Posts From CCME
Updating routers with the latest firmware is a frequent recommendation to improve network security. When it comes to home routers, though, the latest updates won’t help you much. According to a study by Germany’s Fraunhofer Institute for Communication (FKIE), vendors
Security company Proofpoint has identified two new exploits coded into Purple Fox, an exploit kit that has evolved dramatically in the last year. The updates show that cyber-criminals are continuing to invest in infection tools to help get their malware
System partition infections as a method of installing adware are on the rise in mobile devices, according to new research from Kaspersky. It found that 14.8% of Kaspersky users who were targeted by malware or adware in 2019 had this
The number and value of fines for data breaches is predicted to increase between now and 2025, according to a new study by DSA Connect. Interviews with 1000 workers between 24 and 27 April 2020 revealed that 37% think there
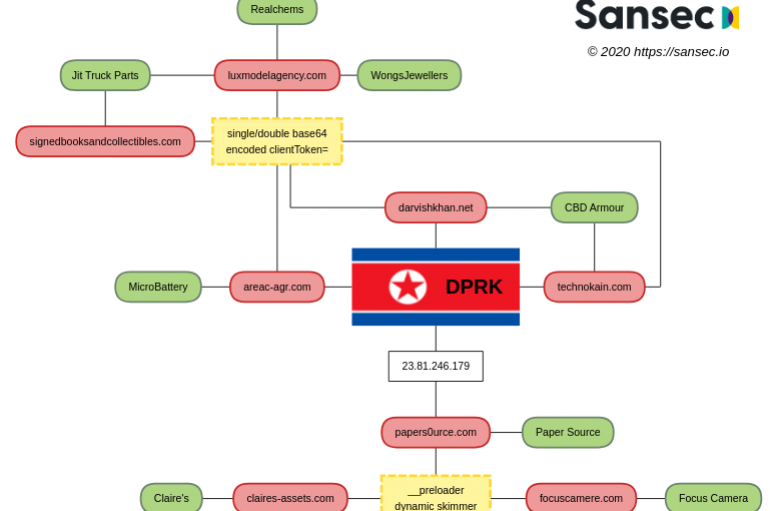
North Korea-linked Lazarus APT has been stealing payment card data from customers of large retailers in the U.S. and Europe for at least a year. Sansec researchers reported that North Korea-linked Lazarus APT group has been stealing payment card information
Tesco Clubcard users have been warned to check their accounts, after a weakness was discovered in the way that Hotels.com codes were generated, which then impacted Clubcard members as they tried to use their points. Whilst Tesco Clubcard’s IT systems
A new report indicates that the web skimming attacks on popular US and European online stores linked with North Korean state-sponsored hackers. Sansec research shows that APT Lazarus/HIDDEN COBRA hacking group break into the websites of large US retailers and
The number of UK business falling victim to cybercrime has doubled over the past five years, costing the economy an estimated tens of billions in the process, according to new research from Beaming. The business ISP polled over 2500 companies
North Korean Hackers Behind Magecart Attacks
North Korean hackers appear to have been breaking into US e-commerce stores since May 2019 and planting digital skimming code to make money for the hermit nation. Researchers at Sansec claimed today that the notorious Lazarus (Hidden Cobra) group was
A Google VP has ignited a fierce debate in the cybersecurity industry over the use of potentially discriminatory language after withdrawing from the upcoming Black Hat USA virtual event in protest. David Kleidermacher, who is VP of Android security and
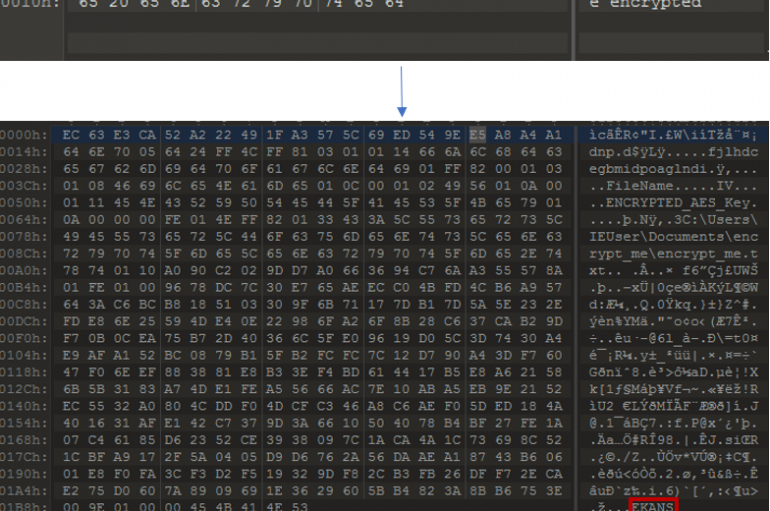
Experts spotted recent samples of the Snake ransomware that were isolating the infected systems while encrypting files to avoid interference. Experts from cybersecurity firm Deep Instinct recently spotted some sample of the Snake ransomware (also known as EKANS) were observed isolating the infected systems to
Behave – A New Browser Extension to Find Web Sites that Perform Browser-Based Port Scans or Attack
A new browser extension published dubbed Behave! that warns the user if the website tries to perform a port scan or launch DNS based attacks. The web sites port scanning issue came into light after a script found on the
A Vulnerability Scanning Tools is one of the essential tools in IT departments Since vulnerabilities pop up every day and thus leaving a loophole for the organization. The Vulnerability scanning tools helps in detecting security loopholes with the application, operating
Critical security vulnerabilities discovered with the F5 BIG-IP application delivery controller (ADC) let remote attackers to run commands and to compromise the system. The BIG-IP application delivery controller (ADC) use to handle application traffic and secure your infrastructure. Based on
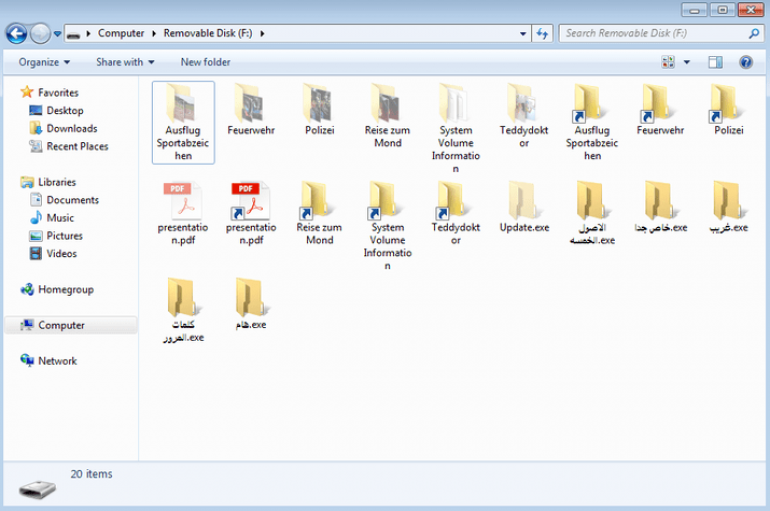
A new piece of ransomware dubbed Try2Cry leverages infected USB flash drives and Windows shortcuts (LNK files) to infect other Windows systems. A new ransomware dubbed Try2Cry implements wormable capabilities to infect other Windows systems by using USB flash drives or Windows shortcuts (LNK files).
LinkedIn caught snooping on the clipboard data of every keystroke, the issue was discovered with the beta version of iOS 14. The LinkedIn iOS app is responsible for the privacy-intrusive behavior that spotted by a developer who goes with the