Posts From CCME
Eight years ago, a list of the world’s most dangerous software errors was published by problem-solving nonprofit the MITRE Corporation. Yesterday saw the long-awaited release of an updated version of this rag-tag grouping of cyber-crime’s most wanted. The Common Weakness
Vacationers Hit by Skimming Attack
People using mobile apps to book hotel rooms for their vacations have been targeted by a skimming attack. Research by cybersecurity company Trend Micro discovered that a series of incidents took place earlier this month in which the booking websites
Purchasing cyber insurance to protect your business from the ever-increasing number of threats will cost you more in Delaware than in any other US state. A new study by business insurer AdvisorSmith has found that the average cost of annual
Facebook has taken down hundreds of Facebook and Instagram Pages and accounts after two separate coordinated campaigns were discovered attempting to influence user behavior in Iraq and Ukraine. It’s possible that the fake news operations were an attempt to peddle
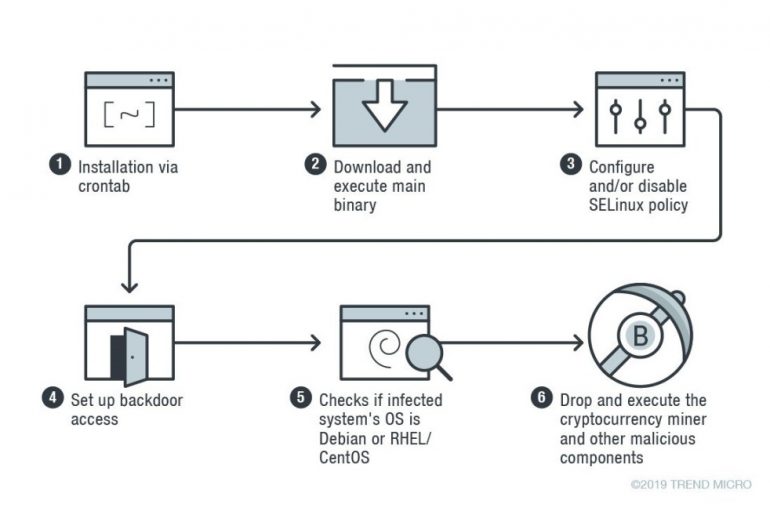
Researchers at Guardicore Labs reported that the Smominru botnet is rapidly spreading and now is already infecting over 90,000 machines each month around worldwide. In February 2018, researchers from Proofpoint discovered a huge botnet dubbed ‘Smominru’ that was using the
The Financial Services Information Sharing and Analysis Center (FS-ISAC) and Europol’s European Cybercrime Centre (EC3) have announced a partnership to combat cybercrime within the European financial services sector. The FS-ISAC is an industry consortium dedicated to reducing cyber-risk in the
The UK’s National Cyber Security Centre (NCSC) has been forced to issue a new report detailing the threat to the country’s universities from cyber-criminals and nation state operatives. The NCSC argued that, while the sector has traditionally been one of
WhatsApp introduced ‘delete for everyone’ feature last year. this is a quite life-saving feature which let you recall the message that you sent accidentally. Security Consultant Shitesh Sachan, noted that the feature was not working an intended with media files
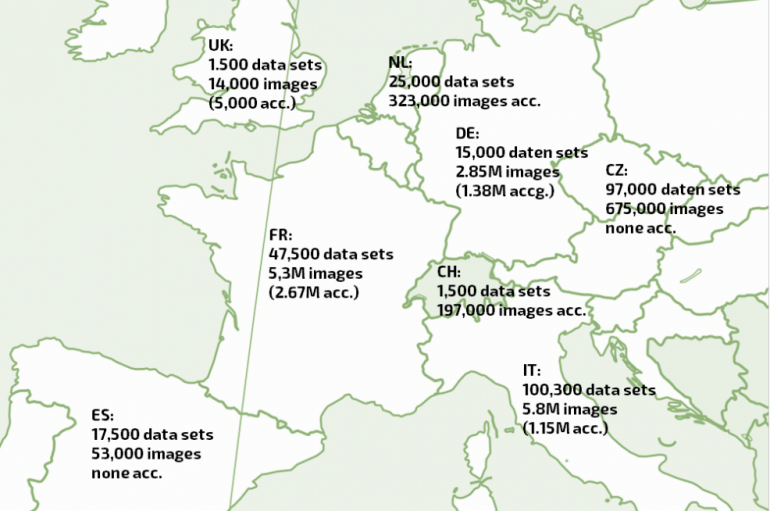
Researchers at Greenbone Networks vulnerability analysis and management company discovered 400 Million medical radiological images exposed online via unsecured PACS servers. The experts at Greenbone Networks vulnerability analysis and management company discovered 600 unprotected servers exposed online that contained medical
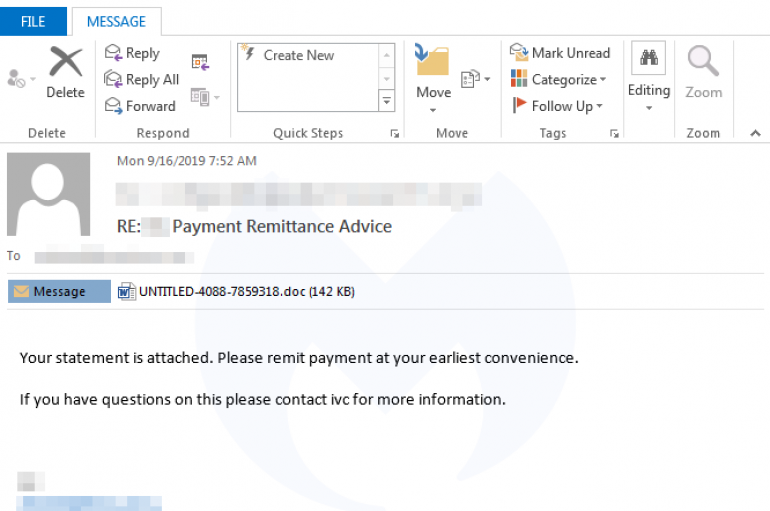
Emotet is back, its operators leverage a recently introduced spear-phishing technique to deliver their malware, they are hijacking legitimate email conversations. In 2019, security experts haven’t detected any activity associated with Emotet since early April, when researchers at Trend Micro
Lion Air Breach Hits Millions of Passengers
Tens of millions of passengers from at least two Asian airlines have had their personal data compromised after workers at the parent company left them exposed via an AWS server, it has emerged. Although it’s unclear how long the data
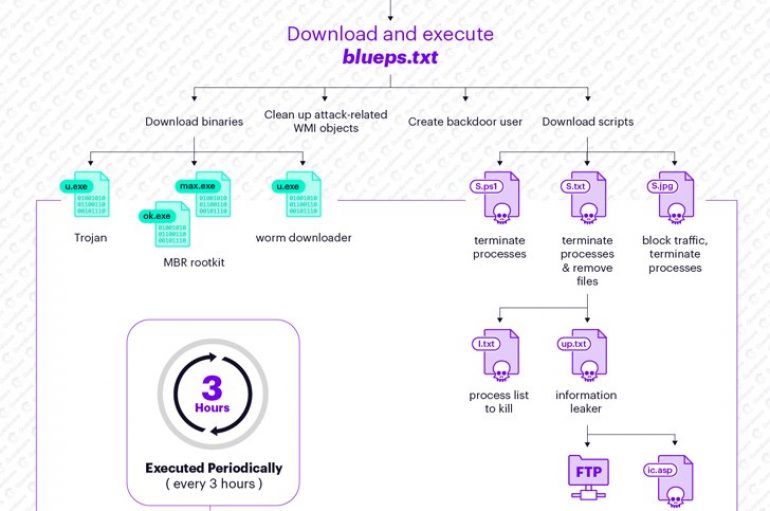
Trend Micro researchers spotted a piece of Linux cryptocurrency miner, dubbed Skidmap that leverages kernel-mode rootkits to evade the detection. Skidmap is a new piece of crypto-miner detected by Trend Micro that target Linux machines, it uses kernel-mode rootkits to
New Attack Group Targets Saudi IT Providers
A previously undocumented threat group has been mounting what appear to be supply-chain attacks against IT providers in the Middle East. Since July 2018, Tortoiseshell Group has targeted at least 11 organizations, using a deadly mix of custom-made and off-the-shelf
What is Spear Phishing Attack – A Complete Guide for Motives, Techniques & Prevention Methods
Each and Every day tens of thousands of Spear phishing emails are sending across the millions of victims around the world. Cyber-attacks have different pathways now, they can strike you from inside or outside, with equal damages across your network.
CWE Top 25 (2019) – List of Top 25 Most Dangerous Software Weakness that Developers Need to Focus
MITRE has released a list of Top 25 Most Dangerous Software Errors (CWE Top 25) that are widely spread and leads to serious vulnerabilities. The list was generated based on the vulnerabilities published within the National Vulnerability Database. These vulnerabilities
A follow-up study into the security of IoT devices has revealed more than twice the number of vulnerabilities as were detected six years ago. In the 2013 study SOHOpelessly Broken 1.0, researchers at Independent Security Evaluators (ISE) highlighted 52 vulnerabilities