Posts From CCME
A test carried out by ethical hackers against the cyber defenses of 50 universities found that they can cripple the defense and exfiltrate sensitive data within two hours. The penetration testing conducted ethical hackers” working for Jisc, who provides internet
New DNS Hijacking Attack Exploiting DLink Routers to Target Netflix, PayPal, Uber, Gmail Users
Cybercriminals continuously perform DNS hijacking attack to the consumer’s routers over the past 3 months, and the sites targeted for phishing includes Netflix, PayPal, Uber, Gmail. DNS hijacking is a type of malicious attack that used to redirect the users
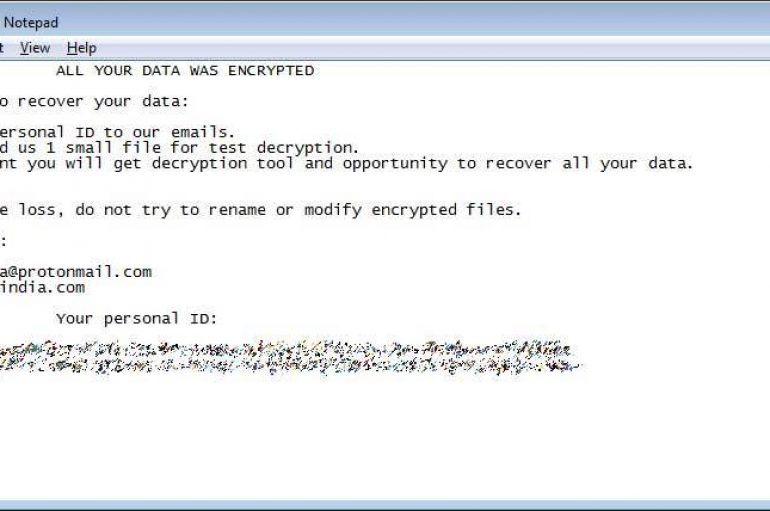
Researchers at Emsisoft developed a decryptor for the Planetary Ransomware family that could allow victims to decrypt their files for free. Good news for the victims of the Planetary Ransomware, security firm Emsisoft has released a decryptor that allows victims
As a normal Internet user, you have the sensible hope that your correspondences and transaction are private and secure in Internet security Environment. Numerous activities in our everyday lives now depend on the Internet, including different types of communication, shopping,
With the use of deep learning, researchers Yisroel Mirsky, Tom Mahler, Ilan Shelef and Yuval Elovici at Cyber Security Labs at Ben-Gurion University demonstrated in a video proof of concept (PoC) that an attacker could fool three expert radiologists by
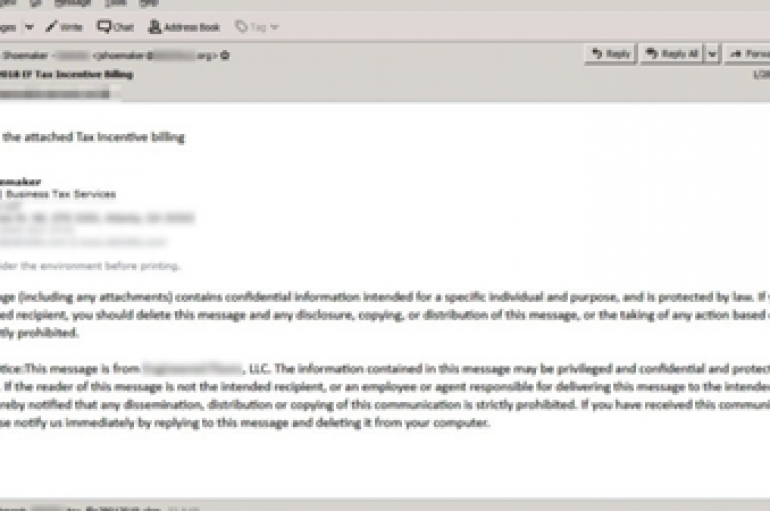
TrickBot Used in Tax Season Email Spoofing
As April 15, the US tax-filing deadline, swiftly approaches, cyber-criminals are taking advantage of the season, using campaigns to deceive three of the biggest accounting, tax services and payroll companies in the US, according to researchers at IBM X-Force. In
A Serious vulnerability that discovered in MikroTik RouterOS allows attackers to perform DoS attack on the vulnerable router that causes the device to reboot. MikroTik provides hardware and software for Internet connectivity around the world and they also created a
FIN6 Hackers Group Targeting Enterprise Network to Deploy LockerGoga and Ryuk Ransomware
FIN6 cybercrime group tied with a LockerGoga and Ryuk ransomware that targets the enterprise network in an engineering industry by compromising the internet facing system. Researchers from FireEye recently learning this incident from their customer’s network and the further investigation
Unofficial security patches have been released for two Oracle Java Runtime Environment (RE) flaws yet to be fixed discovered by Google Project Zero researcher. Unofficial security patches have been released for two Oracle Java Runtime Environment (RE) vulnerabilities discovered by
UK Orgs, Charities Improving in Cybersecurity
Businesses and charities are showing progress in defending against breaches and ensuring General Data Protection Regulation Compliance (GDPR), according to a new report published by the Department for Digital, Culture, Media and Sport. The Cyber Security Breaches Survey 2019 found
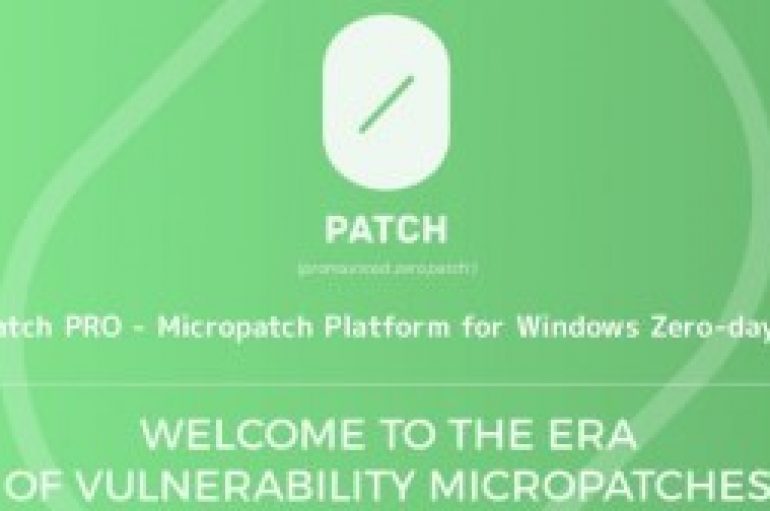
0patch PRO – New Micropatch Program Launched for Windows Platform Zero-day Vulnerabilities
ACROS Security announced new Commercial 0patch PRO, a new platform that offers a security Micropatches for Windows platform Zero-day vulnerabilities. 0patch PRO is the first commercial platform in the security industries that offers rapid fixes for the zero-day flaws in
Cynet Offers a Free Threat Assessment for Mid-Sized and Large Organizations – Take a Free Ride Now
Visibility into an environment attack surface is the fundamental cornerstone to sound security decision making. However, the standard process of 3rd party threat assessment as practiced today is both time consuming and expensive. Cynet changes the rules of the game
A distributed denial-of-service (DDoS) attack aims to exhaust the resources of a network, application or service so that genuine users cannot gain access. There are different types of DDoS attacks, but in general, a DDoS assault is launched simultaneously from
Indane LPG exposed nearly 7 Million Customers and distributors sensitive data online due to the serious vulnerabilities that discovered in all the major services that provide by their iOS applications. Indane is owned by Indian Oil Corporation Limited, which is
74 Facebook Groups With 385,000 Members Serves as Black Markets for Hackers to Carry out Illegal Activities
Cybercriminal host dozens of Facebook groups to serve as a marketplace for carrying out a number of illicit services and for exchanges. Instead of using hidden services cybercriminals prefer to operate in the massive social media platform. Talos research uncovered
Well-Known and advanced threat actors groups TA505 APT distributing a new variant of ServHelper malware that distributed via weaponized Excel 4.0 macro to open a backdoor & steal sensitive information from infection system. TA505 threat actors associated with various high