Posts From CCME
Microsoft briefly exposed call center data on almost 250 million customers via several unsecured cloud servers late last year, according to researchers. Bob Diachenko spotted the major privacy snafu a day after databases across five Elasticsearch servers were indexed by
Security awareness training provider KnowBe4 has donated $250,000 to Stetson University College of Law, Florida’s first law school. The donation includes: Creation of the the KnowBe4 Cybersecurity Law Scholarship Fund which will provide $5000 merit-based scholarships for the next five
US military claims to have disrupted the online propaganda activity of the Islamic State (ISIS) in a hacking operation dating back at least to 2016. In 2016, the US Cyber Command carried out successful operations against the online propaganda of
16Shop – Malware-as-a-service Phishing Toolkit Attack PayPal Users With Anti-Detection Techniques
A prolific phishing kit distribution network dubbed “16Shop” believed to be active since 2018 and developed by a hacking group called the “Indonesian Cyber Army.” It’s a huge first attack targeting Apple kits and then attacked Amazon customers before the
Apple Dropped A Plan Let iPhone Users Have Fully Encrypt Backups On Their Devices Including WhatsApp Chats
Apple now officially dropped plans to let iPhone users have their device backup in an encrypted form in Apple’s iCloud service after the FBI complained. iCloud is an Apple cloud platform that allows Apple users to store and access their
A leading offshore safety and verification body has reported a rapid rise in the number of ships seeking to gain a cybersecurity classification. Ship classification society Bureau Veritas Marine & Offshore (BV) says it has seen a surge in the
An American businessman who co-founded a cybersecurity company has admitted to hiring criminals to carry out cyber-attacks against others. Tucker Preston, of Macon, Georgia, confessed to having paid threat actors to launch a series of distributed denial-of-service (DDoS) attacks between
Police Scotland has announced plans to establish “cyber kiosks” that will allow officers to scan locked smart devices for evidence. The 41 new kiosks will be located in police stations across local policing divisions, where they will be operated by
The US-based children’s clothing maker Hanna Andersson has disclosed a data breach that affected its customers. The US-based children’s clothing maker and online retailer Hanna Andersson discloses a data breach, attackers planted an e-skimmer on its e-commerce platform. Like other
Hong Kong is set to follow the lead of European regulators in applying tougher penalties for data protection infractions, following a serious breach at airline Cathay Pacific in 2018. Proposed amendments to the regional government’s Personal Data (Privacy) Ordinance, which
Zero-Day IE Bug is Being Exploited in the Wild
Both Microsoft and the US government are warning computer users of a critical remote code execution (RCE) vulnerability in Internet Explorer, which is currently being exploited in the wild. The zero-day bug, CVE-2020-0674, exists in the way the scripting engine
UK Gov Database Leak Exposes 28 Million Children
The UK government is facing urgent questions after it was revealed that betting companies were given access to a Department for Education (DfE) database containing personal information on 28 million children. Known as the Learning Record Service, the database stores
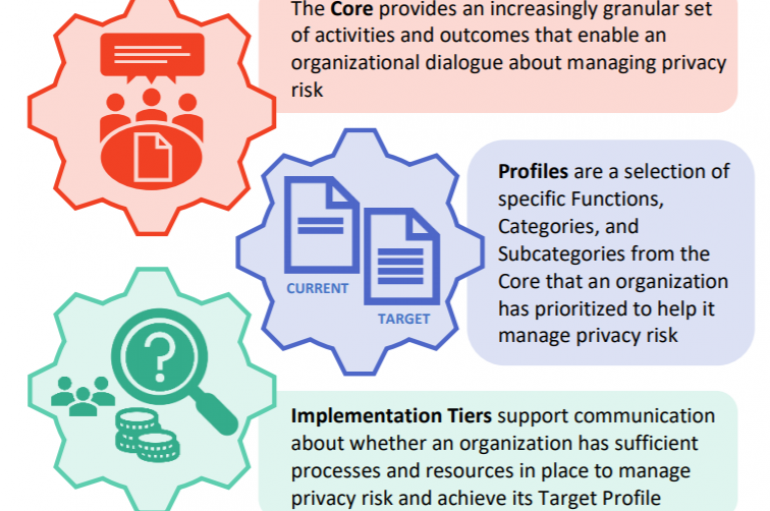
The NIST released version 1.0 of Privacy Framework, it is a tool designed to help organizations to manage privacy risks. The National Institute of Standards and Technology (NIST) has published the release version 1.0 of its privacy framework. The Framework
FTCODE Ransomware Attack Windows To Encrypt Files & Steals Stored Login Credentials From Browsers
Researchers discovered a new wave of FTCODE ransomware campaign that steal browsers login credentials and Encrypt files in Windows systems. FTCODE ransomware was first observed in 2013, it uses the Windows PowerShell program to perform file encryption. The ransomware resurfaced
CWE Top 25 (2019) – List of Top 25 Most Dangerous Software Weakness that Developers Need to Focus
MITRE has released a list of Top 25 Most Dangerous Software Errors (CWE Top 25) that are widely spread and leads to serious vulnerabilities. The list was generated based on the vulnerabilities published within the National Vulnerability Database. These vulnerabilities
Citrix Released Permanent Fixes for the Actively Exploited CVE-2019-19781 Flaw in ADC 11.1 and 12.0
Citrix released permanent fixes for CVE-2019-19781 Flaw in ADC 11.1 and 12.0, which would allow an unauthenticated remote attacker to execute arbitrary code on the vulnerable system. The vulnerability was discovered by Dmitry Serebryannikov from Positive Technologies and the severity