Posts From CCME
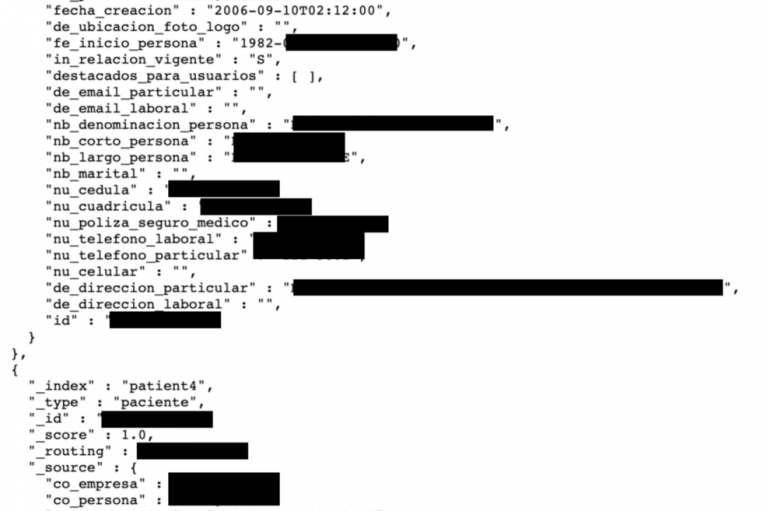
Personally identifiable information belonging to roughly 90% of Panama citizens were exposed on a poorly configured Elasticsearch server. Security researcher Bob Diachenko discovered an unprotected Elasticsearch server exposing personally identifiable information belonging to nearly 90% of Panama citizens. Exposed data
A critical remote code execution vulnerability in WhatsApp allows hackers to deploy spyware remotely on the vulnerable devices. The vulnerability was discovered earlier this month by WhatsApp, and it can be tracked as CVE-2019-3568. The vulnerability resides in “WhatsApp VOIP
Twitter Bug Exposed location Data of Some Users to Unknown Advertisers. Twitter disclosed a bug report that in certain conditions they have accidentally collected and shared the location data of iOS users to the advertisers, even if they opted not
Microsoft Published a List of Legitimate Apps that Attackers Abuse to Bypass Windows Defender
Microsoft published legitimate apps that can be abused by attackers to bypass the security rules and to infects organizations network through living off the land attack methods. Living off is the method in which attackers use operating system features or
Malicious Attacks Cause of Most Aussie Breaches
Malicious or criminal attacks accounted for nearly twice as many data breaches as those resulting from human error during the first quarter of 2019, according to the Notifiable Data Breaches Quarterly Statistics Report by the Office of the Australian Information
Researchers have been monitoring the Korean-speaking threat actor known as ScarCruft and have reportedly discovered that new tools are being developed. According to Kaspersky Lab, ScarCruft is testing tools using code that can identify connected Bluetooth devices in order to
Yoroi Cyber Security Annual Report 2018 – In 2018 cyber-security experts observed an increased number of cyber attacks, malware endure to be the most aggressive and pervasive threat. For this reason, analyzing the last year occurred events would help cyber-security
WannaCry Remains a Global Threat Two Years On
WannaCry ransomware remains a global threat two years on from the initial outbreak of the attack in May 2017. That’s according to new analysis from Malwarebytes, which discovered that a total of 4,826,682 WannaCry detections have been identified since the
A vulnerability in a GPS tracker used by elderly people and kids could be exploited by an attacker to spy on individuals using it. Researchers at Fidus Information Security discovered a vulnerability in GPS trackers used by elderly people and
SMS Spammers Expose 80 Million Records Online
The administrators of an SMS spam operation left an unsecured MongoDB instance wide open online, exposing over 80 million records linked to their ‘leads,’ according to researchers. Bob Diachenko revealed the discovery in a blog post late last week, claiming
No one wants to believe they’d fall victim to a phishing attacks. However, phishing attacks are on the rise, and are more sophisticated than ever. There’s a good reason phishing attacks are touted as one of the most common security
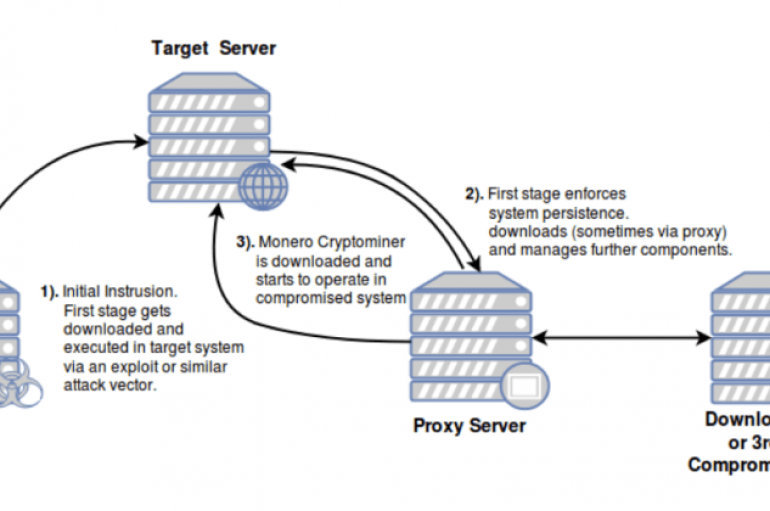
Two hacking groups associated with large-scale crypto mining campaigns, Pacha Group and Rocke Group, wage war to compromise as much as possible cloud-based infrastructure. The first group tracked as Pacha Group has Chinese origins, it was first detected in September
Talos security researchers discovered a Use After Free vulnerability in SQLite, allows attackers to send malicious SQL commands to trigger the vulnerability. The free vulnerability exists in the window function functionality of Sqlite3; the flaw can be tracked as CVE-2019-5018;
Hacking the ‘Unhackable’ eyeDisk USB stick
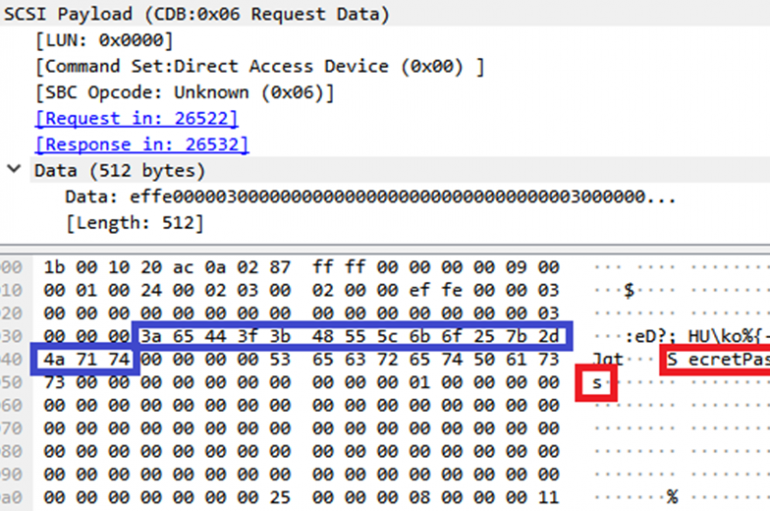
The paradox, the USB stick eyeDisk that uses iris recognition to unlock the drive could reveal the device’s password in plain text in a simple way. eyeDisk is a USB stick that uses iris recognition to unlock the drive, it
Equifax revealed its earnings release related to the security breach suffered in 2017, the incident has cost about $1.4 billion plus legal fees. Equifax revealed this week its earnings release related to the security breach suffered by the credit bureau
Security researcher Gjoko Krstic from Applied Risk discovered over 100 vulnerabilities that expose buildings to cyber attacks. Security researcher Gjoko Krstic from Applied Risk discovered over 100 vulnerabilities in management and access control systems from four major vendors. An attacker