Posts From CCME
Hackers Demand $5.3 Million After Locking Massachusetts City Computers With RYUK Ransomware
Cybercriminals compromise the New Bedford, Massachusetts city computers with the Ryuk Ransomware and demanding $5.3 million to unlock the compromised computers. July 5, 2019, City of New Bedford’s Management Information Systems (MIS) identified the ransomware that infected several computers. Soon
Unpatched Android Zero-day Vulnerability Let Hackers Escalate the Privilege and Take Control Of The Device
Researchers disclosed an unpatched Android zero-day vulnerability that allows local attackers to escalate the privilege and take control of the device. A high severity privilege vulnerability resides within the v4l2 driver which allows an attacker to leverage the lack of
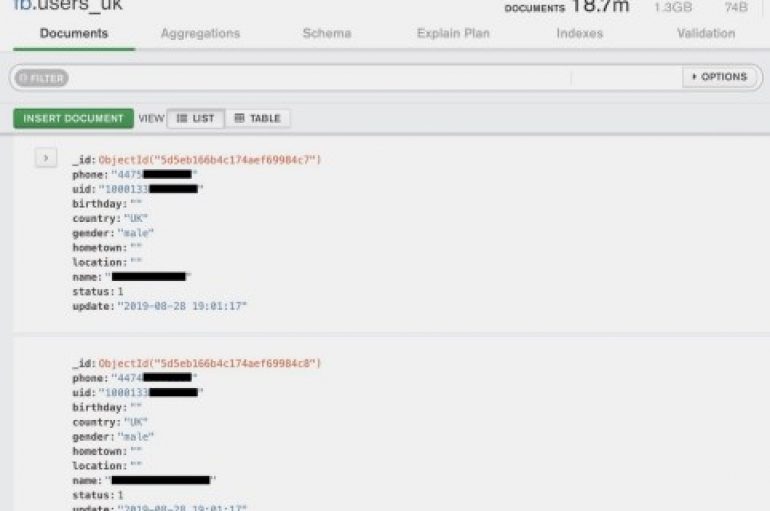
419 Million Facebook user accounts exposed online from an unsecured server that includes a unique Facebook ID and the phone number listed with the account. The details are exposed from the server that doesn’t have any password protection, the database
New Bedford Hit With $5.3m Ransomware Demand
A Massachusetts city has revealed that cyber-criminals tried to hold its data ransom to the tune of more than $5m over the summer, in a sign of the growing risk to organizations from online extortionists. The city of New Bedford
Google and YouTube have agreed to pay $170m to settle a case brought by the FTC and New York Attorney General alleging they illegally harvested personal data on children. The Children’s Online Privacy Protection Act (COPPA) requires online firms to
Hackers Remotely Control Email & Browser by Just Sending an SMS and Change the Settings Over the Air
Researchers discovered an advanced SMS phishing attack on some of the targeted Android phone’s that allows a remote attacker to trick victims in accepting the new settings and control the browser home page, Email server over the air. There are
In the first phase of architecturing the SOC, we have seen the basic level understanding of the attacks and necessary steps to breaking the Attack Chain. Let’s move on to the phases of SOC and advanced level of protecting the
An incident response plan is very essential for any organization to respond to the incident as quickly as possible. Here we have overviewed about how to respond to the cyber incident and the necessary action that needs to be taken.
New problems to Facebook, phone numbers associated with more than 400 million accounts of the social network giant were exposed online. A new privacy incident involved Facebook, according to TechCruch, phone numbers associated with 419 million accounts of the social
40% of IT Pros Would Outlaw Ransomware Payments
Research has revealed that 40% of IT security professionals think paying to retrieve data targeted by ransomware should be made illegal. The findings come from a survey of 145 security pros who visited AT&T’s booth at this year’s Black Hat
Research into insider threats has found that employees are so reticent to snitch on bosses they suspect are threat actors that senior staff are virtually immune from being reported. Researchers at Red Goat Cyber Security questioned 1,145 participants across a
Security flaws have been discovered in 600,000 GPS tracking devices intended to keep society’s most vulnerable members safe. Researchers at Avast Threat Labs found a number of vulnerabilities in 29 different device models commonly used to track the whereabouts of
Twitter opted to temporarily disable the feature that allows users to post tweets via SMS, in response to the hack of the CEO’s account. Twitter announced to temporarily disable the feature that allows users to post tweets via SMS, in
Immersive Labs Integrates MITRE ATT&CK Framework
A global cyber-skills training provider has become the first company to integrate its platform with the MITRE ATT&CK framework. Immersive Labs has mapped its training to the globally recognized knowledge base, which organizes and categorizes various types of tactics, techniques,
Experts warn of advanced phishing attacks in certain modern Android-based phones that can trick users into accepting new malicious phone settings. When users insert a new SIM in their mobile phone and access to the cellular network for the first
A bill intended to strengthen and modernize the cybersecurity of federal agencies will be introduced to the United States House of Representatives this week. The Advancing Cybersecurity Diagnostics and Mitigation Act would formally codify the dynamic Continuous Diagnostics and Mitigation