Posts From CCME
Spyse is a cybersecurity search engine that has caught the attention of many pentesters due to its unique data-gathering design. Most services offer scanning tools, and Spyse places itself on a different tier by combining those tools into a search
NSA Issues VPN Security Guidance
The National Security Agency released guidance this week on securing IPsec virtual private networks as companies across the US continue to grapple with remote working in the wake of the coronavirus pandemic. The advice included a warning not to rely
Alleged Cyber Attacks Caused Fire and Explosions at Nuclear and Military Facilities in Iran
The root cause of a series of explosions at important facilities in Iran may be cyberattacks allegedly launched by Israel. A recent sequence of fires and explosions at important Iranian facilities may have been caused by cyber attacks as part
Avaddon Ransomware Still Using Excel 4.0 Macros
Just like jokes, sometimes the old vulnerabilities are the best ones. So, stop us if you’ve heard this before: ransomware criminals are still using malicious Excel 4.0 macros in campaigns. This week, Microsoft’s security intelligence team noted that Avaddon was
Moose Remain Unaware of Lottery Privacy Breach
It isn’t often that you hear the words “breach,” “privacy,” and “moose” in the same sentence, but thanks to the province of Nova Scotia, that just changed. The maritime province on Canada’s East Coast was dealing with the publicity fallout
A record number of teenagers have enrolled in the National Cyber Security Center’s (NCSC) CyberFirst summer courses this year, with classes held online for the first time due to the COVID-19 pandemic. As a result, the NCSC plans to offer
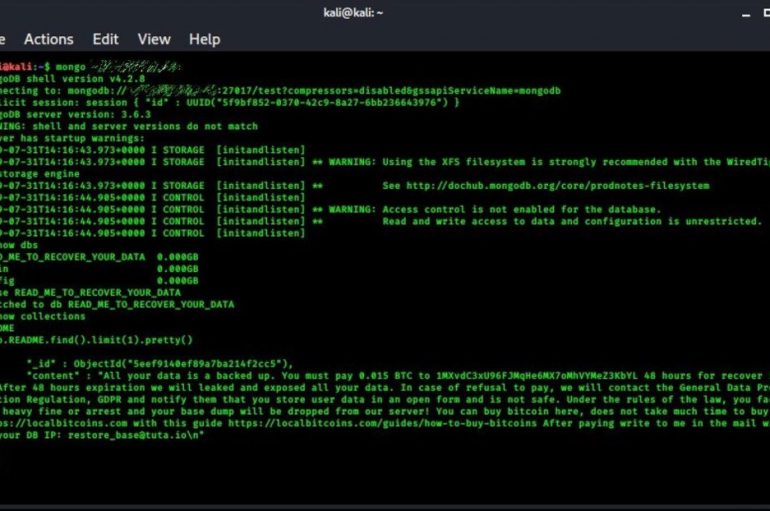
Hackers are Targeting Unsecured MongoDB Database
A new wave of attacks is targeting unsecured MongoDB database servers and wiping their content attempting to extort a ransom to the victims. The popular security expert Victor Gevers from the non-profit GDI Foundation reported a new wave of attacks
Nearly 100,000 customers have had their sensitive personal data and revealing photos exposed online after a US-based fitness company misconfigured an Amazon database. Las Vegas-headquartered V Shred left the S3 bucket containing over 1.3 million individual files publicly accessible, according
GoldenSpy Uninstaller Appears Out of Nowhere
A mysterious uninstaller has been discovered in malware-laden tax software required for download by firms doing business in China, according to Trustwave. The security vendor explained last week how it discovered a backdoor it named GoldenSpy inside Intelligent Tax software,
Third-party apps on social media continue to misuse the data shared by users, researchers from the University of Iowa proposed a paper dubbed CanaryTrap details Data Misuse by Third-Party Apps on Online Social Networks. CanaryTrap aimed to misuse of data
Security researchers have discovered five dating apps in the US and East Asia which are leaking millions of customer records thanks to misconfigured cloud databases. A team from WizCase led by Avishai Efrat explained that the Elasticsearch servers, MongoDB databases
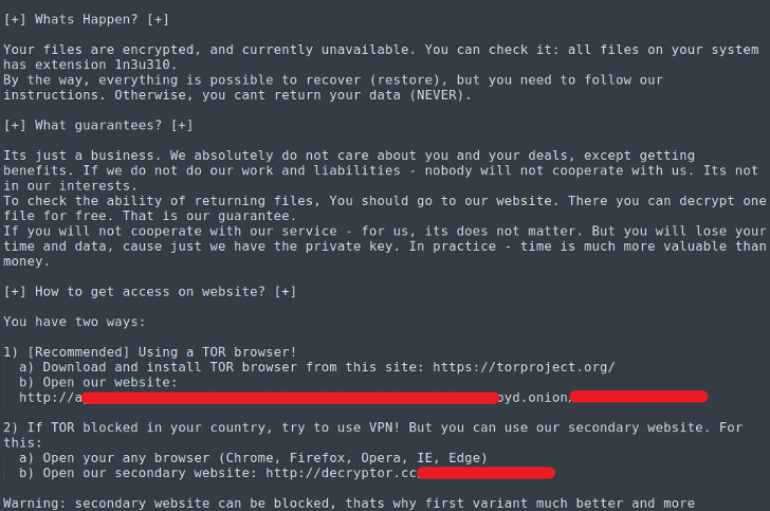
Sodinokibi ransomware (aka REvil) operators are demanding a $14 million ransom from Brazilian-based electrical energy company Light S.A. Sodinokibi ransomware (aka REvil) operators have breached the Brazilian-based electrical energy company Light S.A. and are demanding a $14 million ransom. The
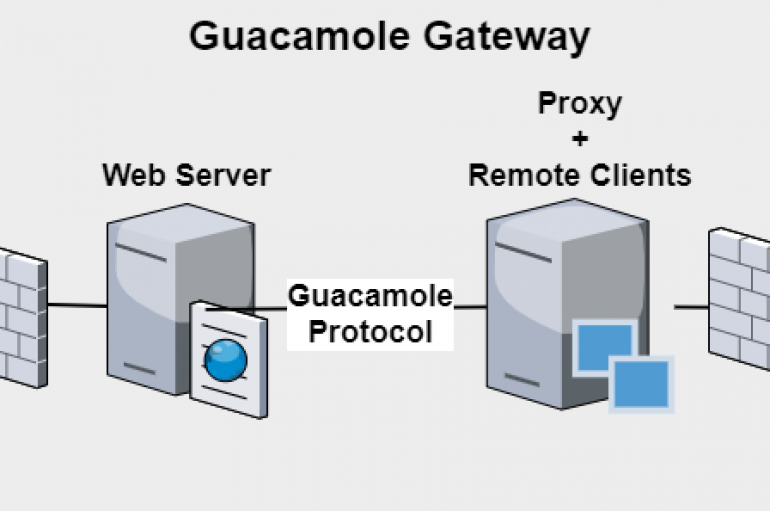
Researchers have discovered a gaping hole in popular remote access system Apache Guacamole that puts thousands of companies with remote employees at risk. The flaw could allow attackers to control the software and the computers that connect to it. Luckily,
Schools and colleges in the US have leaked 24.5 million records since 2005, according to new research by technology website Comparitech. K-12 school districts across the country have suffered 1,327 breaches in the last 15 years–with last year’s count setting
Security researchers discovered multiple critical reverse RDP vulnerabilities in the remote desktop application Apache Guacamole. Security experts from Check Point Research have discovered multiple critical reverse RDP vulnerabilities in the Apache Guacamole, which is a clientless remote desktop gateway. It supports standard protocols like VNC, RDP, and
Almost everyone at home now has a Wi-Fi router. People would probably ask you forthe network’s password to check their smartphone or show you vacation pictures stored in the cloud. Many will learn your wireless password soon so people will