Posts From CCME
LED wristbands to light up large shows and events, it will be provided by event organizers to attendees, the wristbands are a part of lighting systems and it can be remotely controlled by DJ. RF remote controllers are the common
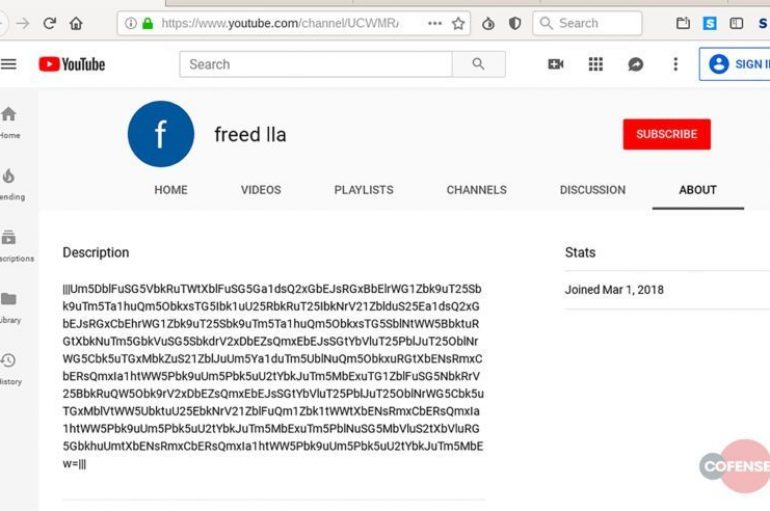
Cofense experts uncovered a new variant of the Astaroth Trojan that uses Facebook and YouTube in the infection process. Researchers at Cofense have uncovered a phishing campaign targeting Brazilian citizens with the Astaroth Trojan that uses Facebook and YouTube in
Web server pen testing performing under 3 major category which is identity, Analyse, Report Vulnerabilities such as authentication weakness, configuration errors, protocol Relation vulnerabilities. 1. “Conduct a serial of methodical and Repeatable tests “ is the best way to test
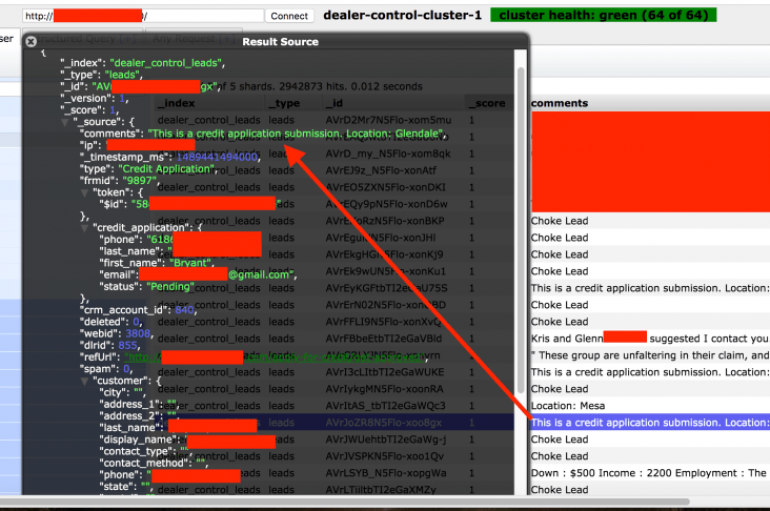
Researcher discovered an unsecured database exposed online, belonging to car dealership marketing firm Dealer Leads, containing 198 million records. The researcher Jeremiah Fowler discovered an unsecured database exposed online that belong to car dealership marketing firm Dealer Leads. The archive
A security researcher discovered a flaw in iOS 13 that allows bypassing the iPhone lock screen and access the victims to contact information without unlocking the device. Apple announced a release of iOS 13 during the company’s iPhone 11 event
A new cryptocurrency-miningbotnet tracked as WatchBog is heavily using the Pastebin service for command and control (C&C) operations. Cisco Talos researchers discovered a new cryptocurrency-mining botnet tracked as WatchBog is heavily using the Pastebin service for command and control. The
Speaking at 44CON, Pen Test Partners researchers Tony Gee and Vangelis Stykas demonstrated vulnerabilities in GPS trackers, which enabled them to call premium rate phone numbers, and possibly influence the outcome of television talent shows. Gee said that there is
Java is the programming language that is considered a favorite for both ethical and illegal hacking, according to Mehedi Hasan of Ubuntu Pit. It is commonly used to gain access through backdoor entries, much as hackers do with JavaScript. It
Marketer Exposes 198 Million Car Buyer Records
Another unprotected Elasticsearch database has been discovered by researchers, this time exposing personally identifiable information (PII) linked to 198 million car buying records. The privacy snafu was discovered back in August by Jeremiah Fowler, researcher at SecurityDiscovery. The non-password protected
An Iranian threat group exposed last year has been detected targeted hundreds of universities in over 30 countries in a global phishing operation. Cobalt Dickens has been linked to indictments last year against nine Iranian nationals who worked for the
Mirai and SMB Attacks Dominate 1H 2019
Attacks on IoT devices using Mirai and its variants and raids against the Windows SMB protocol dominated the first half of 2019, according to new data from F-Secure. The Finnish security vendor analyzed its global network of honeypots to find
Poland announced it will launch a cyberspace defense force by 2024 composed of around 2,000 soldiers with a deep knowledge in cybersecurity. The Polish Defence Ministry Mariusz Blaszczak has approved the creation of a cyberspace defence force by 2024, it
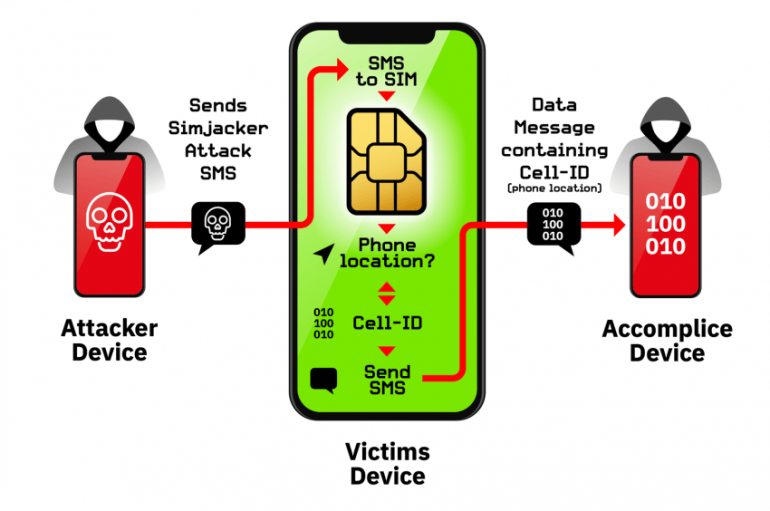
SimJacker is a critical vulnerability in SIM cards that could be exploited by remote attackers to compromise any phones just by sending an SMS. Cybersecurity researchers at AdaptiveMobile Security disclosed a critical vulnerability in SIM cards dubbed SimJacker that could
Ireland Hit by Pedophile Sextortion Email Scam
Residents of Ireland are being targeted by an aggressive email sextortion scam that accuses recipients of being pedophiles before threatening to expose them as such unless a ransom is paid. The scam was highlighted yesterday by the Irish arm of
A survey of 300 security professionals has found that 34% admit to bypassing security checks to bring products to market faster. The research was carried out by cyber assessment company Outpost24, which questioned attendees at the Infosecurity Europe Conference held
The United Nations (UN) children’s agency UNICEF has apologized after inadvertently leaking the personal data of users of its online learning platform, Agora. The leak occurred on August 26, when 20,000 Agora users were accidentally emailed a spreadsheet containing the