Posts From CCME
Thousands of domestic violence victims have had their emergency distress messages exposed after a developer misconfigured a back-end AWS bucket. Researchers at vpnMentor led by Noam Rotem and Ran Locar found the voice recordings stored on a publicly accessible AWS
European Commission: Still Work to Do on GDPR
The GDPR has successfully met its main objectives but work still needs to be done to improve cross-border investigations, increase regulator resources and address fragmented approaches across the EU, according to the European Commission. The review of the data protection
Microsoft has warned Exchange customers to patch their servers urgently after reporting a surge in attacks exploiting an Internet Information Service (IIS) vulnerability. That flaw, CVE-2020-0688, was patched in February, but attackers are still finding victims compromised by such attacks.
A newly detected threat group has stolen an estimated minimum of $200m from cryptocurrency exchanges in just two years. The dastardly deeds of cyber-criminal organization CryptoCore were discovered by security firm ClearSky Cyber Security. Recently published research by the company
US lawmakers have introduced a bill that proposes banning federal law enforcement agencies from using facial recognition and biometric surveillance technology. The Facial Recognition and Biometric Technology Moratorium Act of 2020 was introduced yesterday by Senators Ed Markey and Jeff
Around half (48%) of UK businesses have admitted that their cybersecurity policies aren’t fit-for-purpose in the “new normal” of mass remote working, according to Centrify research. The access management vendor polled 200 senior decision makers in medium and large businesses
Zoom Hires Former Salesforce SVP as New CISO
Zoom has made another high-profile hire as it looks to bolster its security credentials, with the recruitment of Salesforce SVP Jason Lee as its new CISO. Lee was previously SVP of security operations at the SaaS pioneer, where he was
Maze ransomware operators claims to have breached the South Korean multinational electronics company LG Electronics. Researchers at Cyble discovered a data leak of LG Electronics published by Maze ransomware operators. “As part of our regular darkweb monitoring, our researchers came across the
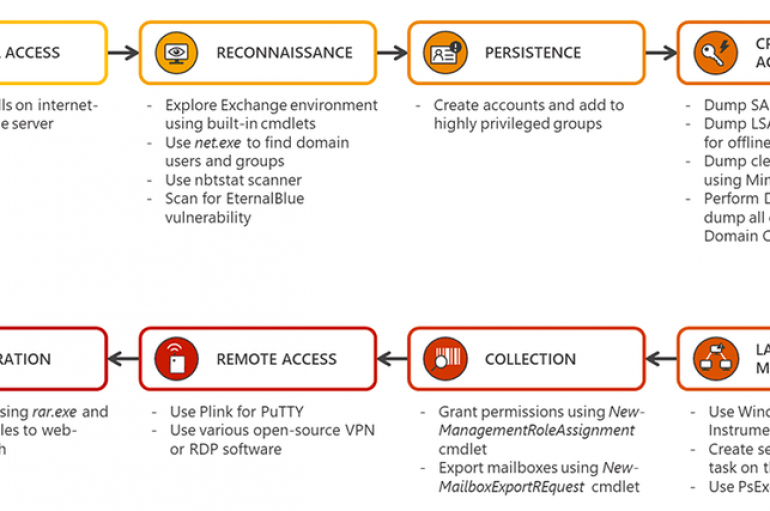
Microsoft researchers are warning of attacks against Exchange servers and published guidance on how to defend them. Microsoft’s Defender ATP Research Team released guidance on how to defend against attacks targeting Exchange servers with the use of behavior-based detection. Microsoft
Details of a new COVID-themed ransomware attack on Android users in Canada, known as CryCryptor, have been revealed by ESET researchers. In the attack, people were lured into downloading a ransomware app disguised as an official COVID-19 tracing tool through
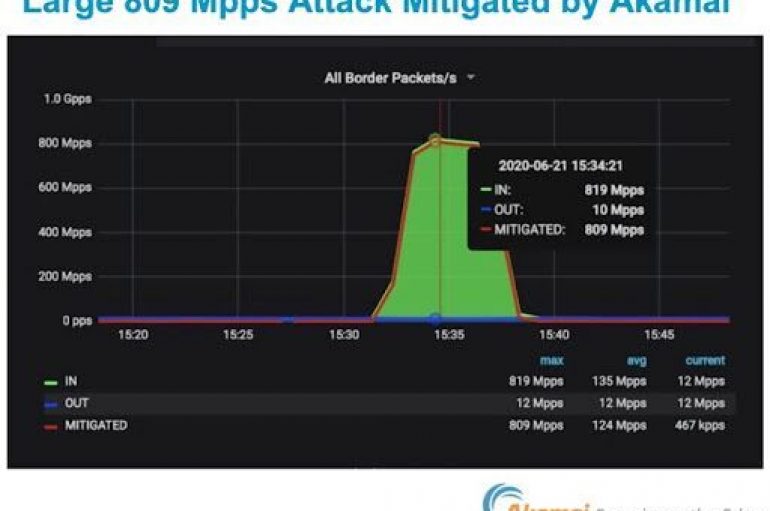
Akamai announced to have mitigated a record distributed denial-of-service (DDoS) attack that hit a European bank. Akamai revealed that a bank in Europe was hit by a massive distributed denial-of-service (DDoS) attack that peaked a record 809 million packets per
Personal data of an estimated 100,000 social media influencers has been accessed and partially leaked following a breach at social media marketing firm Preen.Me, Risk Based Security has discovered. The same breach has also led to more than 250,000 social
PlayStation Announces Bug Bounty Program
PlayStation has announced that it will pay hackers thousands of dollars to unearth vulnerabilities in its network and entertainment products. The gaming titan launched its PlayStation Bug Bounty program yesterday morning in hopes of rooting out flaws and providing players
The National Cyber Security Centre (NCSC) has announced that in just two months of its Suspicious Email Reporting Service being launched, it has received one million reports. According to a statement, the service, which was launched in April as part
Financial fraud attempts rose by 33% in April as the UK entered lockdown due to the COVID-19 pandemic, new analysis from Experian and the National Hunter Fraud Prevention Service has revealed. Fraudsters targeted a myriad of financial products, including current
Medical Devices Among Most Risky to Security
Medical devices, physical access operations and networking equipment are among the most risky when it comes to risks posed to businesses. Using analysis of metrics and data from the Forescout Device Cloud, the company identified points of risk inherent to