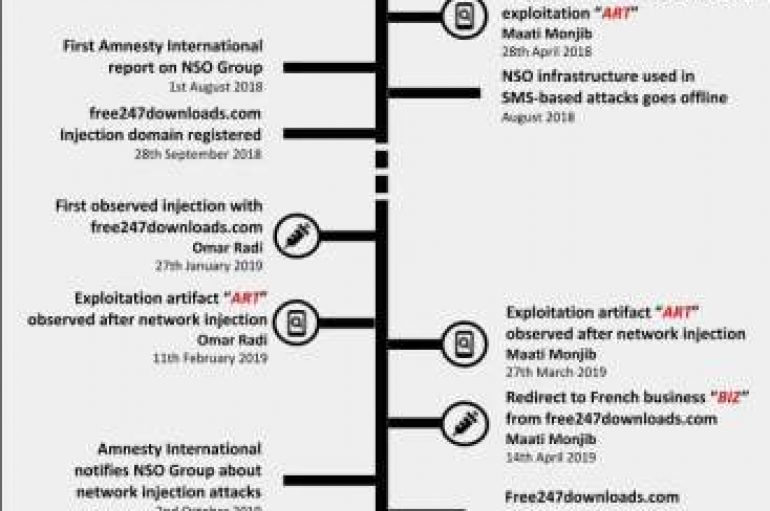
Researchers at Amnesty International collected evidence that a Moroccan journalist was targeted with network injection attacks using NSO Group ‘s spyware. In October 2019, security experts at Amnesty International’s Security Lab have uncovered targeted attacks against Moroccan human rights defenders
Security researchers are warning players of a popular MMO game that over 1.3 million user records are being sold on dark web forums. Usernames, passwords, email addresses, phone numbers and IP addresses belonging to players of Stalker Online were found
Experts spotted a new version of the IcedID banking trojan that uses steganography to infect victims as part of COVID-19 themed attacks. A new version of the IcedID banking trojan was employed in COVID-19 themed attacks, the new variant uses
Burp Suite 2020.5.1 Released – Security Bugs Fixed & Improvements to the HTTP Message Editor
Burp Suite is one of the most famous tools used by pentesters & bug hunters, which incorporates a full static code investigation engine to discover vulnerabilities. It is a widely used tool to identify vulnerabilities with web applications. Penetration testers
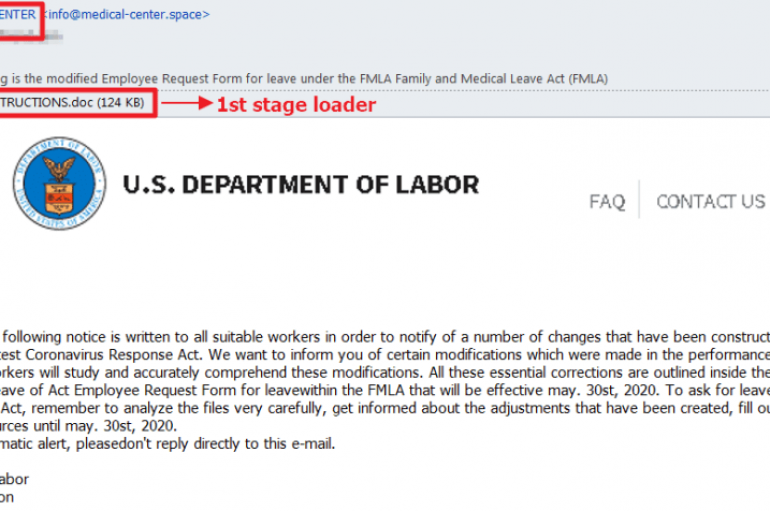
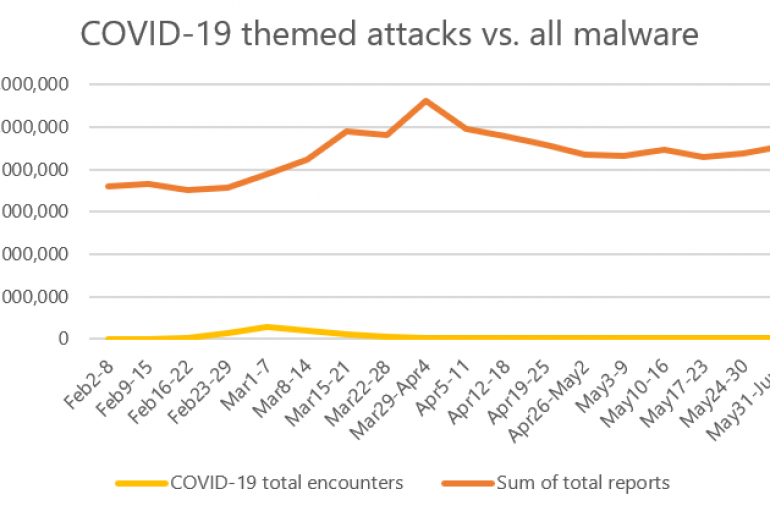
Threat actors adapted their tactics to exploit the interest in the ongoing COVID-19 pandemic, Microsoft says. Since the beginning of the COVID-19 pandemic, threat actors started to actively deploy opportunistic campaigns using Coronavirus lures. Anyway, Microsoft says that malware attacks